Table of Contents
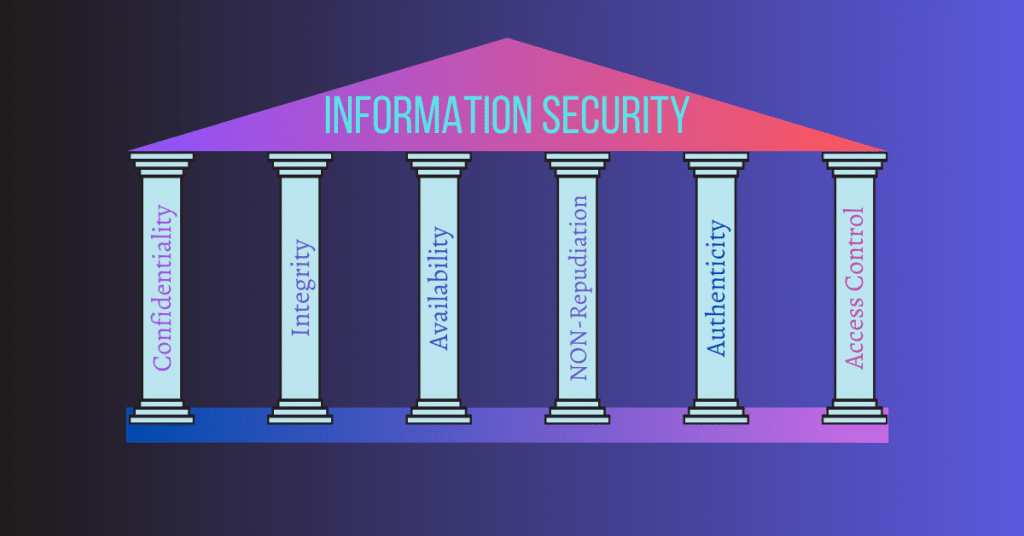
ToggleHello everyone lucifer here with a topic of pillars of information security. Pillars are like the base on which any building stands, without pillars the building will get fall and smash.
These pillars confirm that the security is running smoothly with no unauthorized access or any type of data theft is there.
these pillars are very important for information security functionality in the real world. Every online data and content need to follow the policy of these pillars which is also very essential for proper data flow and safety over any network.
The 6 pillars of information security are:
- Confidentiality
- Integrity
- Availability
- Non-repudiation
- Authenticity
- Access control
Let’s discuss every pillar in brief
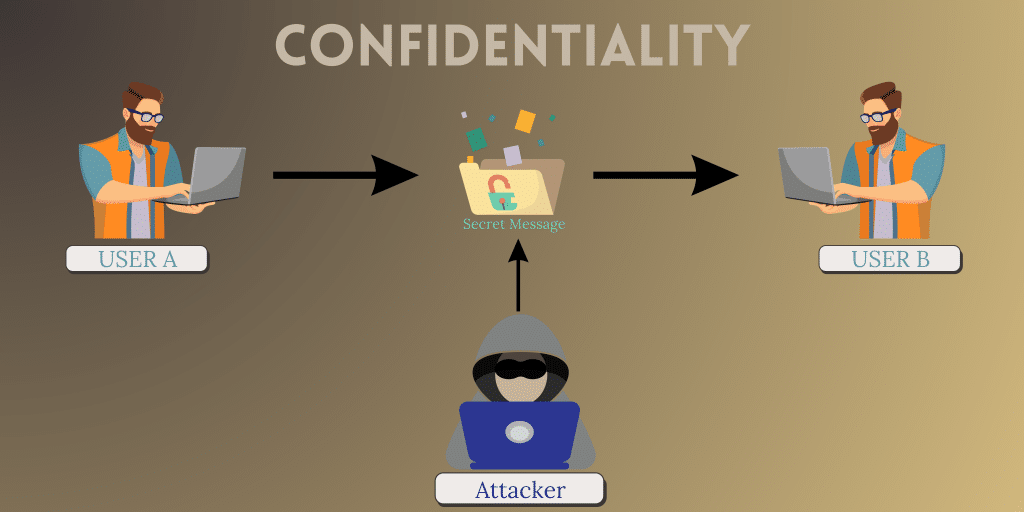
Confidentiality
This is the first and very essential principle in information security that is liable for the assurance that the information is accessible only to the authorized user. That means if User A sends any message to User B then the data of the message is only accessible to user B no other users will be able to access the data without user A permission.
If there are four users in the same network that are User (A, B, C, D), and user A sends something to user C then that data is only accessible to user C. But in some conditions, if user B got the data then also he/she can’t able to understand it because encryption is done by user A.
Confidentiality controls include data classification, data encryption, and proper disposal of equipment such as (DVDs, USB drives, Hard Drives, etc.).
Confidentiality breaches may occur due to improper data handling or hacking attempts. If the confidentiality breaks then it is called an attack of interception.
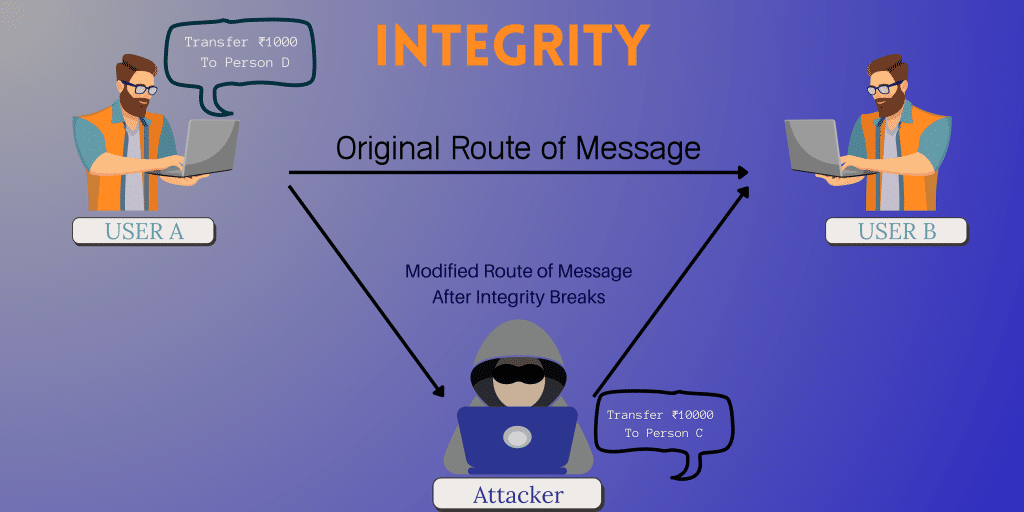
Integrity
This principle insures that the data flowing on the network between two parties has not been modified at any cost during the traveling. This creates thrust worthiness between the parties for the correct data they are sharing with each other.
Integrity will help users in the prevention of improper and unauthorized changes that assure the information is sufficiently accurate for its purpose.
Integrity can be achieved by proper handling of checksum (a number produced by a mathematical function to verify that a given block of data is not changed) and by maintaining access control (which ensures that only an authorized user can update, add, or delete data).
If integrity breaks then it is called an attack of modification.
Availability
This principle also plays a very important role in information security pillars along with integrity and confidentiality principles. availability ensures that the data or information is available all the time for the authorized user when he/she needs it.
It assures that the systems responsible for delivering, storing, and processing information are accessible when required by authorized users.
In other words, we can say that the assurance of the information and resources are available and reliable when required by an authorized party.
availability can be maintained by including disk arrays for redundant systems and clustered machines, antivirus software to combat malware, and distributed denial-of-service (DDoS) preventions.
If the availability breaks then it is called as an attack of interruption.
NON-Repudiation
The principle of non-repudiation ensures that the sender of the message cannot later deny that he sent that message and that the recipient of the message cannot be able to deny that he received the message.
Any individual or organization uses a digital signature to ensure non-repudiation
In other words, we can say that after sending or receiving any message the party cannot later deny having done so, nor they deny the content or accuracy of the message.
Digital signature certificates play a very important role in ensuring non-repudiation. this is because a digital signature certificate provides unique and verifiable proof of the sender’s identity and the integrity of the data being transmitted.
There are several attacks that can be done if non-repudiation breaks that are Replay attacks, Man-In-The-Middle (MITM) attacks, Denial of Service (DoS) attacks, etc.
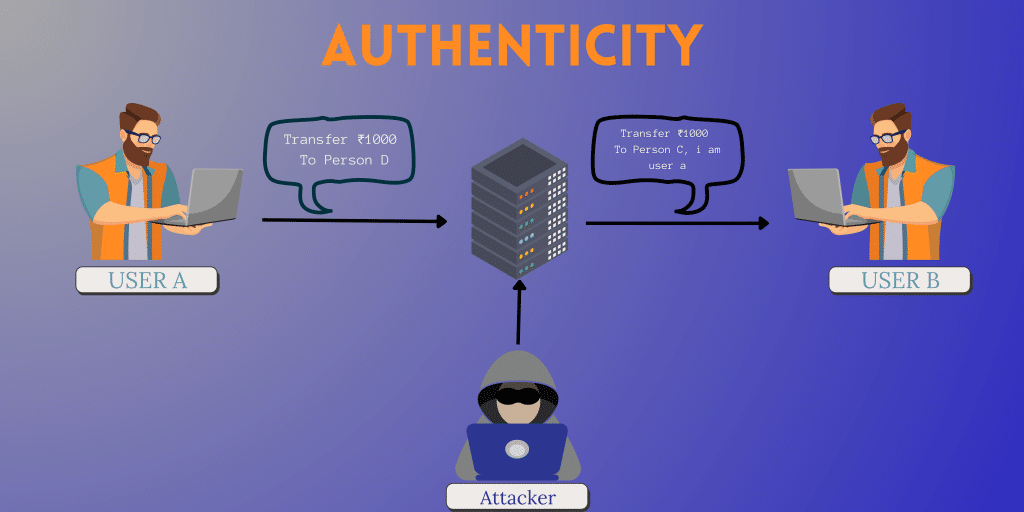
Authenticity
The principle of authenticity ensures that the user is genuine who sent the message. This will provide the assurance to the recipient of the data or the information that they received is generated from a genuine user and legitimate sources.
This principle ensures that the data or the information is legitimate and cannot be altered, or not tampered with by any unauthorized user.
Authenticity can be achieved by the implementation of digital signatures, encryption, and authentication protocols.
Access Control
This information security principle ensures that only authorized users can access the resources or information when needed. access control can also be defined as restricting access to data or resources based on a set of predefined policies and rules.
This principle is very important in securing data from unauthorized access and theft or misuse. Access control involves many steps and components, that include authentication, authorization, and accountability.
Access control can be used for creating access levels for the employees that what type of employee can access what level of data or resources. which means A normal employee can’t access its HR data or HR cannot be able to access the admin data because of the security level.
If you have any queries regarding the above content, or you want to update anything in the content, then contact us with your queries. You can directly post your question in the group.
Connect with us on these platforms