This room is the third in the (Nmap Advanced Port Scans) Nmap series (part of the Introduction to Network Security module). In the first two rooms, we learned about live host discovery and basic port scans.
In Nmap Basic Port Scans, we covered TCP flags and reviewed the TCP 3-way handshake. To initiate a connection, TCP requires the first packet to have the SYN flag set. Consequently, we can tell if a TCP port is open based on the response we receive.
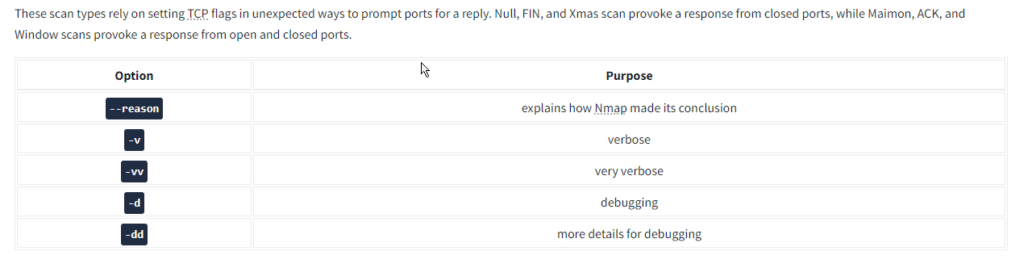
Security researchers and hackers contemplated the TCP flags, shown in the figure below and explained in the previous room, and started to experiment. They wanted to know what would happen if we send a TCP packet, which is not part of any ongoing TCP connection, with one or more flags set.

For instance, an ACK flag is set when you want to acknowledge received data. An ACK scan is like trying to acknowledge data that was neither sent nor received in the first place. Consider this simple analogy, someone coming to you out of nowhere to tell you, “yes, I hear you, please continue.” when you haven’t said anything.
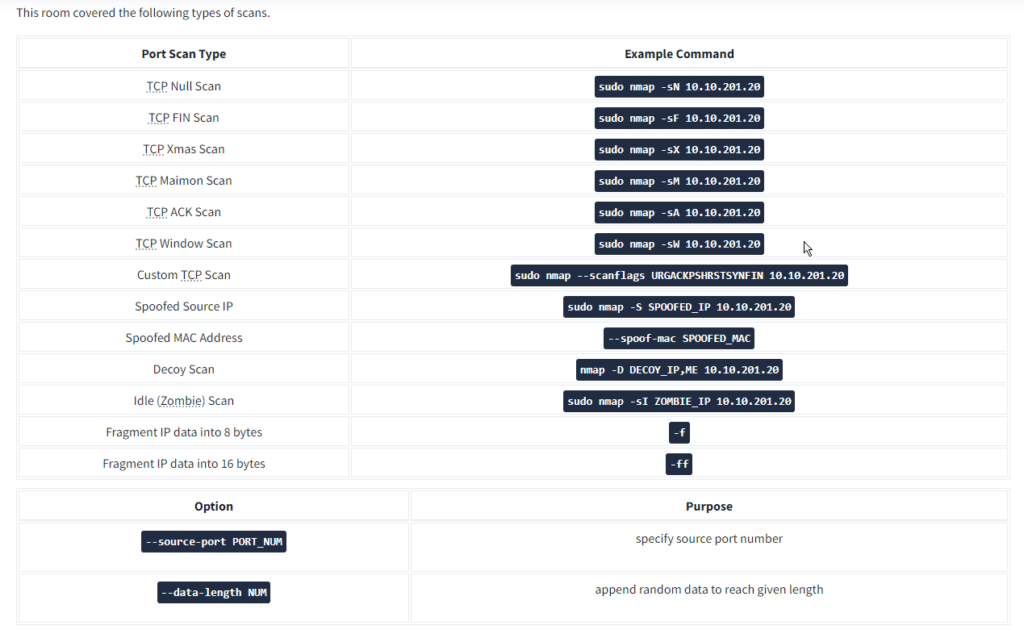
This room explains advanced types of scans and scan options. Some of these scan types can be useful against specific systems, while others are useful in particular network setups. We will cover the following types of port scans:
- Null Scan
- FIN Scan
- Xmas Scan
- Maimon Scan
- ACK Scan
- Window Scan
- Custom Scan
Moreover, we will cover the following:
- Spoofing IP
- Spoofing MAC
- Decoy Scan
- Fragmented Packets
- Idle/Zombie Scan
We will discuss options and techniques to evade firewalls and IDS systems. We also cover options to get more verbose details from Nmap.
Task 2 TCP Null Scan, FIN Scan, and Xmas Scan nmap advance
Question: In a null scan, how many flags are set to 1?
Answer: 0
Question: In a FIN scan, how many flags are set to 1?
Answer: 1
Question: In a Xmas scan, how many flags are set to 1?
Answer: 3
Question: Start the VM and load the AttackBox. Once both are ready, open the terminal on the AttackBox and use nmap to launch a FIN scan against the target VM. How many ports appear as open|filtered?
Answer: 7
Question: Repeat your scan launching a null scan against the target VM. How many ports appear as open|filtered?
Answer: 7
Task 3 Maimon Scan nmap advance
Question: In the Maimon scan, how many flags are set?
Answer: 2
Task 4 TCP ACK, Window, and Custom Scan nmap advance
Question: In TCP Window scan, how many flags are set?
Answer: 1
Question: You decided to experiment with a custom TCP scan that has the reset flag set. What would you add after --scanflags?
Answer: RST
Question: The VM received an update to its firewall ruleset. A new port is now allowed by the firewall. After you make sure that you have terminated the VM from Task 2, start the VM for this task. Launch the AttackBox if you haven’t done that already. Once both are ready, open the terminal on the AttackBox and use Nmap to launch an ACK scan against the target VM. How many ports appear unfiltered?
Answer: RST
Question: What is the new port number that appeared?
Answer: 443
Question: Is there any service behind the newly discovered port number? (Y/N)
Answer: N
Task 5 Spoofing and Decoys Port nmap advanceScans
Question: What do you need to add to the command sudo nmap MACHINE_IP to make the scan appear as if coming from the source IP address 10.10.10.11 instead of your IP address?
Answer: -S 10.10.10.11
Question: What do you need to add to the command sudo nmap MACHINE_IP to make the scan appear as if coming from the source IP addresses 10.10.20.21 and 10.10.20.28 in addition to your IP address?
Answer: -D 10.10.20.21,10.10.20.28,ME
Task 6 Fragmented Packets nmap advance
Question: If the TCP segment has a size of 64, and -ff option is being used, how many IP fragments will you get?
Answer: 4
Task 7 Idle/Zombie Scan nmap advance
Question: If the TCP segment has a size of 64, and -ff option is being used, how many IP fragments will you get?
Answer: -sI 10.10.5.5
Task 8 Getting More Details nmap advance
Question: Launch the AttackBox if you haven’t done so already. After you make sure that you have terminated the VM from Task 4, start the VM for this task. Wait for it to load completely, then open the terminal on the AttackBox and use Nmap with nmap -sS -F --reason 10.10.201.20 to scan the VM. What is the reason provided for the stated port(s) being open?
Answer: syn-ack