Hello there, today we are going to discuss some of the best information-gathering tools used for gathering information from other sources. I am not ranking them but showing you guys how they work and why I chose them as the best tools, but I didn’t give them any ranking that this is top or down. you can decide what tools are giving you the best-gathered information and rank them as your wise list.
Let me clear you guys in this article we will discuss many things like what is information gathering, what to do with the gathered information, how gathering information helps us to understand targets, and what types of attacks we can do with the gathered information.
this article was created in the context of my own experience with cybersecurity. this will help you in gathering information about someone by using tools on Linux and then find bugs in their system with that information.
Tools for Information Gathering
There are many tools available for gathering different types of information for different types of attacks. But here we will discuss some common tools and their techniques to gather more useful information about your target. And the tools we are going to discuss will help you with passive information gathering of someone’s individual or organization.
We will discuss here some system tools and some online tools to gather information
Tools for information gathering are
- nslookup
- theHarvester
- Knockpy
- Maltego
Online tools to gather information are
- whois domain tools
- Netcraft
- Who.is
- robtex
Information gathering with nslookup
nslookup is a command-line tool that is used for querying the Domain Name System (DNS) to obtain domain name or IP address mapping or for any other specific DNS record. It is available on most operating systems, including Windows, macOS, and Linux.
nslookup can gather 3 types of information for you, the IP address of the Domain, nameserver details of the domain, and mail server details of the domain.
for getting the IP address of any domain
nslookup [domain-name]To find the IP address of the domain name “example.com”, you would type nslookup example.com and press enter. The nslookup tool will then query the DNS and display the corresponding IP address on the screen.
Example:-
└─$ nslookup testfire.net
Server: 10.0.2.3 || your machine IP
Address: 10.0.2.3#53 || your address
Non-authoritative answer:
Name: testfire.net
Address: 65.61.137.117 || IP of testfire.net└─$ nslookup testphp.vulnweb.com
Server: 10.0.2.3 || your machine IP
Address: 10.0.2.3#53 || your address
Non-authoritative answer:
Name: testphp.vulnweb.com
Address: 44.228.249.3 || IP of testphp.vulnweb.comNow here we’re getting the IP address of testfire.net (domain) as 65.62.137.117 and in the above, the IP address 10.0.2.3 is of our Kali machine so don’t get confused with both IPs. Here we are using nslookup to resolve the IP address of any domain.
For getting nameserver details of any domain
nslookup -type=ns [domain-name]To find the name server of the particular domain name “example.com” you would type nslookup -type=ns and press enter. This will return the nameserver details for the specified domain. For example, if you want to get the nameserver details for the domain testfire.net, you would use the following command:
└─$ nslookup -type=ns testfire.net
Server: 10.0.2.3
Address: 10.0.2.3#53
Non-authoritative answer:
testfire.net nameserver = usc3.akam.net.
testfire.net nameserver = asia3.akam.net.
testfire.net nameserver = ns1-99.akam.net.
testfire.net nameserver = eur2.akam.net.
testfire.net nameserver = ns1-206.akam.net.
testfire.net nameserver = usw2.akam.net.
testfire.net nameserver = usc2.akam.net.
testfire.net nameserver = eur5.akam.net.
Authoritative answers can be found from:
eur2.akam.net internet address = 95.100.173.64
eur5.akam.net internet address = 23.74.25.64
usc2.akam.net internet address = 184.26.160.64
usc3.akam.net internet address = 96.7.50.64
usw2.akam.net internet address = 184.26.161.64
asia3.akam.net internet address = 23.211.61.64
ns1-99.akam.net internet address = 193.108.91.99
ns1-99.akam.net has AAAA address 2600:1401:2::63
ns1-206.akam.net internet address = 193.108.91.206
ns1-206.akam.net has AAAA address 2600:1401:2::ce Attacks with exposed nameserver details
Having the nameserver details for a domain exposed can potentially allow an attacker to perform various types of attacks. For example, an attacker may be able to use the nameserver details to:
- Perform DNS spoofing attacks, where they can redirect traffic intended for the target domain to a different server that they control. This can allow the attacker to steal sensitive information, such as login credentials, or to serve malicious content to users who visit the target domain.
- Launch a distributed denial of service (DDoS) attack, where the attacker sends a large volume of traffic to the nameservers in an attempt to overwhelm them and make the target domain unavailable.
- Conduct DNS cache poisoning attacks, where the attacker modifies the DNS records in the cache of a nameserver in order to redirect traffic intended for the target domain to a different server that they control. This can allow the attacker to serve malicious content to users who visit the target domain.
- Perform a Zone transfer attack, where an attacker who is able to perform a successful zone transfer can gain access to the DNS records for a domain, which may include sensitive information such as the IP addresses of the servers that host the domain.
For getting mail server details of any domain
nslookup -type=mx [domain-name]To find the mail server of the particular domain name “example.com” you would type nslookup -type=mx and press enter. This will return the mail server details for the specified domain. For example, if you want to get the mail server details for the domain, example.com, you would use the following command:
└─$ nslookup -type=mx gmail.com
Server: 10.0.2.3
Address: 10.0.2.3#53
Non-authoritative answer:
gmail.com mail exchanger = 5 gmail-smtp-in.l.google.com.
gmail.com mail exchanger = 10 alt1.gmail-smtp-in.l.google.com.
gmail.com mail exchanger = 30 alt3.gmail-smtp-in.l.google.com.
gmail.com mail exchanger = 40 alt4.gmail-smtp-in.l.google.com.
gmail.com mail exchanger = 20 alt2.gmail-smtp-in.l.google.com.
Authoritative answers can be found from:
gmail.com nameserver = ns1.google.com.
gmail.com nameserver = ns3.google.com.
gmail.com nameserver = ns2.google.com.
gmail.com nameserver = ns4.google.com. Attacks with exposed Mail records details
There are several potential attacks that a malicious actor could perform with access to exposed email records. Here are a few examples:
- Spamming: The attacker could use the email addresses to send large volumes of spam or phishing emails. This could inundate the victims’ inboxes with unwanted messages and potentially trick them into divulging sensitive information.
- Spear phishing: The attacker could use the information in the email records to craft targeted phishing emails that appear to come from a trusted source. This could make the emails more convincing and increase the likelihood of victims falling for the scam.
- Social engineering: The attacker could use the information in the email records to try to gain the trust of the victims and then trick them into divulging sensitive information. This could be done through email, phone, or in-person interactions.
- Identity theft: The attacker could use the information in the email records to steal the victims’ identities and commit financial fraud or other crimes.
- SMTP open relay: An SMTP open relay is a type of vulnerability in an email server that allows unauthorized users to send messages through the server. This is a serious security issue because it can be exploited by attackers to send spam or phishing emails, potentially on a large scale.
Information gathering with theHarvester tool
theHarvester is a popular open-source tool used for information gathering and reconnaissance in the initial phase of a penetration testing or red teaming engagement. It can be used to gather email addresses, subdomains, and hostnames related to a specific domain. This information can then be used to identify potential targets and vulnerabilities in the organization’s network.
It can be used to gather various types of information related to a specific domain, including:
- Email addresses: theHarvester can search public sources such as search engines and social media networks to find email addresses associated with the target domain.
- Subdomains: theHarvester can use DNS records and other public sources to identify subdomains of the target domain.
- Hostnames: theHarvester can use DNS records and other public sources to identify hostnames associated with the target domain.
- IP addresses: theHarvester can use DNS records and other public sources to identify IP addresses associated with the target domain.
Basic Syntax for information gathering with theHarvester
theharvester -d [domain] -b [source] -l [limit] -f [file]
theHarvester -d [domain] -l [limit] -S[start from port\dns]
Check That theHarvester tool is installed or not by running these command
└─$ theHarvester
*******************************************************************
* _ _ _ *
* | |_| |__ ___ /\ /\__ _ _ ____ _____ ___| |_ ___ _ __ *
* | __| _ \ / _ \ / /_/ / _` | '__\ \ / / _ \/ __| __/ _ \ '__| *
* | |_| | | | __/ / __ / (_| | | \ V / __/\__ \ || __/ | *
* \__|_| |_|\___| \/ /_/ \__,_|_| \_/ \___||___/\__\___|_| *
* *
* theHarvester 4.2.0 *
* Coded by Christian Martorella *
* Edge-Security Research *
* cmartorella@edge-security.com *
* *
*******************************************************************
usage: theHarvester [-h] -d DOMAIN [-l LIMIT] [-S START] [-p] [-s] [--screenshot SCREENSHOT] [-v]
[-e DNS_SERVER] [-r] [-n] [-c] [-f FILENAME] [-b SOURCE]
theHarvester: error: the following arguments are required: -d/--domain
Let’s try it by giving a random target to it:-
└─$ theHarvester -d testfire.net -b bing -l 200
*******************************************************************
* _ _ _ *
* | |_| |__ ___ /\ /\__ _ _ ____ _____ ___| |_ ___ _ __ *
* | __| _ \ / _ \ / /_/ / _` | '__\ \ / / _ \/ __| __/ _ \ '__| *
* | |_| | | | __/ / __ / (_| | | \ V / __/\__ \ || __/ | *
* \__|_| |_|\___| \/ /_/ \__,_|_| \_/ \___||___/\__\___|_| *
* *
* theHarvester 4.2.0 *
* Coded by Christian Martorella *
* Edge-Security Research *
* cmartorella@edge-security.com *
* *
*******************************************************************
[*] Target: testfire.net
Searching 0 results.
[*] Searching Bing.
[*] No IPs found.
[*] No emails found.
[*] Hosts found: 2
---------------------
demo.testfire.net:65.61.137.117
www.testfire.net:65.61.137.117
Here theHarvester returns you the details of the domain testfire.net from the Bing search engine. Here it is showing only hosts were found in the search.
Note:- in the recent update of theHarvester tool they removed the source google. So here now we can’t able to get results from Google searches.
Kockpy Tool for passive information gathering
Knockpy is a Python-based tool used for information gathering and reconnaissance. It is specifically designed to enumerate subdomains on a target domain by using a variety of techniques, including DNS brute-forcing, permutation generation, and Google scraping.
Knockpy can be used to quickly identify subdomains that may be vulnerable to attack, allowing security researchers and penetration testers to focus their efforts on the most promising targets. Additionally, Knockpy can also be used to perform basic information gathering on a target domain, such as identifying the DNS server and MX records. Overall, Knockpy is a powerful and effective tool for information gathering and reconnaissance.
For installing knockpy click here
The basic syntax for knockpy.py:-
python3 knockpy.py [domain-name]Knockpy v5.3.0
_ __ _
| |/ / | | v5.3.0
| ' / _ __ ___ ___| | ___ __ _ _
| < | '_ \ / _ \ / __| |/ / '_ \| | | |
| . \| | | | (_) | (__| <| |_) | |_| |
|_|\_\_| |_|\___/ \___|_|\_\ .__/ \__, |
| | __/ |
|_| |___/ Let’s try to gather information on the target domain testfire.net
└─$ python3 knockpy.py testfire.net
_ __ _
| |/ / | | v5.3.0
| ' / _ __ ___ ___| | ___ __ _ _
| < | '_ \ / _ \ / __| |/ / '_ \| | | |
| . \| | | | (_) | (__| <| |_) | |_| |
|_|\_\_| |_|\___/ \___|_|\_\ .__/ \__, |
| | __/ |
|_| |___/
local: 10757 | google: 4 | duckduckgo: 1 | virustotal: 0
Wordlist: 10762 | Target: testfire.net | Ip: 65.61.137.117
08:21:59
Ip address Code Subdomain Server Real hostnam
--------------- ---- ------------------------------------ ------------------------------------ ------------
65.61.137.117 200 altoro.testfire.net Apache-Coyote/1.1
65.61.137.117 200 demo.testfire.net Apache-Coyote/1.1
65.61.137.117 200 demo2.testfire.net Apache-Coyote/1.1
65.61.137.117 200 evil.testfire.net Apache-Coyote/1.1
65.61.137.117 200 ftp.testfire.net Apache-Coyote/1.1 testfire.net
65.61.137.117 200 localhost.testfire.net Apache-Coyote/1.1
65.61.137.117 200 www.testfire.net Apache-Coyote/1.1 testfire.net
08:23:01
Ip address: 1 | Subdomain: 7 | elapsed time: 00:01:02 here we got some information about the target’s IP address, subdomain, server version and type, and hostname
Maltego for information gathering

Maltego is a tool used for information gathering and analysis. It is specifically designed to visualize complex relationships between entities on a network, such as individuals, organizations, websites, and infrastructure. Maltego uses a concept called “transforms” to gather data from various sources and transform it into a visual graph, allowing users to easily identify and analyze patterns and connections.
Maltego can be used for various types of information gathering, including open-source intelligence (OSINT), cyber threat intelligence (CTI), and social network analysis (SNA). It allows users to quickly and easily gather and analyze data from a variety of sources, including social media, the Dark Web, and public databases.

Online tools for information gathering
whois domain tools
WHOIS is a network protocol used to query databases that store information about registered domain names and their associated owners or administrators. The WHOIS protocol allows users to query a WHOIS server to obtain information about a specific domain name, such as the registered owner, contact information, and the domain’s expiration date.
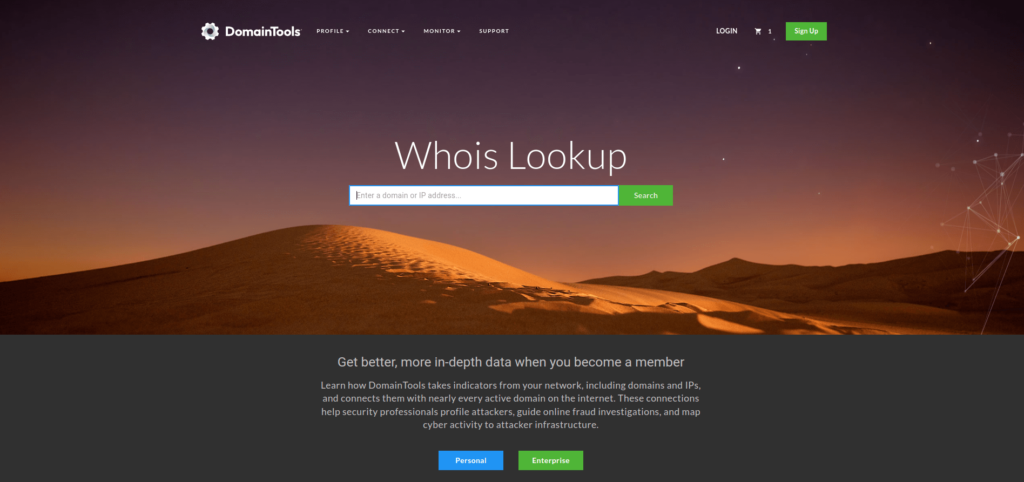
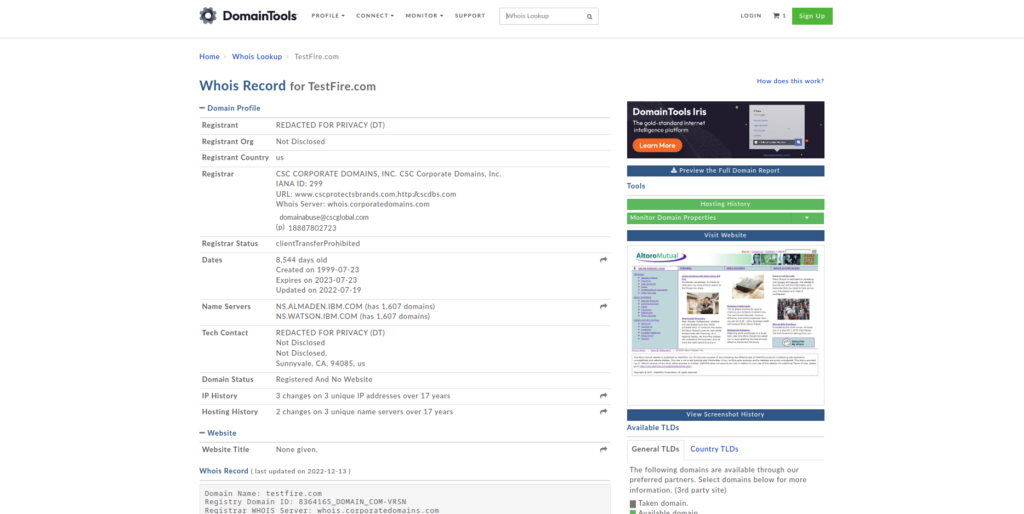
Netcraft
Netcraft also offers a range of other online tools and services, including a phishing site reporting service, a website attack detection service, and an SSL certificate monitoring service. These tools are used by businesses, security researchers, and individuals to protect their web-based assets and ensure the security of their online presence.
The Netcraft Toolbar is available for the Chrome, Firefox, and Safari web browsers, and can be installed as an extension from the respective browser’s app store.
Who.is
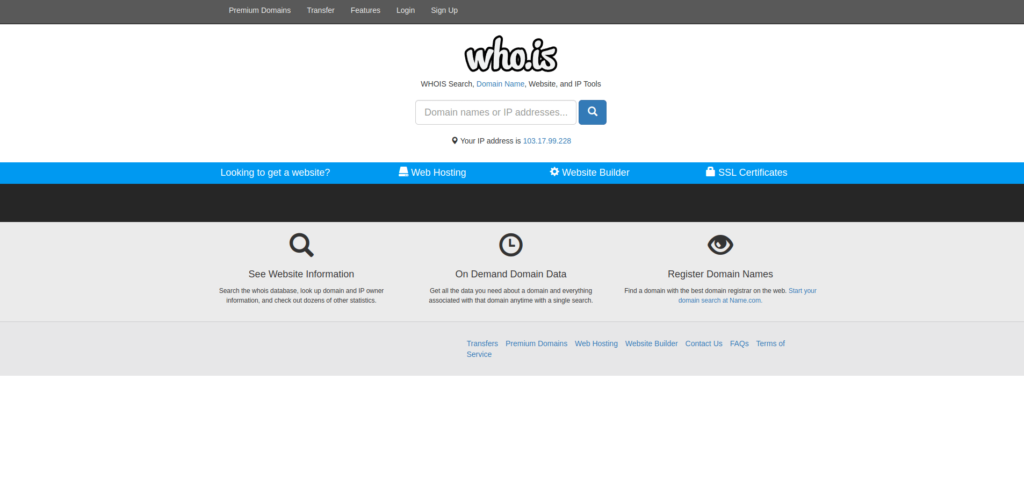
The website “who.is” is a service that provides a user-friendly interface for performing whois lookups. With this website, users can enter a domain name or IP address and the website will display the information that is associated with it. This can be useful for quickly looking up information about a domain without having to use the whois command on the command line. However, please note that the information provided by “who.is” may not be as comprehensive or up-to-date as the information provided by the official registrar or registry for a given domain.
Robtex
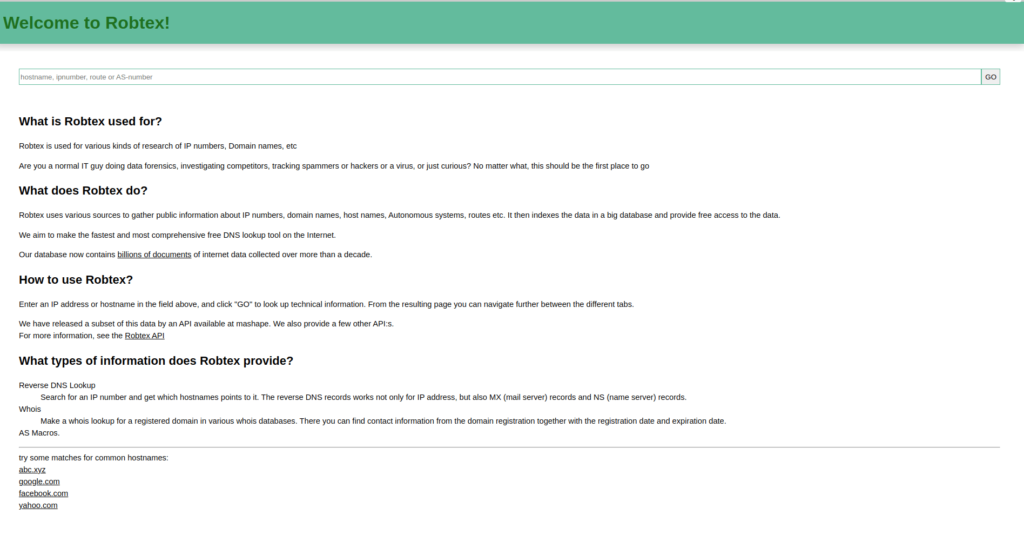
Robtex is a website that provides a variety of online tools and services related to networking and security. Some of the services offered by Robtex include DNS lookup, whois lookup, and IP address lookup. The website also provides information about internet infrastructures, such as data center locations and network topology. Additionally, Robtex offers security tools, such as a port scanner and a password checker, to help users ensure the safety of their online accounts and networks. Overall, Robtex is a useful resource for those who work in the fields of networking, security, and internet infrastructure.
Thank you for reading this post, don't forget to subscribe!





Comments are closed.