Table of Contents
ToggleHello everyone, welcome again to my new article based on transposition techniques in cryptography. In this, I will explain what transposition cipher is and what are its various techniques.
The purpose of writing this article is to clarify the concept of our readers on transposition cipher and its various techniques and how they can implement those techniques.
Transposition cipher
A transposition cipher is a method of encryption in which the positions of the letters in the plaintext are rearranged to create the ciphertext. It does not involve any substitution of letters, only the rearrangement of their positions. For example, if the plaintext is “HELLO” and the key is 2, the letters might be rearranged like this “LEHOL”.
Transposition techniques
The various types of transposition cipher are: –
- Rail fence technique
- Simple columnar transposition technique (SCTT)
- Vernam Cipher (One Time Pad)
- Book cipher/ Running key cipher
Rail fence technique
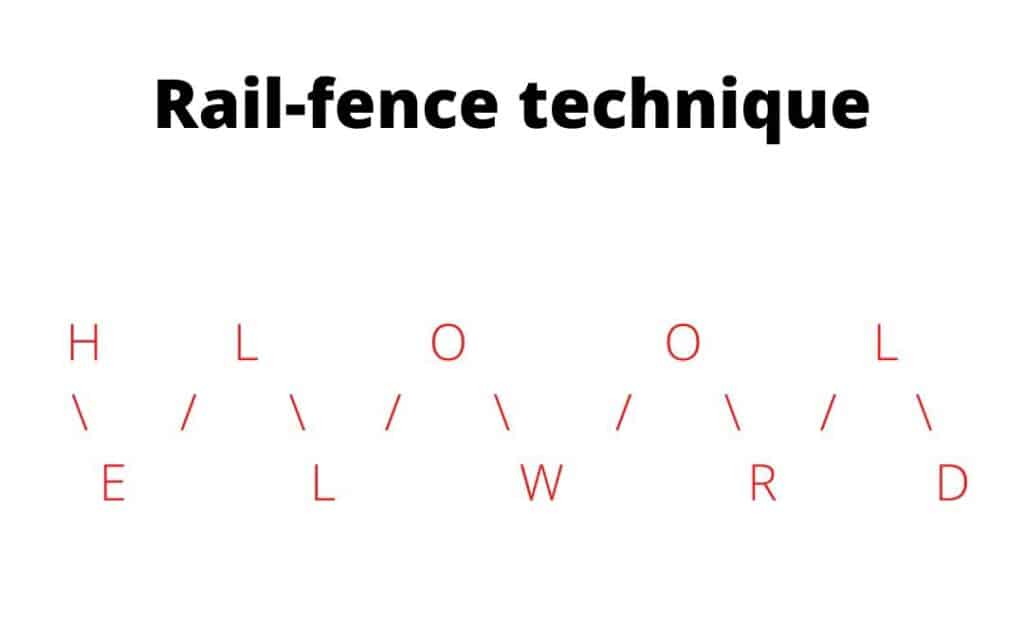
The rail fence technique is an example of a transposition cipher that involves rearranging the letters of a message by writing it in a zigzag pattern on a number of “rails.” The number of rails is usually equal to the key, and the message is written out in a pattern that follows the rails, going up and down as it moves from left to right.
In simple words first, we write plain text diagonally and then read it row-wise i.e. row by row for converting it into cipher text. For decrypting, the user should know the key.
Ex: – We take “HELLO WORLD” as our plain text which we had to convert into cipher text with the help of the rail fence technique.
After encryption, our plain text “HELLO WORLD” is converted into cipher text “HLOOLELWRD”.
Simple columnar transposition technique (SCTT)
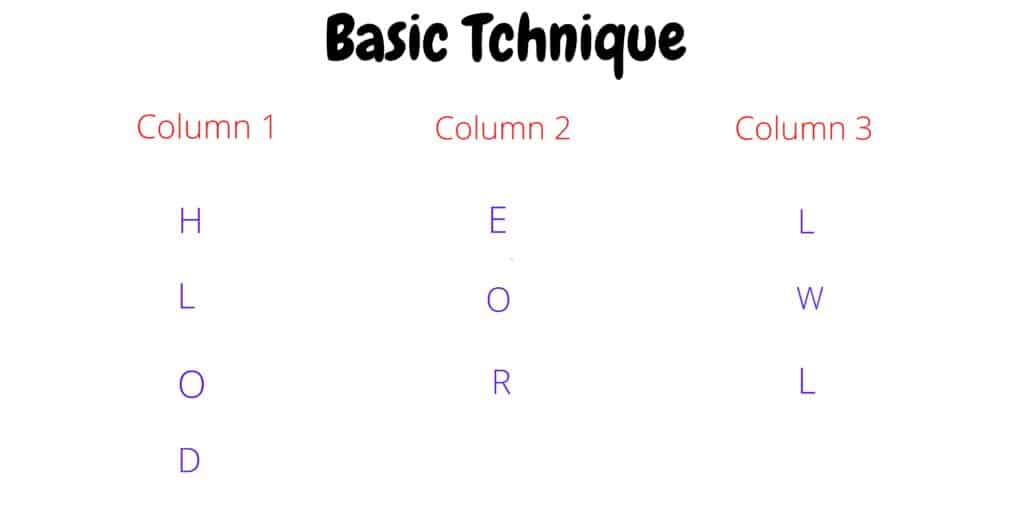
Simple columnar transposition is a technique used to encrypt a message by rearranging the order of the letters in the message. It involves writing the message out in a grid, with the columns being a certain width and the rows being a certain height. The message is then read out by taking the letters from each column in order, from top to bottom.
In this for converting plain text into cipher text first, we have to choose a fixed size of columns or column width. Then, we write the plain text message row-wise in selected columns. Then for creating cipher text read the message column wise i.e. column by column and before that, you have to choose the order of columns.
Ex: – We take “HELLO WORLD” as plain text which has to convert into cipher text. The order of columns will be 213.
Hence, the cipher text of plain text “HELLO WORLD” is “EORHLODLWL”.
Simple columnar transposition technique with multiple rounds
In simple columnar transposition techniques with multiple rounds for converting plain text into cipher text first, use the basic technique for deriving cipher text from the plain text “HELLO WORLD”. Now we write that derived cipher text again in columns of specific width and then follow the same steps we follow in the simple columnar transposition technique.
Ex: – First we convert “HELLO WORLD” into cipher text using a basic simple columnar transposition technique and the order of columns is 213.

Hence, our cipher text is “EORHLODLWL”. Now, we write this cipher text again columns of column width 3 and again convert it into cipher text by reading the letters column-wise with an order of column 312.

Now our final cipher text derived with multiple rounds is “OOWHDRLLEL”. We can also change the width of the column in the second round i.e., in this we use the width of column 3, so we can also use others like 2, 4, 5, etc.
Vernam Cipher (One Time Pad)
Vernam cipher, also known as a one-time pad, is a type of symmetric-key encryption algorithm in which a message is encrypted using a randomly generated key that is as long as the message itself. The key is used only once to encrypt the message and is then discarded.
The key is chosen randomly from a very large set of possible keys and is kept secret by both the sender and the receiver. The key is used to XOR the message with the key to produce the ciphertext. The resulting ciphertext can only be decrypted by XORing it with the same key that was used to encrypt it.
One of the main advantages of the Vernam cipher is that it is theoretically unbreakable, as long as the key is truly random and kept secret. However, in practice, it is difficult to generate truly random keys and keep them secure, which makes the Vernam cipher vulnerable to attacks.
The steps of vernam cipher are: –
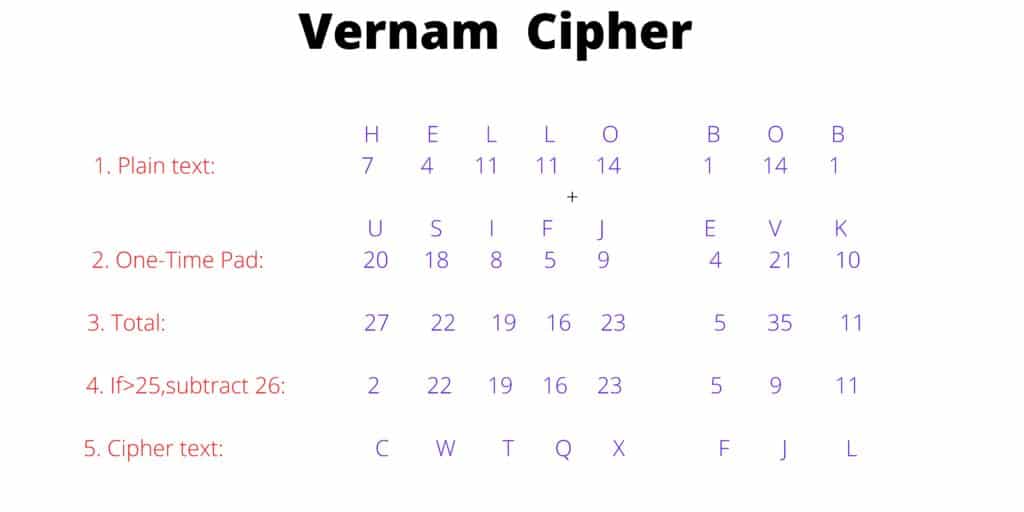
- First, we have to decide the plain text and write its ASCII code.
- Secondly, select a random code also known as a one-time pad whose size would be the same as the size of plain text, and convert it into its ASCII code.
- Now add the ASCII codes of both plain text and one-time pad.
- Subtract the sum by 26 which is greater than 25.
- And then convert those numbers or ASCII codes into alphabets assigned to that number.
For example, we take the plain text “HELLO BOB” and one-time pad “USIFJ EVK”. And after encryption derived cipher text is “CWTQXFJL”.
Book cipher/ Running key cipher
A book cipher, also known as a running key cipher, is a cipher in which the key is some long, pre-existing text, such as a book or article. The key is used to provide a very long sequence of numbers, which are then used as the keystream to encrypt the plaintext.
A book cipher, also known as a running key cipher, is a cipher in which the key is some long, pre-existing text, such as a book or article. The key is used to provide a very long sequence of numbers, which are then used as the keystream to encrypt the plaintext.
To encrypt a message using a book cipher, the sender and the recipient must both have a copy of the same book or article. The sender selects a page and a line from the book as the key and then uses the numbers corresponding to the letters on that line as the keystream.
For example, we take the key as “The quick brown fox jumps over the lazy dog” and the plain text message is “hello world”.
Follow the below steps for encryption of the message using book cipher: –
- Convert the key to numbers using a pre-agreed upon system, such as A=1, B=2, C=3, etc. In this case, the key becomes “20 8 5 17 21 3 15 16 6 18 9 14 19 7 15 18 11 4 15 3 5”.
- Convert the plaintext message to numbers using the same system. In this case, the plaintext becomes “8 5 12 12 15 23 15 18 12 4”.
- Add the keystream numbers to the plaintext numbers, modulo 26. This gives us the ciphertext “28 13 17 29 10 17 30 2 18”.
- Convert the ciphertext back to letters using the same system. In this case, the ciphertext becomes “ABQJADGEAI”.
Therefore, our required cipher text of plain text “hello world” is “ABQJADGEAI”.
Difference between substitution and transposition cipher
| Substitution Cipher | Transposition Cipher | |
| 1. | In this, we replace letters of plain text with other letters. | In this, we rearrange the letters of plain text. |
| 2. | It is easy to break. | It is tough to break. |
| 3. | It is easy to implement. | It is hard to implement. |
| 4. | It is less resistant to frequency analysis. | It is more resistant to frequency analysis. |
| 5. | Ex: – Caesar cipher, Hill cipher, etc. | Ex: – Vernam cipher, Rail-fence technique. |
If you have any queries regarding the above content, or you want to update anything in the content, then contact us with your queries. You can directly post your question in the group.
Connect with us on these platforms