When we want to target a network, we want to find an efficient tool {Nmap live host} to help us handle repetitive tasks and answer the following questions:
- Which systems are up?
- What services are running on these systems?
The tool that we will rely on is Nmap. The first question about finding live computers is answered in this room. This room is the first in a series of four rooms dedicated to Nmap.
The second question about discovering running services is answered in the next Nmap rooms that focus on port-scanning.
This room is the first of four in this Nmap series. These four rooms are also part of the Network Security module.
This room explains the steps that Nmap carries out to discover the systems that are online before port-scanning. This stage is crucial because trying to port-scan offline systems will only waste time and create unnecessary noise on the network. {Nmap live host}
We present the different approaches that Nmap uses to discover live hosts. In particular, we cover:
- ARP scan: This scan uses ARP requests to discover live hosts
- ICMP scan: This scan uses ICMP requests to identify live hosts
- TCP/UDP ping scan: This scan sends packets to TCP ports and UDP ports to determine live hosts.
We also introduce two scanners, arp-scan and masscan, and explain how they overlap with part of Nmap’s host discovery.
As already mentioned, starting with this room, we will use Nmap to discover systems and services actively. Nmap was created by Gordon Lyon (Fyodor), a network security expert and open-source programmer. It was released in 1997. Nmap, short for Network Mapper, is free, open-source software released under GPL license.
Nmap is an industry-standard tool for mapping networks, identifying live hosts, and discovering running services. Nmap’s scripting engine can further extend its functionality, from fingerprinting services to exploiting vulnerabilities. A Nmap scan usually goes through the steps shown in the figure below, although many are optional and depend on the command-line arguments you provide.
Task 2 Subnetworks
Question: How many devices can see the ARP Request?
Request:
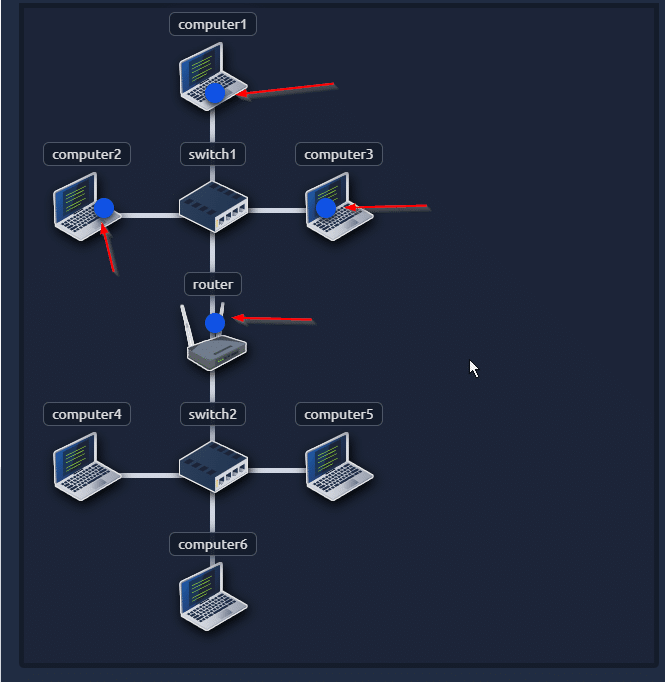
Answer: 4
Question: Did computer6 receive the ARP Request? (Y/N)
Answer: N
Explain: Our packet is going to only four pc not to pc 6
Question: How many devices can see the ARP Request?
Answer: 4
Question: Did computer6 reply to the ARP Request? (Y/N)
Answer: Y
Task 3 Enumerating Targets
Question: What is the first IP address Nmap would scan if you provided 10.10.12.13/29 as your target?
Hint: Run nmap -sL -n 10.10.12.13/29
Options: -sL {}
Answer: 10.10.12.8
Question: How many IP addresses will Nmap scan if you provide the following range 10.10.0-255.101-125?
Hint: Run nmap -sL -n 10.10.0-255.101-125
Answer: 6400
Task 4 Discovering Live Hosts
Question: What is the type of packet that computer1 sent before the ping?
Answer: ARP Request
Question: What is the type of packet that computer1 received before being able to send the ping?
Answer: ARP Response
Question: How many computers responded to the ping request?
Answer: 1
Question: What is the name of the first device that responded to the first ARP Request?
Answer: router
Question: What is the name of the first device that responded to the second ARP Request?
Answer: computer5
Question: Send another Ping Request. Did it require new ARP Requests? (Y/N)
Answer: n
Task 5 Nmap Host Discovery Using ARP
Question: How many devices are you able to discover using ARP requests?
Answer: 3
Task 6 Nmap Host Discovery Using ICMP
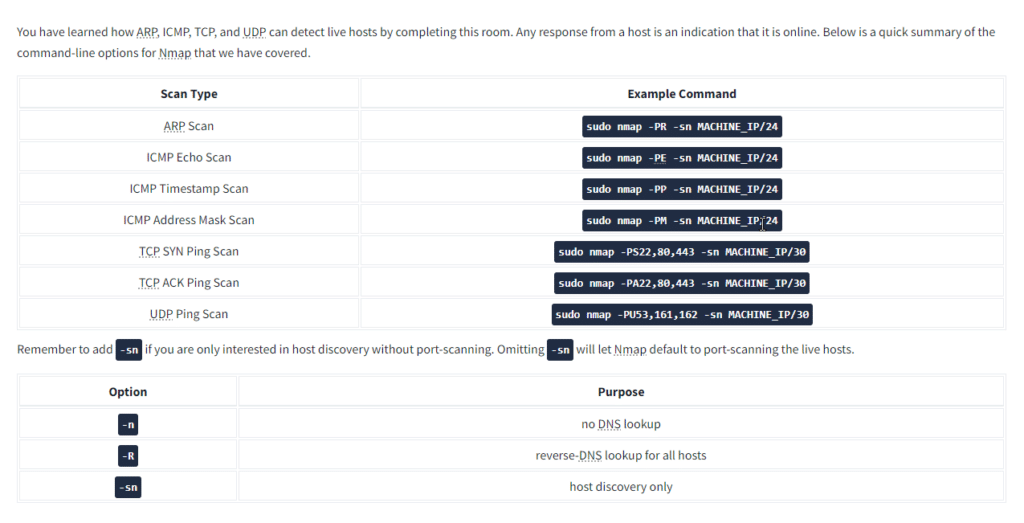
Question: What is the option required to tell Nmap to use ICMP Timestamp to discover live hosts?
Answer: -PE
Question: What is the option required to tell Nmap to use ICMP Address Mask to discover live hosts?
Answer: -PM
Question: What is the option required to tell Nmap to use ICMP Echo to discover live hosts?
Answer: -PE
Task 7 Nmap Host Discovery Using TCP and UDP {Nmap live host}
Question: Which TCP ping scan does not require a privileged account? {Nmap live host}
Answer: tcp syn ping
Question: Which TCP ping scan requires a privileged account?
Answer: tcp ack ping
Question: What option do you need to add to Nmap to run a TCP SYN ping scan on the telnet port?
Answer: -p23
Task 8 Using Reverse-DNS Lookup
Question: We want Nmap to issue a reverse DNS lookup for all the possibles hosts on a subnet, hoping to get some insights from the names. What option should we add? {Nmap live host}
Answer: -R
{Nmap live host}{Nmap live host}
{Nmap live host}{Nmap live host}