DNS short for Domain Name System is a universal naming system used for linking a unique IP address with a unique domain name.
DNS is very important because there are millions of websites on the internet and every website is kept on a different server with a unique IP address for their identification and data flow over the internet.
Everyone who searches for any website only knows the website name, not their IP address and the server is only having an IP address attached to that data or website.

So for making the connection between the user and the website a silent process runs behind the browser and server which convert the domain name into an IP address and then the website is accessible by the user.
In simple terms, we can say that DNS is like a directory or phone book of the internet that stored all the domain names with their corresponding IP address.
DNS enables a user to access the website and other online resources by only searching their domain names instead of IP addresses.
Gathering DNS Information with tools
DNS short for domain name system is a hierarchical and decentralized naming system that translates domain names into IP addresses.
Every DNS consists of many things inside it for security and resolving purposes over the internet. these are DNS structure, IP address resolution, Authoritative DNS servers names, TTL (Time to live) details, Reverse DNS Data, and DNSSEC (DNS Security Extensions).
We will gather information by resolving DNS queries with the help of tools and services. Tools such as nslookup, Security Trails, and DNS Recon.
Let’s start with the nslookup tool
Gathering DNS information with NSlookup
NSlookup is a command-line utility that allows you to perform DNS queries to find information about a particular domain name or IP address.
It is commonly used to troubleshoot DNS issues, as it can provide information about the DNS records for a given domain, including the IP address and DNS server used for that domain.
In this article, we are using a Windows terminal for using this tool and if you want to do this practice on a Linux platform then you can go with our other article by [clicking here]
Let’s start with this tool
1. Open the Windows terminal and type the command [nslookup] and you’ll get your machine IP in response.
2. Now for gathering DNS information give the command nslookup and then set type=a and in the last give the domain name. Here the type a configures nslookup to query for the IP address of a given domain.
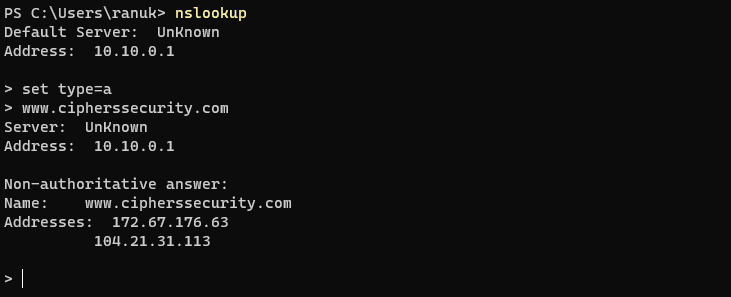
3. here we are getting non-authoritative answers from our query because the response is coming from the local machine’s server (google), but not from that server that legitimately hosts the domain www.google.com. now we need to find some authoritative name server from the domain.
4. Now we will set the type=cname and press enter. the cname will directly look for the domain’s authoritative name server and lists the CNAME records for a domain. and after that specify your target domain as google.com.
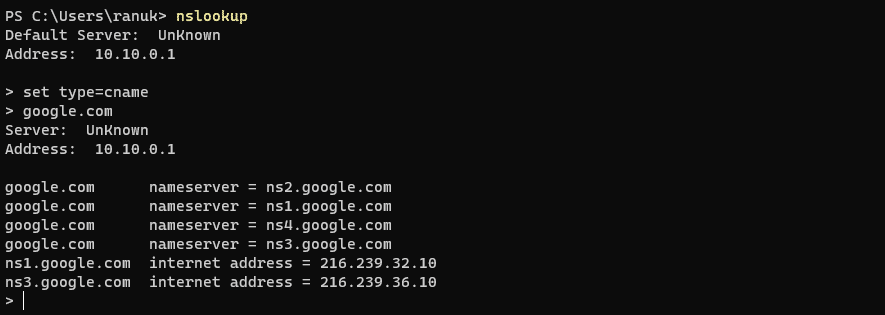
5. now here we are getting 4 domains’ authoritative nameservers (ns1.google.com, ns2.google.com, etc). As we got the nameserver of google.com now we will try to get IP address of the nameservers.
6. I am targeting [ns1.google.com] nameserver for querying its IP address. Set nslookup type=a and enter the nameserver address.

7. here we are getting details of the IP addresses of nameservers associated with google.com. authoritative nameserver stores the records associated with the domain.
8. This information like authoritative nameservers and IP addresses is very confidential because if any attacker determines this information then he/she might be able to exploit the server to perform attacks such as DoS, DDoS, URL Redirection, etc.
9. We can perform these operations by using nslookup online version only from the browser. So now we will use the online tool NSLOOKUP to gather DNS information about the target domain.
10. Access the nslookup website from here [nslookup] and enter the domain of your choice and select the query you want to execute with the domain and press enter. here I am using google.com as my target domain and selecting default type-a query for finding DNS servers.
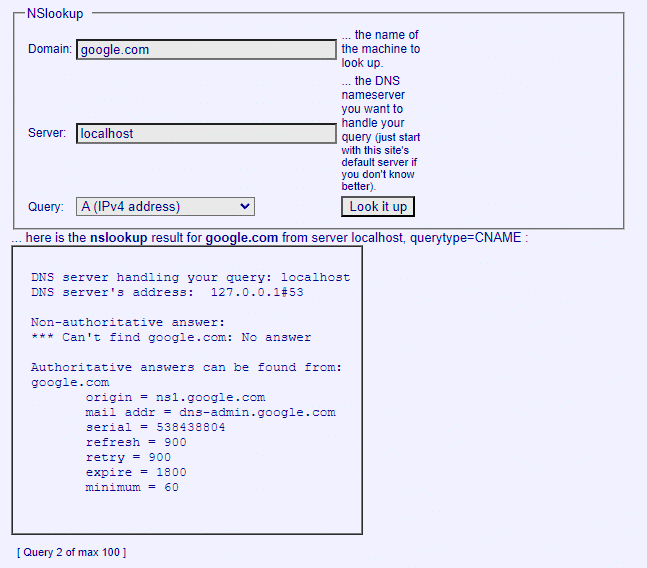
11. Now go with any other query, so this time I will choose AAAA query from the list and my target domain will be the same and press enter.
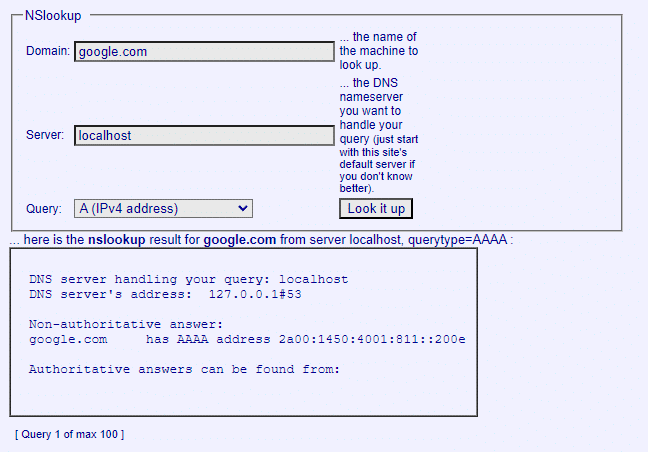
12. This will show the result you want. Online version is the same as command line version you can use anyone of them. Both will give you same and accurate result for your query.
Performing reverse DNS Lookup with tools
Performing reverse DNS lookup means we need to gather domain name information from any known IP address. It is totally opposite of DNS lookup because there we’re gathering information about IP address from any give domain name.
In this Reverse DNS lookup we will use tools such as Reverse IP domain check and DNS Recon
So first we are going to use you get signal‘s Reverse IP domain check online tool to find the other domains/sites that share the same web server as our target server.
And we will also perform a reverse DNS lookup using DNSRecon on IP range in an attempt to locate a DNS PTR record for those IP addresses.
1. first navigate to the website of you get signal [click here]. Then click on Reverse IP Domain Check.
2. Now for reverse DNS lookup enter the target domain address in the remote address box and click on the check button.
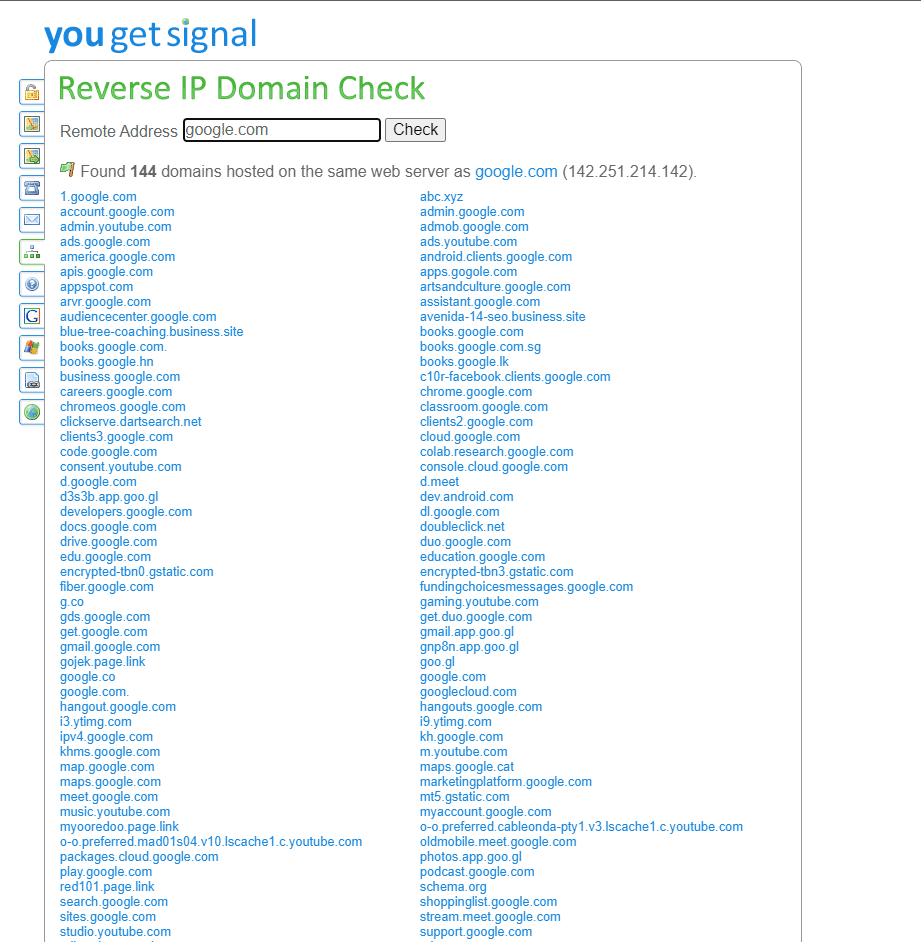
3. here we are getting the list of domain name that is hosted on the same server as google.com hosted, as shown in the screenshot.
4. Now we will use DNSRecon tool for reverse DNS lookup
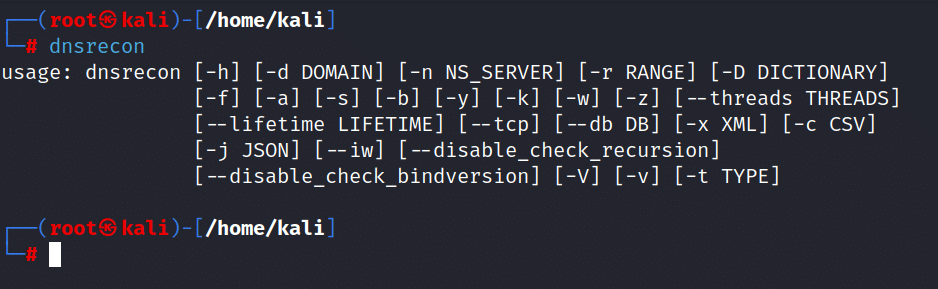
5. Open Kali Linux machine terminal and type [dnsrecon]. now if it is installed it will show up you the options of dnsrecon tool. as shown in the screenshot below.
6. now give the command for locating DNS PTR record for IP addresses between 142.251.46.0-142.251.46.255. [dnsrecon -r 142.251.46.0-142.251.46.255]
Note:- here -r specifies the range of IP addresses and the IP addresses is obtained from the previous step in reverse DNS with you get signal online tool.
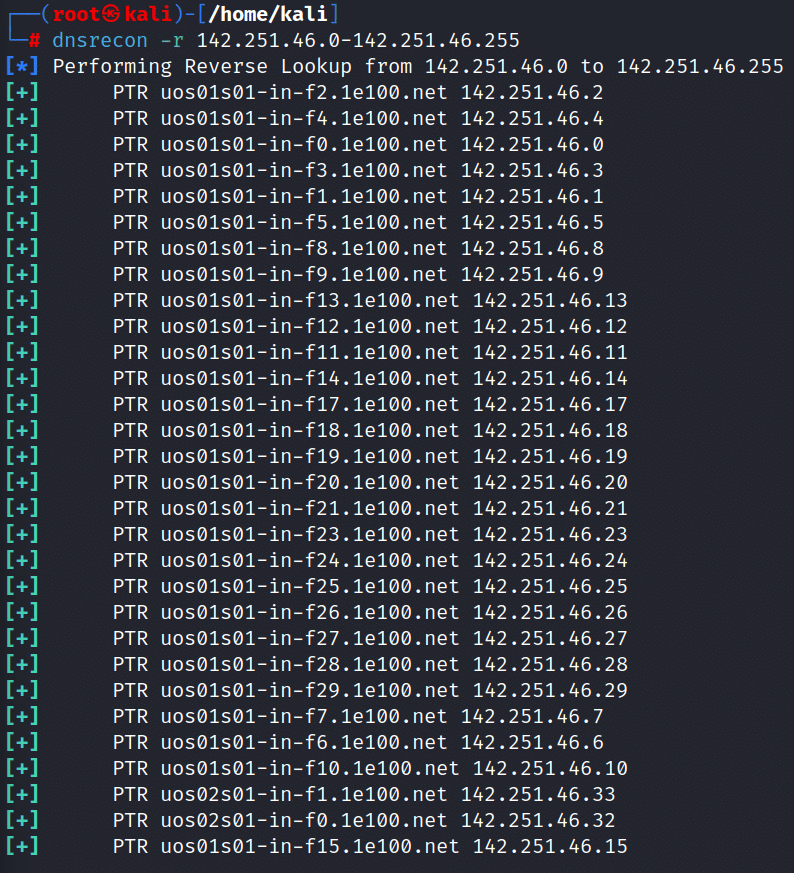
7. This is the demonstration of gathering information about a target organization by performing reverse DNS lookup using “you get signal” reverse IP Domain Check and DNSRecon tool.
keywords:- DNS, Reverse DNS, Domain name, IP address, nslookup, DNSRecon, Kali Linux