Gathering data on systems that are “alive” and responding on the network is the process of scanning. The first step in the network scanning procedure is host discovery.
It is vital to look for active systems in order to conduct a thorough scan and locate open ports and services.
An attacker can skip scanning every port on every system in a list of IP addresses in order to determine whether the target host is up by using host discovery, which gives an exact state of the systems in the network.
The initial stage in network scanning is host discovery. This section describes numerous ping scan strategies that can be used to look for active systems in a network.
Along with several ping sweep tools, it also goes through how to ping sweep a network to find active hosts and systems.
Host Discovery Techniques
Host discovery techniques can be used to find the active/live hosts in the network. You must be knowledgeable about the various host discovery approaches if you want to hack ethically. The following is a list of some host discovery methods:
- ARP Ping Scan
- UDP Ping Scan
- ICMP Ping Scan
- ICMP ECHO Ping
- ICMP ECHO Ping Sweep
- ICMP Timestamp Ping
- ICMP Address Mask Ping
- ICMP ECHO Ping
- TCP Ping Scan
- TCP SYN Ping
- TCP ACK Ping
- IP Protocol Scan
ARP Ping Scan
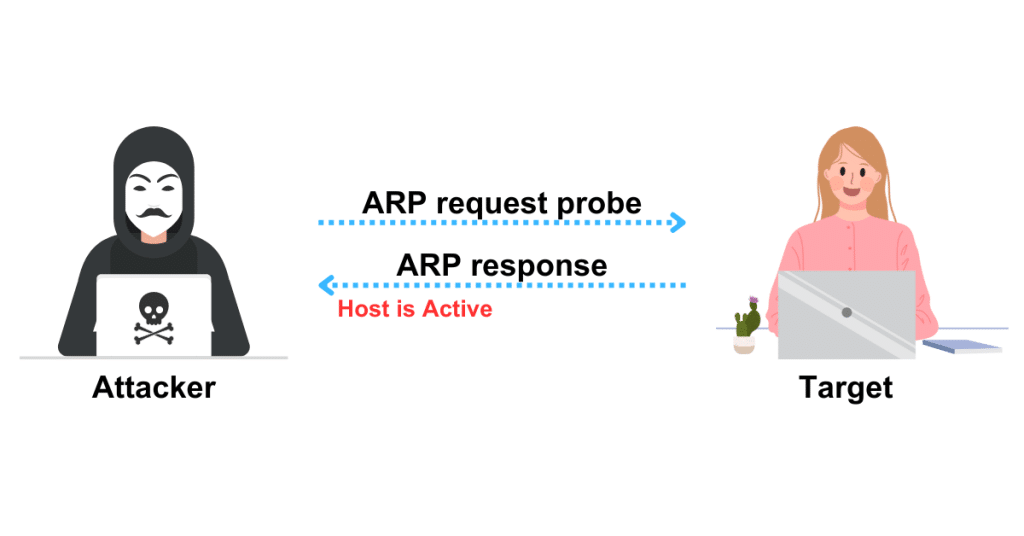
Even though the presence of such devices is hidden by restrictive firewalls, the ARP ping scan sends ARP packets to find all active devices in the IPv4 range. In a majority of networks, particularly in the LAN’s private address ranges, numerous IP addresses are always unoccupied.
Therefore, the OS must determine the hardware destination address (ARP) matching to the target IP for addressing the Ethernet frame appropriately when the attackers attempt to transmit IP packets to the target host, such as ICMP echo requests. A series of ARP requests are sent out for this reason.
The MAC address of the device’s network interface and all other devices on the LAN that share the same IPv4 address can both be seen via an ARP scan. If the host IP associated with the corresponding hardware destination address is active, the host will generate the ARP response; otherwise, the original OS gives up on the host after a certain number of ping attempts.
To put it another way, if an attacker sends an ARP request probe to a target host and receives an ARP response, the host is active. If the destination host is discovered to be unresponsive, the source host updates the destination IP’s incomplete entry in its kernel ARP database.
Mostly Attacker uses the NMAP tool for performing ARP ping scans for discovering live hosts in the network.
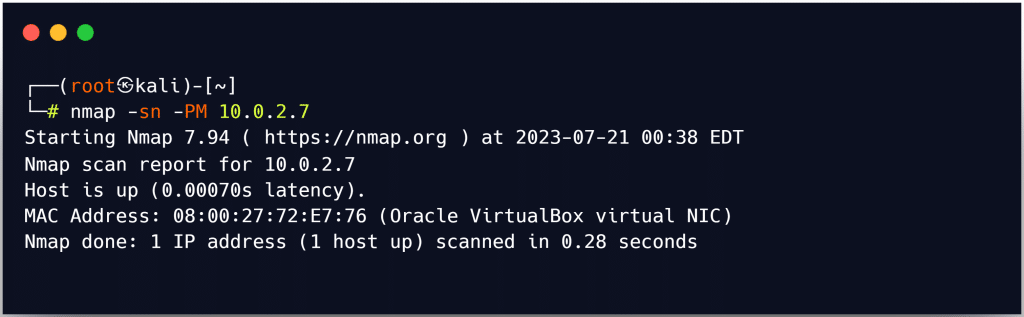
Note:- The Nmap command to stop the port scan is -sn. You can use –disable-arp-ping to stop Nmap from using the default ARP ping scan and carry out any other requested ping scans instead.
Advantages of ARP Ping Scan
- ARP ping scan always provides accurate and more efficient results than other host discovery techniques.
- ARP ping scan is helpful for system discovery, where you may need to scan vast address spaces
- it automatically manages ARP requests, retransmissions, and timeouts at its discretion.
- It can also show the response time or latency of a device to an ARP packet.
UDP Ping Scan
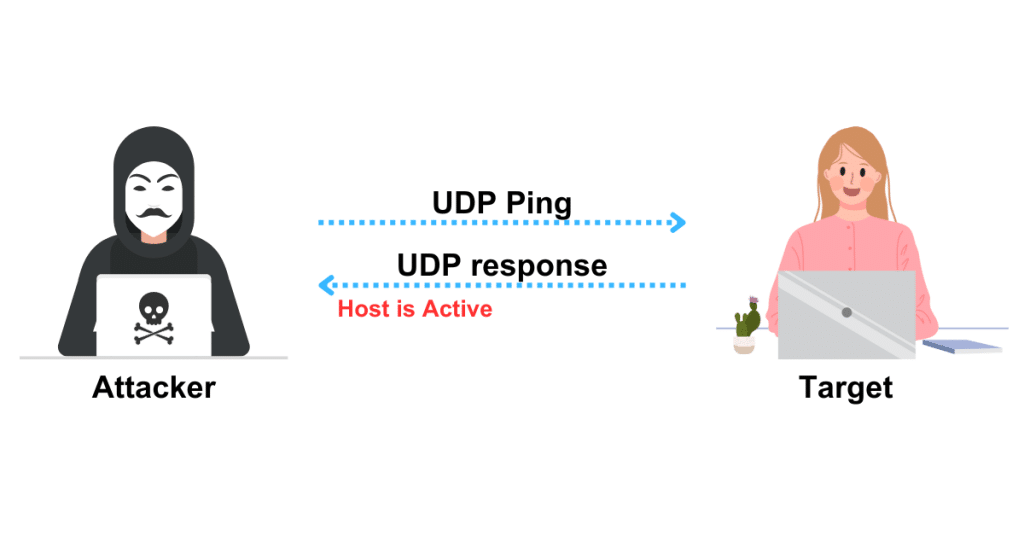
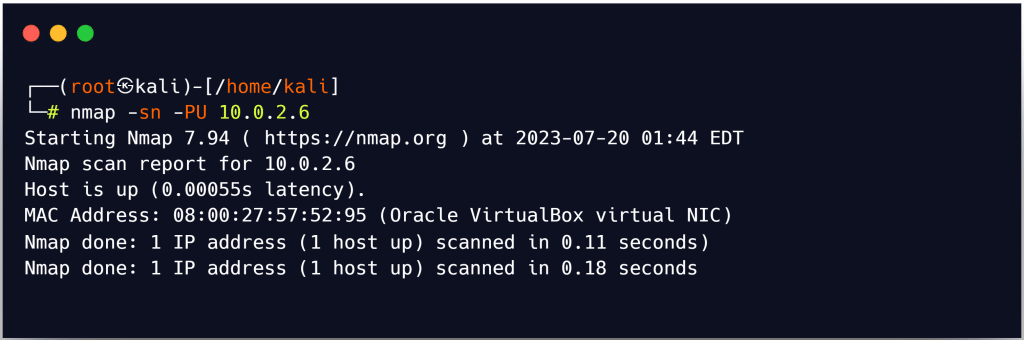
Similar to a TCP ping scan, a UDP ping scan uses Nmap to send UDP packets to the target host. Nmap uses port 40,125 by default when performing a UDP ping scan. Sending UDP packets to the target is done by default using this incredibly unusual port. When compiling Nmap, this default port number can be changed using DEFAULT_UDP_PROBE_PORT_SPEC.
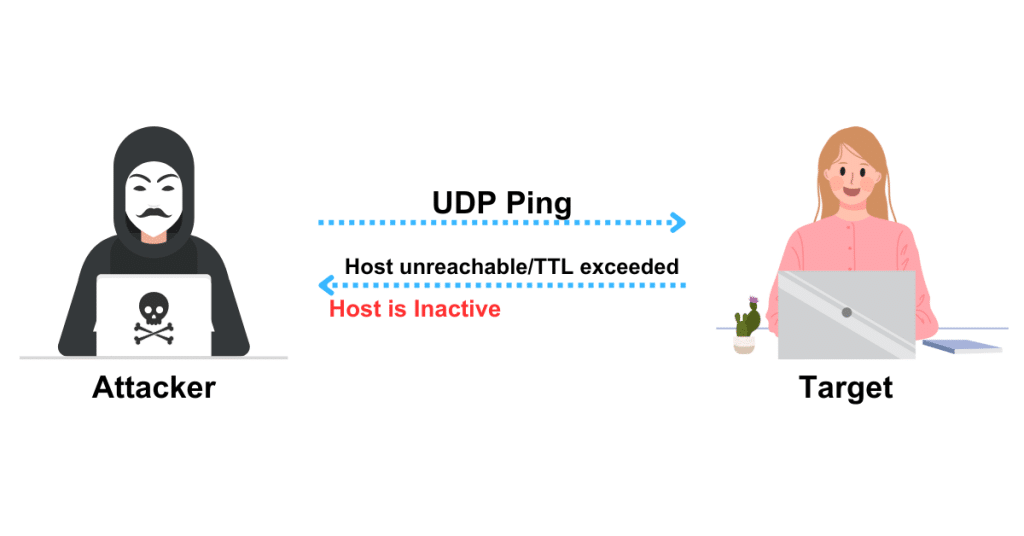
Attackers transmit UDP packets to the target host; if the target host responds, it is active. Different error messages, such as host/network unavailable or TTL exceeded, may be returned if the destination host is down or unreachable. To do a UDP ping scan with Zenmap, use the -PU option.
Advantages of UDP Ping Scan
it has the advantage of detecting the system behind the firewalls with strict TCP filtering and leaving the UDP traffic unfiltered.
ICMP ECHO Ping Scan
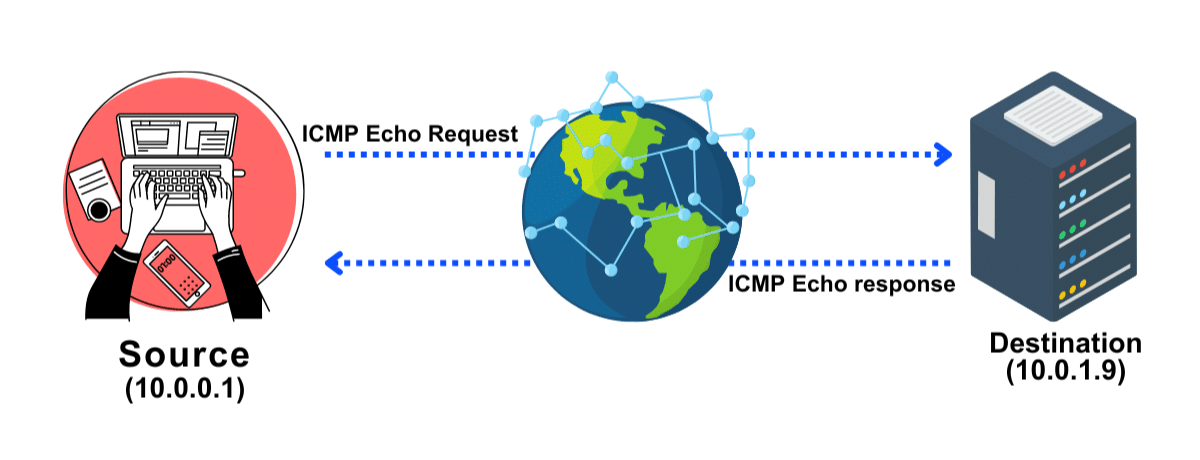
Attackers send ICMP packets to the target system as part of an ICMP ping scan to collect all the data they require about it. This is so that ICMP can be distinguished from port scanning, which includes port abstraction. However, by pinging every host in a network, it is possible to learn which hosts are active.
Sending ICMP ECHO queries to a host is part of an ICMP ECHO ping scan. The host will respond with an ICMP ECHO if it is still functional. Finding active devices or figuring out whether ICMP is getting via a firewall are also possible uses for this scan.
The TCP/IP stack implementations in these OS’s react to the ICMP echo queries to the broadcast addresses on UNIX/Linux and BSD-based workstations. As the TCP/IP stack implementation in Windows does not respond to ICMP probes sent to the broadcast address, this approach is ineffective on Windows-based networks.
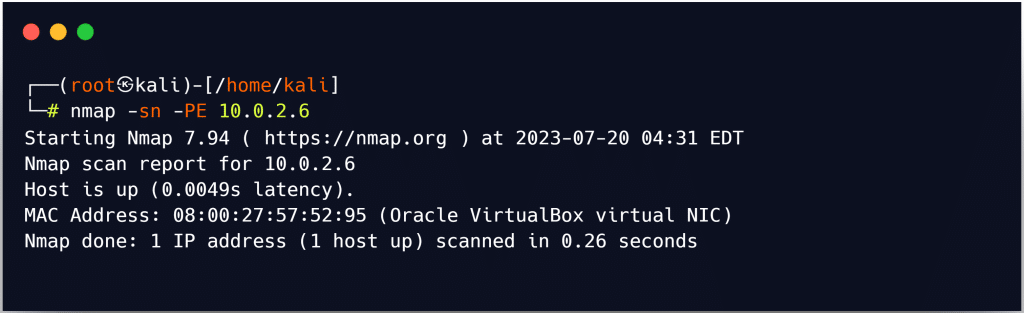
The -P option of Nmap is used to ICMP scan the target. The -L option allows the user to increase the number of simultaneous pings. The – T option can be used to change the ping timeout value.
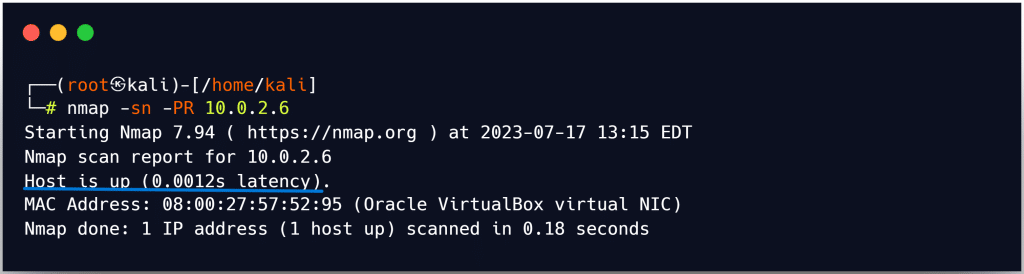
In nmap, the -PE option is used to perform the ICMP ECHO ping scan. Active hosts are displayed as “Host is up,” as shown in the screenshot.
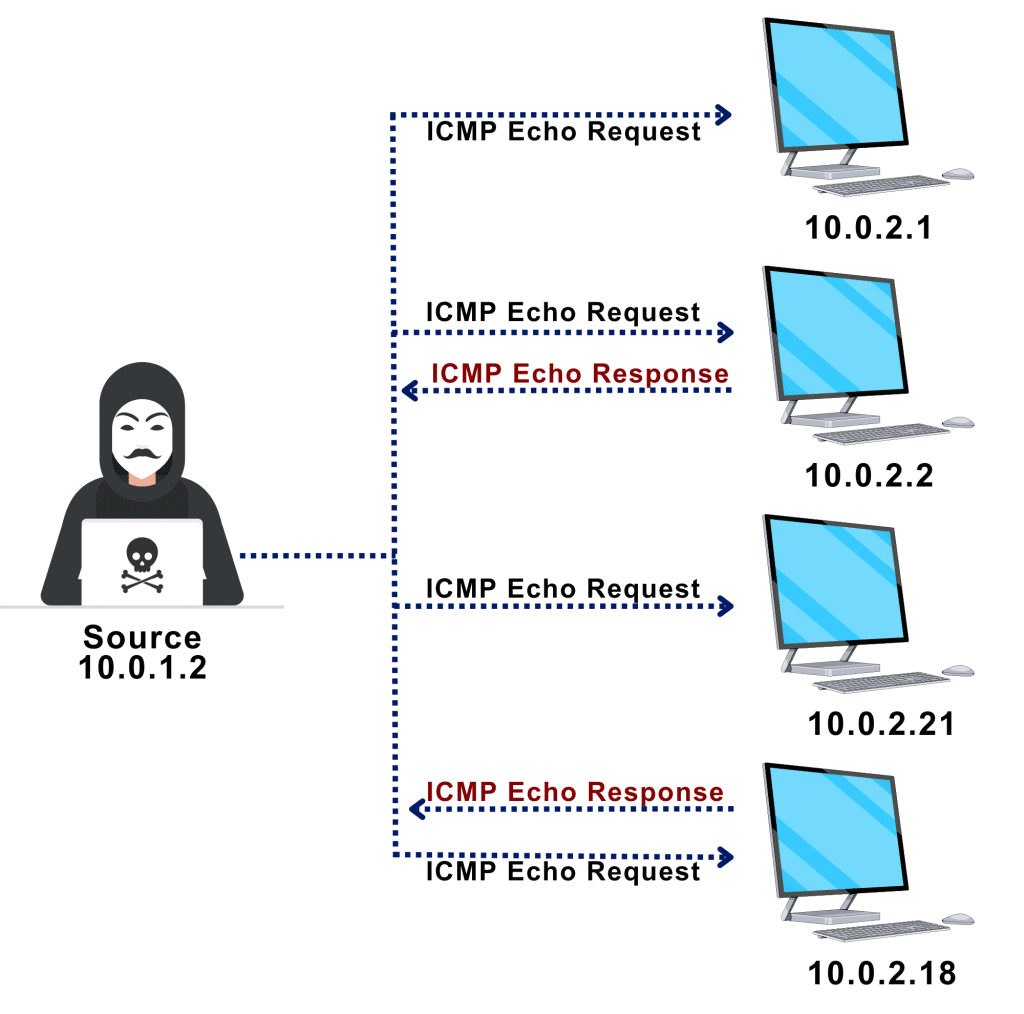
ICMP Echo Ping Sweep
An ICMP sweep, commonly referred to as a ping sweep, is a fundamental network scanning technique used to identify the range of IP addresses that correspond to active hosts (computers).
A ping sweep is made up of many ICMP ECHO queries that are sent to numerous hosts, even though a single ping will tell the user whether a particular host machine is there on the network. An ICMP ECHO reply will be returned by the specified host if it is operational.
Ping sweeps are among the oldest and slowest methods used to scan a network. This utility is distributed across nearly all platforms, and it acts as a roll call for systems; a system that is active on the network answers the ping query that another system sends out.
ICMP echo scanning pings all the machines in the target network to discover live machines. Attackers send ICMP probes to the broadcast or network address, which relays to all the host addresses in the subnet. The live systems will send the ICMP echo reply message to the source of the ICMP echo probe.
One should be able to comprehend the TCP/IP packet in order to comprehend pings better. A system that does a ping transmits a single packet to a particular IP address via the network.
The 64 bytes in this packet are made up of 8 bytes of protocol header information and 56 bytes of data. After that, the sender watches or listens for a response packet from the recipient system.
A nice return packet is anticipated if the connections are strong and the target computer is “alive”. If there is a communication breakdown, this won’t be the case. Pings also provide information on the “round-trip time,” which is the amount of time it takes a packet to travel completely.
They additionally assist with hostname resolution. The system cannot match the name with the given IP address in this situation if the packet bounces back when sent to the IP address but not when sent to the name.
Attackers use subnet mask calculators to determine the number of hosts in a subnet by computing the subnet mask. After that, they utilize ping sweep to compile a list of active systems in the subnet.
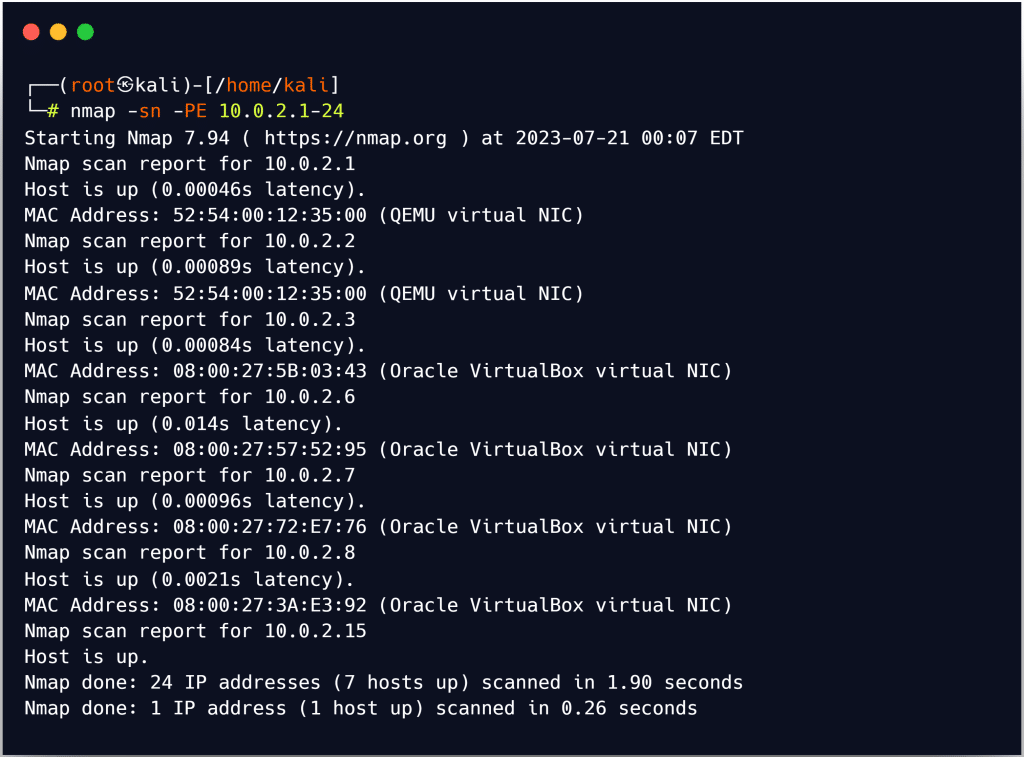
ICMP Echo Ping Sweep Using Nmap
An attacker can use Nmap to carry out a ping sweep to identify active hosts from a variety of IP addresses. For an ICMP ECHO ping sweep, the nmap -PE option with a list of IP addresses is utilized.
ICMP Timestamp Ping Scan
In addition to the standard ICMP ECHO ping, an attacker may use various ICMP pinging methods under certain circumstances, such as the ICMP timestamp ping scan and the ICMP address mask ping scan.
An optional and extra type of ICMP ping called an “ICMP timestamp ping” allows attackers to obtain information from the target host machine about the current time by querying a timestamp message.
Each timestamp query is answered by the target computer with a timestamp reply. However, depending on how the administrator at the target’s end has configured it, the answer from the destination host may or may not include the time value.
The purpose of this ICMP timestamp pinging is often to synchronize the time. In particular, when the administrator disables the standard ICMP ECHO ping queries, such a ping method is efficient in determining whether the destination host machine is operational.
The -PP option in Zenmap is used to run an ICMP timestamp ping scan.
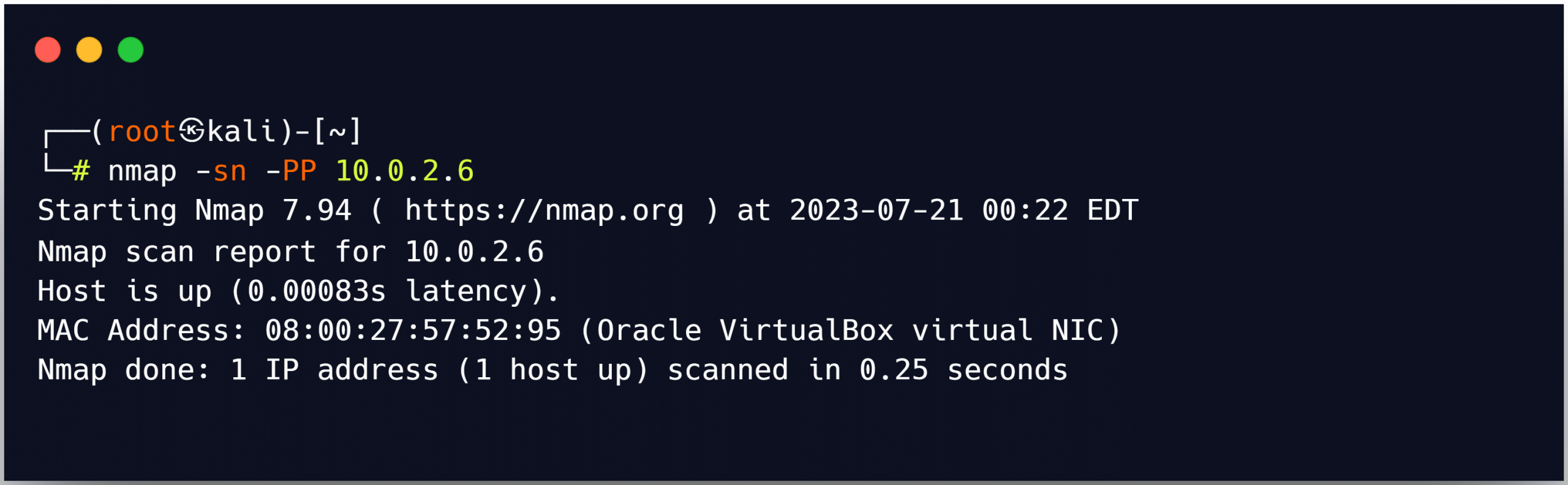
ICMP Address Mask Ping Scan
An alternative to the conventional ICMP ECHO ping is the ICMP address mask ping, in which the attackers send an ICMP address mask inquiry to the target host in order to obtain information about the subnet mask.
However, the address mask answer from the destination host is conditional, and depending on how the administrator at the target’s end has configured it, it may or may not respond with the correct subnet value.
Similar to the ICMP timestamp ping, this kind of pinging technique is excellent at locating active hosts, especially when the administrator disables the standard ICMP Echo ping. The -PM option in Zenmap is used to run an ICMP address mask ping scan.
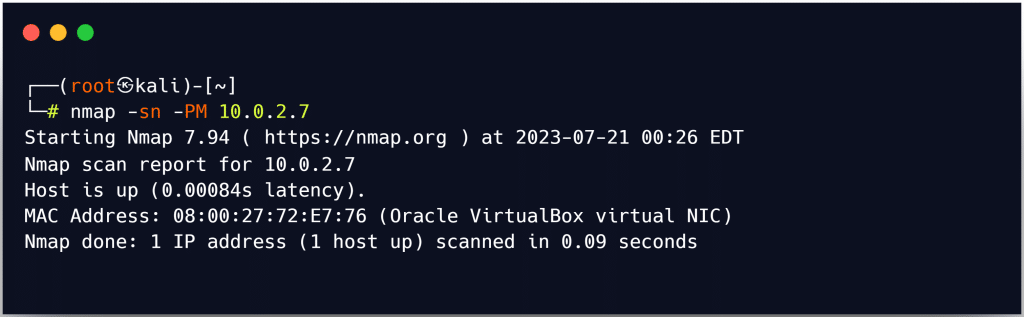
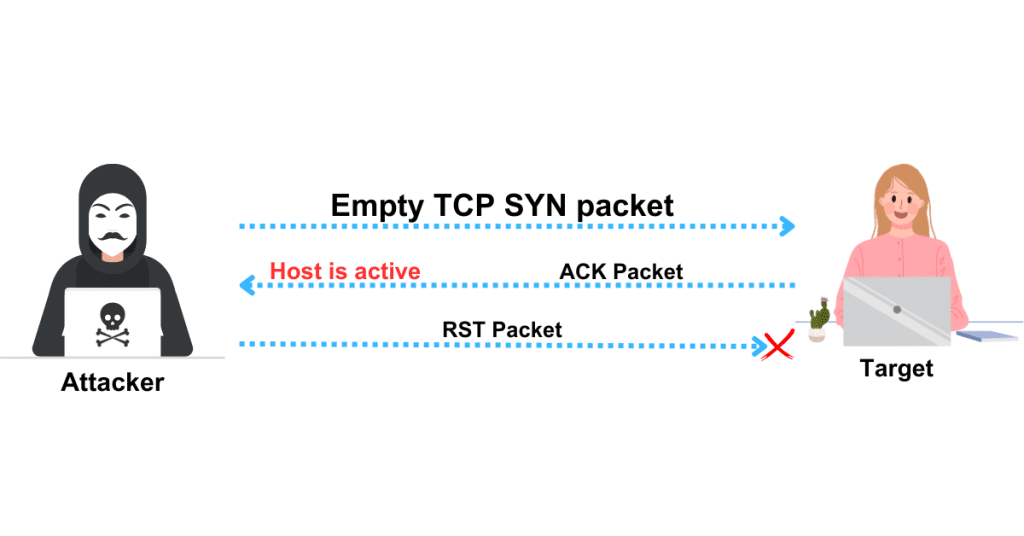
TCP SYN Ping Scan
A host discovery technique called TCP SYN ping is used to examine various ports to see whether they are open and to see if any firewall rule sets are present.
In this kind of host discovery technique, an attacker sends the target host an empty TCP SYN flag to start the three-way handshake. The destination host notifies the sender of SYN that it has received it by setting an ACK flag.
The attacker validates that the target host is active upon receipt of the ACK flag before cutting off communication by sending an RST flag to the target host machine (because the attacker’s goal of host discovery has been achieved).
The standard destination port is port 80. In this kind of pinging style, a range of ports can also be supplied without a space between -PS and the port number (for example, PS22-25,80,113,1050,35000), in which case the probe will be executed against each port concurrently. To do a TCP SYN ping scan in Zenmap, use the -PS option.
Advantages of TCP SYN Ping scan
- The scan never encounters the time-out problem while waiting for the response because the machines can be scanned simultaneously.
- You can check the host’s activity with TCP SYN ping without establishing a connection. As a result, the logs are not kept at the system or network level, allowing the attacker to avoid being discovered.
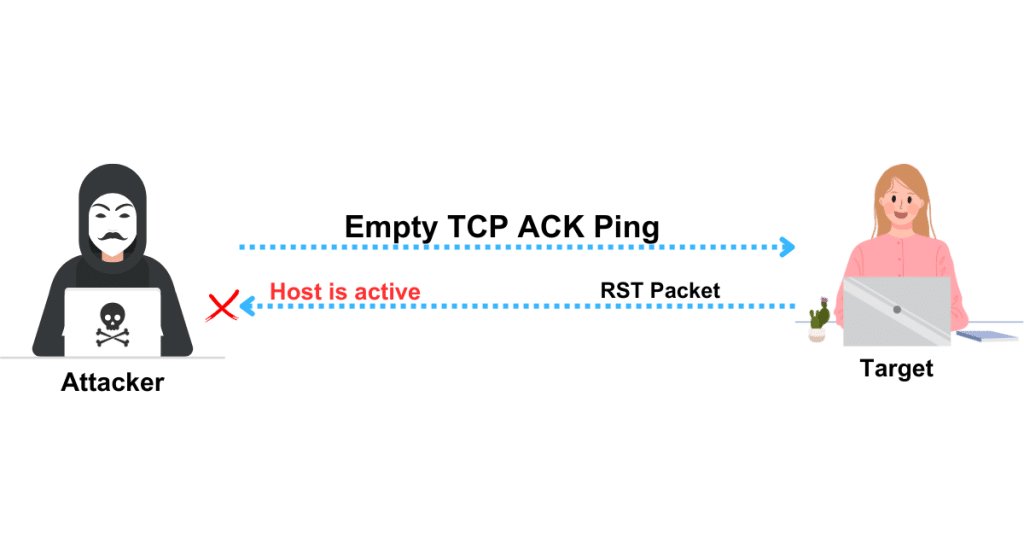
TCP ACK Ping Scan
TCP SYN ping and TCP ACK ping are comparable, albeit with a few minor differences. The standard port 80 is also used by TCP ACK ping.
Attackers immediately transmit an empty TCP ACK packet to the target host when using the TCP ACK ping technique.
The target host responds to the ACK packet with an RST flag to end the request because there is no prior connection between the attacker and the target host.
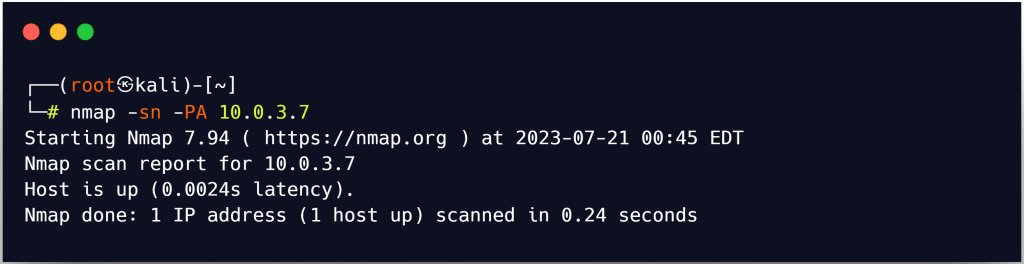
The attacker’s end has received this RST packet, which proves the host is live. To do a TCP ACK ping scan in nmap, use the -PA option.
Advantages of TCP ACK Ping Scan
The SYN and ACK packets can both be utilized to increase the likelihood of getting past the firewall. However, because SYN ping packets are the most used pinging method, firewalls are typically set up to block them.
In these circumstances, the ACK probe can be successfully used to simply get around various firewall rule configurations.
IP Protocol Ping Scan
The most recent host-finding method, IP protocol ping, transmits IP ping packets with the IP header of any designated protocol number. Its format is the same as that of TCP and UDP pings.
This method attempts to send various packets using various IP protocols in the hopes of receiving a response indicating that a host is online. When no protocols are provided, several IP packets for ICMP (protocol 1), IGMP (protocol 2), and IP-in-IP (protocol 4) are automatically delivered.
Change DEFAULT_PROTO_PROBE_PORT_SPEC in nmap. h during compilation to configure the default protocols. Only the IP header data needs to be provided with the packets for all other protocols; specialized protocols like ICMP, IGMP, TCP (protocol 6), and UDP (protocol 17) require the necessary protocol headers to be included.
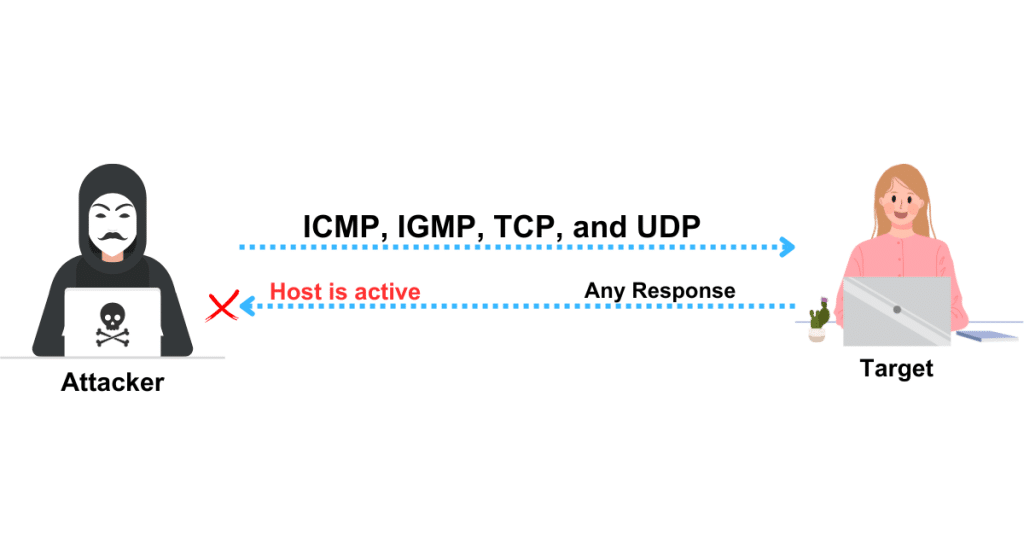
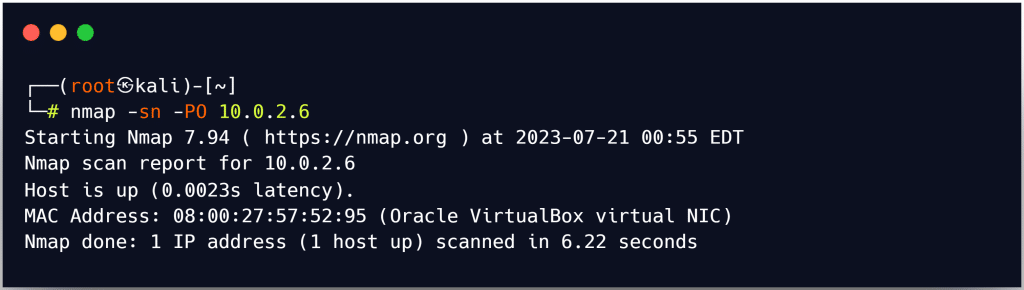
In essence, attackers bombard the target host with a variety of probe packets using several IP protocols; any response from a probe shows that a host is online. The -PO option in Zenmap is used to run an IP protocol ping scan.
Ping Sweep Tools
To find the active systems, ping sweep tools ping the complete range of network IP addresses. The following ping sweep programs allow you to identify active hosts on the target network by simultaneously making several ICMP ECHO queries to various network hosts.
Angry IP Scanner
An IP address and port scanner are called an Angry IP scanner. It can scan any range of IP addresses and any port on those addresses.
It pings each IP address to see if it is still active; if it is, it may also resolve the hostname, ascertain the MAC address, scan the ports, and perform other operations. With plugins, more information is obtained about each host.
Additional capabilities of angry IP scanners include NetBIOS data (machine name, workgroup name, and presently logged-in Windows user), favorite IP address ranges, web server identification, and programmable openers.
The tool enables users to save the scan findings as IP-Port list files, CSV, TXT, or XML files.
It employs a multithreaded strategy to speed up the scanning process, creating a distinct scanning thread for each scanned IP address.
If you have any queries regarding the above content, or you want to update anything in the content, then contact us with your queries. You can directly post your question in the group.
Connect with us on these platforms