Network Footprinting is gathering information about the target network to find network vulnerabilities, network infrastructure, and network security of the victim’s network.
This information will help the attacker for better attacks and understand the victim’s network. The information about the network includes IP address, Hostname, Domain name, network range, IP classification, etc.
Network Footprinting will help an attacker/ethical hacker to draw a network diagram and analyze the target network in more detail to perform advanced attacks.
Let’s start network footprinting by finding the network range of the target network system.
Finding Network Range
A map of the target network can be made with the use of network range information.
The network range can be used to learn more about the network’s topology and which computers are active inside it.
Additionally, knowing the network topology and having access to the target network’s operating system and control system can both be useful.
First, we will use the ARIN Whois database search tool for finding and locating the target network range.
1. First navigate to the ARIN website from here [ARIN Whois Database]
2. Now the ARIN website will appear then enter the IP address of your target organization network. In my case, I was using Microsoft.com as my target organization and its IP address will be [20.81.111.85]. You can get the IP address by using the nslookup tool.
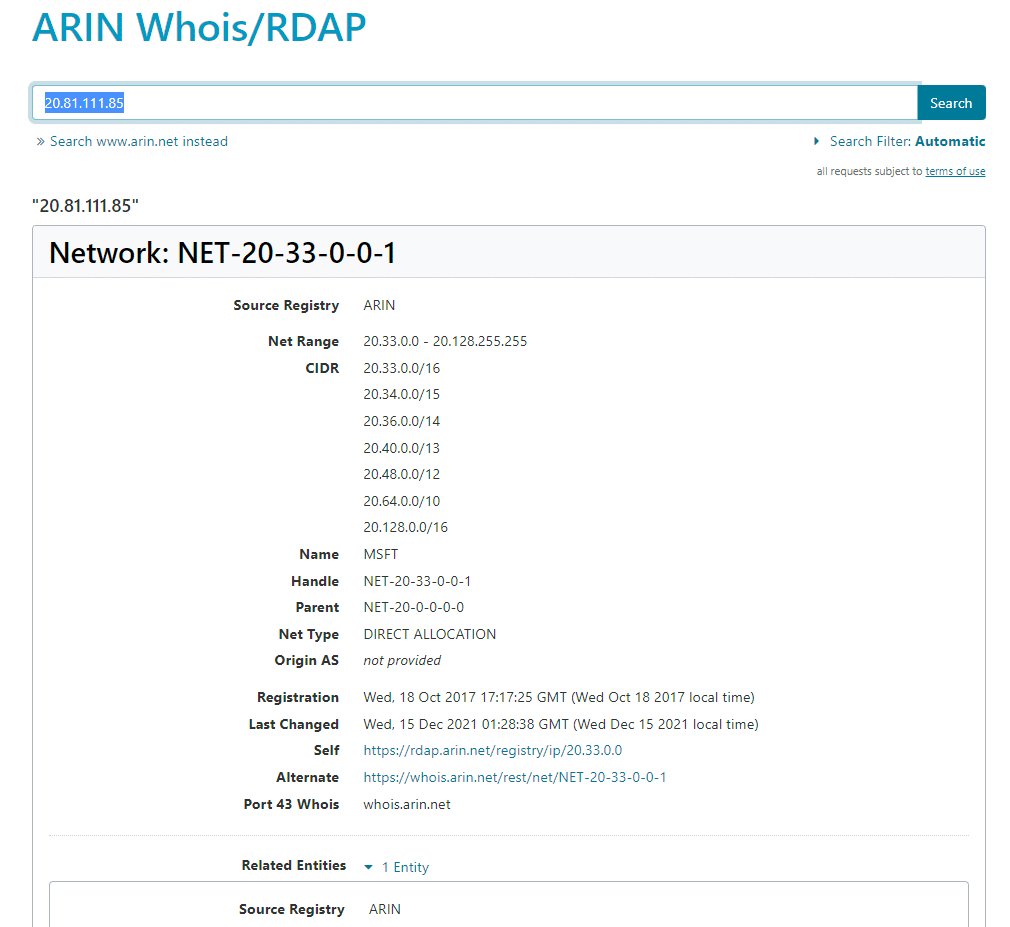
Now after searching you will get the network range information and other information such as network type, registration information, DNS, etc.
This is how you can use ARIN for finding network ranges and other information related to a target network system.
Network Trace Routing in Windows
The network packet’s route is the journey it takes to get from its source to its destination. The technique of locating the hosts and routes between a source and a destination is known as network trace routing or network footprinting.
Using network trace routing, you may map the organization’s network topology by getting crucial details such as the IP addresses of the hosts that are located between the source and destination.
You can use Traceroute to gather data on the topology of your network, the locations of firewalls, trustworthy routers, and other things.
Now we will see how to perform network trace routing with Windows OS. Here I am choosing to testfire.net as my target organization.
1. Open Command or Windows terminal and type [tracert www.testfire.net] after it will start finding hops between the destination source IP for the communication.
2. for Seeing other different options in the tracert type [tracert /?]
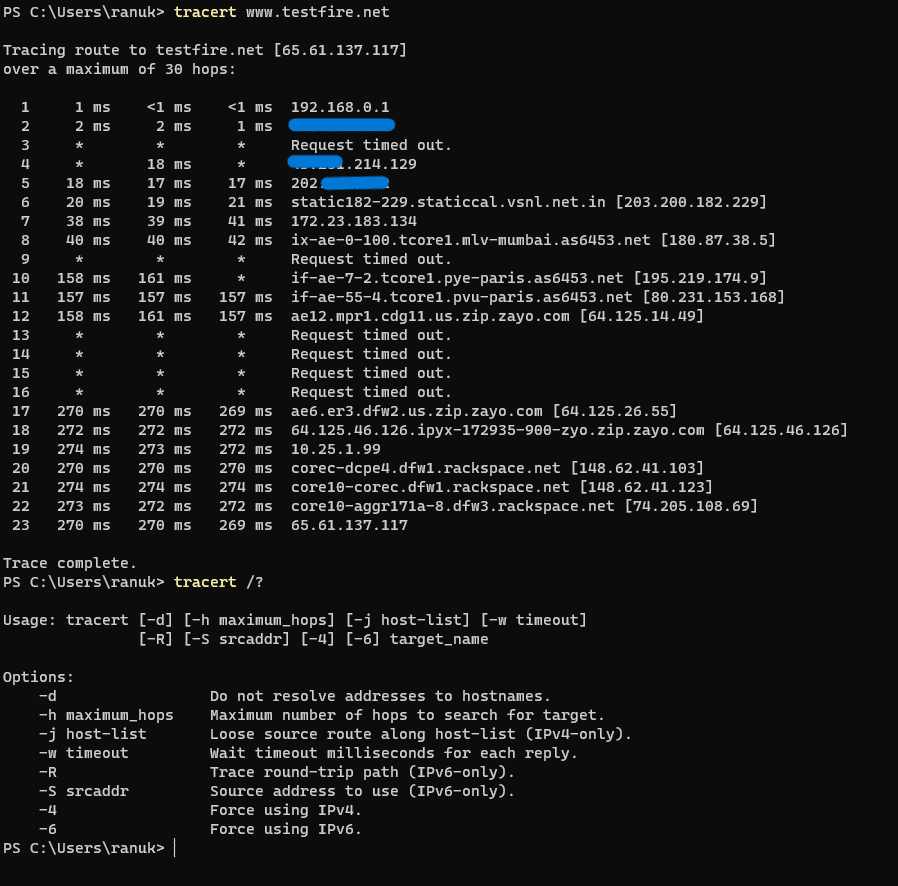
3. The above screenshot is the result of our query now we will try some options with the query for better and more accurate results.
4. Now give the command as [tracert -h 5 www.testfire.net] and press enter. now here we are limiting the maximum hops for our network route to 5.
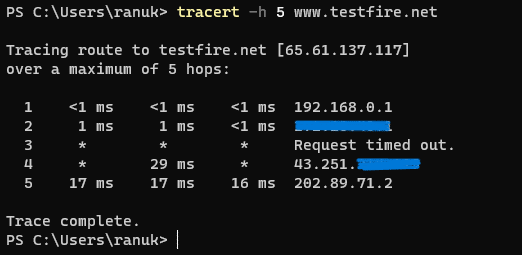
5. this is how we can use options in the tracert tool in Windows. tracert will help in finding routes for the packets going to their destination.
Network Trace Routing in Linux
The process and concept for trace routing are the same for Windows and Linux with just a difference of tools and commands. here I am using Kali Linux to perform this trace routing or network footprinting.
1. Open Kali Linux or any Linux machine you have and there open the Linux Terminal.
2. In the terminal first type the command as [traceroute] for checking whether the traceroute is installed or not. If it is installed then it will so up the options and help for the traceroute tool. as shown in the screenshot below
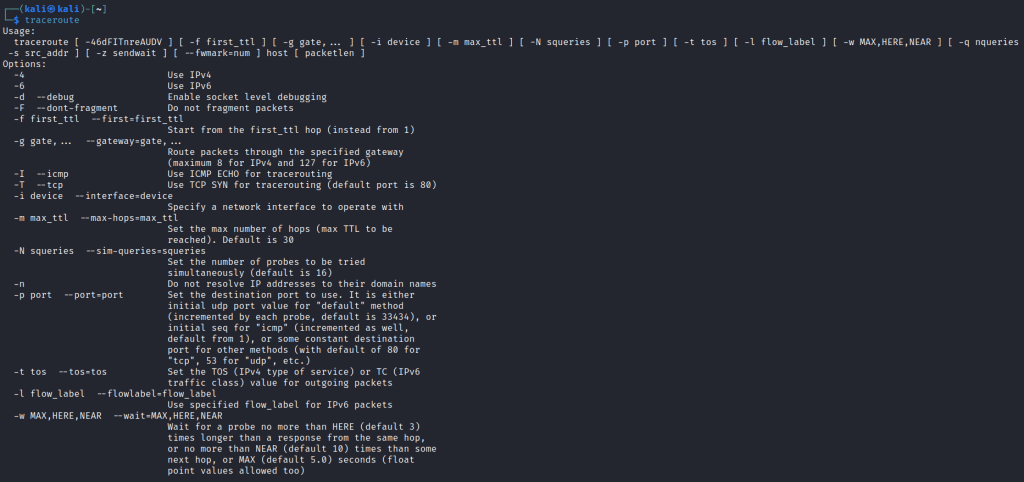
3. Now we will use the traceroute tool for tracing the packet’s routes for reaching their destination to the server. for this, I am targeting testfire.net and going to trace the route of the packets for reaching the testfire.net server.
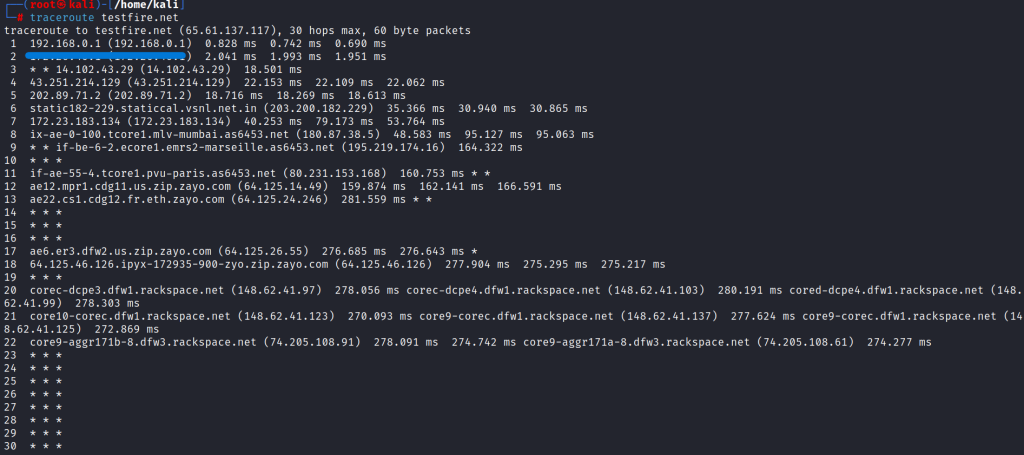
4. Here we are seeing all the hops we are going through for reaching the destination server over the network. This is how we can see all the routers and servers between the sender and receiver server and can draw a network diagram for further attacks on that network.
5. There are several more tools available in Linux for trace routing and network footprinting:-