Table of Contents
ToggleActive Directory (AD) is widely used by almost every big organisation to manage, control and govern a network of computers, servers and other devices. The room aims to teach basic concepts for hardening AD in line with best cyber security practices.
Learning Objectives
The topics that we will cover in this room include:
- Secure authentication methods
- Securing hosts through group policies
- Implementing the Least Privilege model
- Protection against known AD attacks
- Recovery Plan (Post-compromise scenario)
Prerequisites
Before starting this room, we recommend going through the following rooms to develop a solid understanding of Windows AD:
- Active Directory basics
- Breaching Active Directory
- Standard technologies used in the corporate environment
Connecting to the Machine
We will be using Windows Server 2019 as a development/test machine throughout the room with the following credentials:
- IP:
MACHINE_IP - Username:
Administrator - Password:
tryhackmewouldnotguess1@
You can access the VM by clicking Start Machine. The machine will start in a split-screen view. If the VM is not visible, use the blue Show Split View button at the top-right of the page. Alternatively, you can access the VM through Remote Desktop using the above credentials.
Let’s begin. Active Directory
Task 2 Understanding General Active Directory Concepts
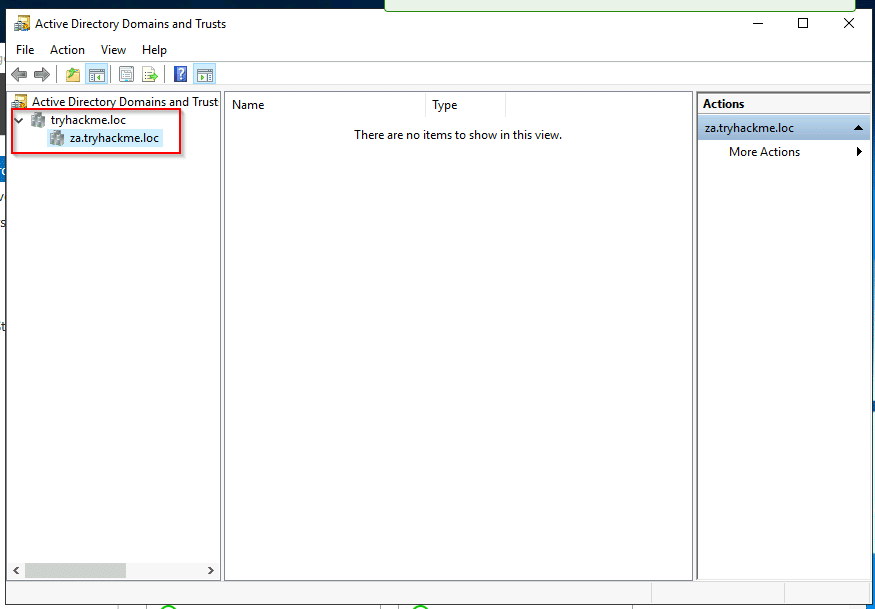
Question: What is the root domain in the attached AD machine?
Answer: tryhackme.loc
Hint: Server Manager > Tools > Active Directory Domains and Trust
Task 3 Securing Authentication Methods
Question: Change the Group Policy Setting in the VM, so it does not store the LAN Manager hash on the next password change. Active
Path: Group Policy Management Editor > Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options > Domain controller: LDAP server signing requirements > select Require signing from the dropdown
Steps:
Open group policy management Active Directory
Expand Group Policy Objects Tab
Right-click and create new policy name {anythink}
Right click and edit the policy from the path given above
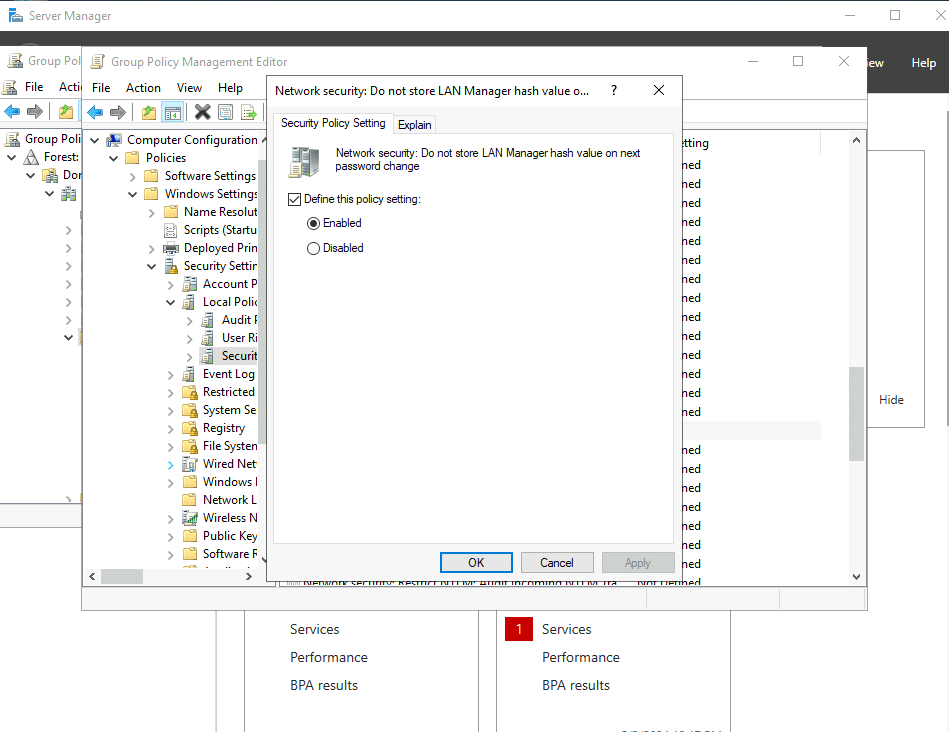
Question: What is the default minimum password length (number of characters) in the attached VM?
Answer: 7
Task 4 Implementing the Least Privilege Model
Question: Computers and Printers must be added to Tier 0 – yea/nay?
Answer: nay
Question: Suppose a vendor arrives at your facility for a 2-week duration task. Being a System Administrator, you should create a high privilege account for him – yea/nay?
Answer: nay
Task 5 Microsoft Security Compliance Toolkit
Question: Find and open BaselineLocalInstall script in PowerShell editor – Can you find the flag?
Hint: go to {C:\Users\Administrator\Desktop\Scripts\Windows Server 2019 Security Baseline\Local_Script}
then right click and open Baeline script in editor and fing the flag
Answer: Flag : THM{00001}
Question: Find and open MergePolicyRule script (Policy Analyser) in PowerShell editor – Can you find the flag?
Hint: path to go {C:\Users\Administrator\Desktop\Scripts\PolicyAnalyzer\PolicyAnalyzer_40}
Answer: Flag : {THM00191}
Task 6 Protecting Against Known Attacks
Question: Does Kerberoasting utilise an offline-attack scheme for cracking encrypted passwords – yea/nay?
Answer: yea
Question: As per the generated report, how many users have the same password as aaron.booth?
Answer: 186
If you have any queries regarding the above content, or you want to update anything in the content, then contact us with your queries. You can directly post your question in the group.
Connect with us on these platforms



