Hello everyone, lucifer here for discussing the steps and processes of hacking methodology according to the ethical hackers. how they can beat hackers from proceeding with any type of cyber attack.
In simple terms, hacking methodology defines the steps and process of defending or attacking any type of cyber attack against someone individual, or organization.
It is the same process as an attacker follows but here the only difference is the ethical hacker hacking goals and strategies.
Following the steps of the hacking methodology process will help an ethical hacker to understand the various phases of hacking followed by the real hacker to achieve their wrong objective.
It will also help an ethical hacker or security researcher by learning various types of hacking techniques, tactics, and tools used by the attacker at the various phase of hacking.
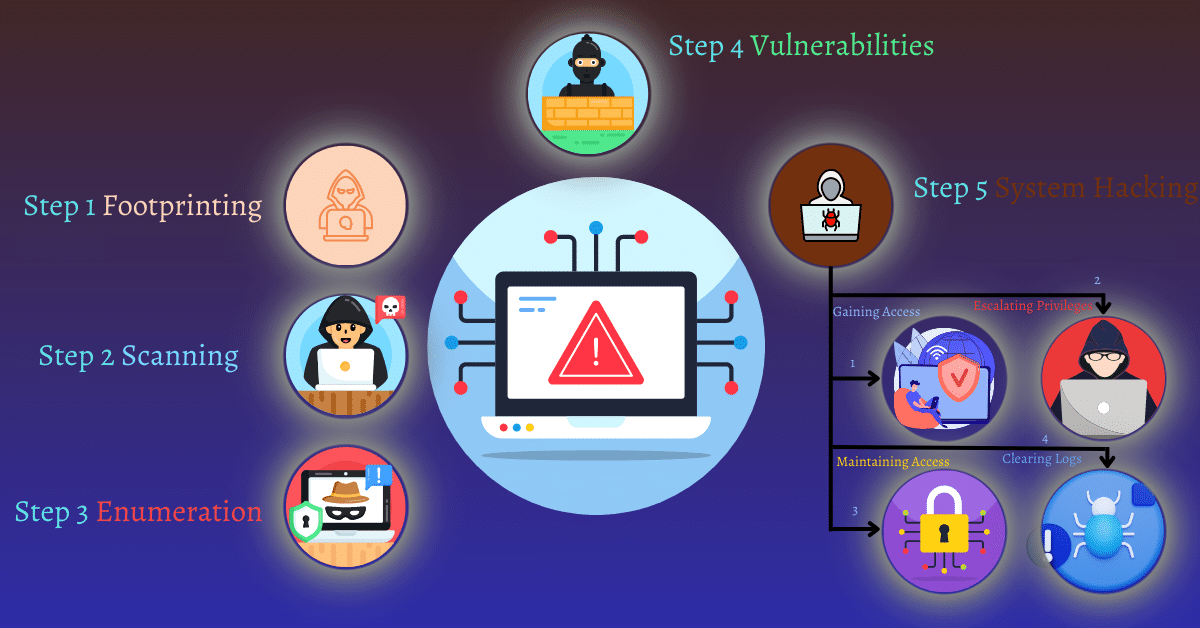
Steps in Hacking Methodology
According to the hacking methodology, these are the various steps and phases involved in hacking:
- Footprinting
- Scanning
- Enumeration
- Vulnerability Analysis
- System Hacking
- Gaining Access
- Escalating Privileges
- Maintaining Access
- Clearing Logs
Let’s discuss all these steps in brief:-
Footprinting in hacking methodology
Footprinting is also known as reconnaissance in which an attacker or security researcher gathers as much information as possible about the target for understanding their digital environment. it will help an attacker in the future for a successful attack.
The main goal of this phase is to gain a comprehensive understanding of the target system or network including its network infrastructure and its vulnerability.
This information can help an attacker for launching successful various types of cyber attacks like social engineering attacks, phishing attacks, or network attacks.
In the phase of footprinting, an attacker creates a profile of the victim’s organization or individual to obtain information like their network IP address ranges, their namespace, and their employee detail. which will further help the attacker for a successful social engineering attack.
It will also help the attacker in finding any known vulnerabilities inside the victim’s network or organization.
For example, an organization’s website may provide employees biographic or a personal details directory that can be used by the hacker for social engineering attacks on the employees of that company.
It is also known as the first phase of hacking which is information gathering which target includes the target organization’s clients, employees, operations, networks, and system details.
To defend your organization against footprinting you can apply many measures such as doing regular vulnerability assessment and penetration testing as well as implementing strong access control and security measures.
it is also important to monitor and analyze network traffic for any suspicious activity and to establish policies and procedures for responding to cyber-attacks.
Scanning hacking methodology

This is also known as the second phase of hacking which includes the identification of the victim’s networks like their open ports, active host, what type of service they are running on their ports, or any type of unnecessary service enabled on particular hosts.
In this phase, an attacker uses the information that he gathered in the first phase of footprinting Which results in successful scanning attacks against the target victim’s network.
Scanning is the logical extension of active reconnaissance; in fact, some experts do not differentiate scanning from active reconnaissance. but active reconnaissance and scanning have a slight difference which is scanning involves more in-depth probing by the attacker.
Often the reconnaissance and scanning phases overlap, and it is not always possible to separate them.
The main goal of the scanning phase is to identify the victim’s network by using some network scanning tools.
This phase is typically used for scanning ports and getting their open port details and service details of servers and finding any vulnerability in their system or network which can be used to plan and execute the cyber attacks on the victim system or network.
Enumeration in hacking methodology
Enumeration is the third phase in ethical hacking which is used to gather detailed information about the target system or network that can be used to identify vulnerabilities weaknesses and potential targets for further exploitation.
Enumeration can be performed by making an active connection with the victim’s network for scanning their open port services and application details.
Enumeration is the method of intrusive probing through which attackers gather information such as network user lists, routing tables, security flaws, shared users, groups, applications, and banners.
Here we can say that enumeration involves active reconnaissance techniques, which include scanning for open ports, running services, and active applications, and using a specialized tool to query the target system for information.
It can also help attackers in exploiting any known vulnerabilities and weaknesses in the target system to gain deeper access and controls.
To defend ourselves from the enumeration phase we can implement some important rules and techniques in our network such as strong access control and security measures that include firewalls, intrusion detection systems, two-factor authentication for our users, and monitoring our network traffic and logs for any type of suspicious activities.
Vulnerability Analysis in hacking methodology
Vulnerability analysis is known as vulnerability assessment which is the process of identifying security threats, vulnerabilities, or weaknesses in a system network or application and assessing the potential risk that these vulnerabilities pose to the security and integrity of the system data.
In the process of vulnerability assessment, we can recognize, measure, and classify security vulnerabilities in a computer system or network and communication channels.
In the case of an attacker, he/she will perform a vulnerability analysis of the target system or network for identifying security loopholes in the organization’s network and computers.
Identified security loopholes can be used by the attacker for future attacks and exploitation on the target system and network.
Vulnerability analysis can be performed by many types of techniques which includes manual testing, automated vulnerability scanning, and penetration testing.
The first step in the vulnerability analysis is to identify the vulnerability, then in the next step access the potential risk and impact of the vulnerability, and then prioritize them based on their severity and likelihood of exploitation.
In the final step, you need to develop a strategy for mitigating the identified vulnerability and reducing the risk of security breaches which can involve implementing security patches and update to the application network or system.
System Hacking in hacking methodology
This is the phase from where an attacker starts attacking the targeted system for gaining initial access after the scanning phases, the information that the attacker got there will be used here for attacking the targeted system.
In the first three-phase attacker obtained the information during the footprinting, scanning, enumeration, and vulnerability analysis. In this phase now attacker uses that information for the attacks he’s going to perform on the targeted system or network.
The hacking methodology of System hacking is further divided into four phases that are:
- Gaining Access
- Escalating Privileges
- Maintaining Access
- Clearing tracks logs
Gaining Access
This is the phase where attackers attack the system in real-time which means here that hacking is going to happen. In the previous phases, the attacker got information about the targeted system security loopholes, vulnerabilities, and security tactics.
In this phase, the attacker will use all the information to exploit the vulnerability in the targeted system, which can include techniques like password cracking, exploitation of the vulnerability, including buffer overflow, and gaining access to the target organizational system.
Gaining access is the term that refers to obtaining access to the operating system or any application on the targeted system or network.
Gaining access to the targeted system or network is a very challenging task for the hacker because it always depends on several factors like system security architecture or security configuration of the targeted system.
The attacker needs to get the initial level of access to the targeted system. Then he needs to carry out the attack for getting root-level access. When an attacker gets initial access to the targeted system then they need to attempt to escalate privileges to obtain complete control.
Escalating Privileges
After getting an initial level or low-privilege user account access to the targeted system. Then the attacker needs to increase their privilege to the administrator level to perform, protected system operations.
so they can proceed to the next level of the system hacking phase, which is the execution of applications that can only be done by the admin-level access of the system. now the attacker will exploit some known vulnerabilities for escalating the user privileges.
Maintaining Access
After getting the administrator or root-level access to the targeted system then the attacker needs to maintain the access for a long time.
The attacker can use both systems for further attacks like he can use both systems or their resources to perform highly intensive scanning or exploitation of the targeted system or networks.
Now the attacker can use the zombie system as the launchpad to launch any type of heavy scanning process and exploit their network, this can be done by maintaining a low profile during the exploitation.
These actions can cause significant damage to the targeted system and network because of getting the root level access of the victim system.
Because of root-level access, an attacker can upload, download, or manipulate data, applications, and configuration on the target system and also use malicious software to transfer username passwords, and any other information stored in the system.
Once the attacker is able to know the vulnerable point or loopholes of the system from which he entered then for maintaining long-time access he can be able to close the vulnerability to prevent other hackers from exploiting them.
For doing this attacker needs to patch the vulnerability which he exploited, after patching attacker will use the compromised or zombie system for launching further attacks without getting affected by other hackers.
Clearing Tracks Logs
After the attacker got what he wants or after completing all his tasks, then he needs to take himself out of the compromised system to remain undetected by the forensic of that victim.
The attacker needs to erase all the tracks and evidence of security compromise from that system.
To perform the clearing of logs attackers can modify or delete logs in the system using certain log-wiping utilities that remove all evidence of their presence.
Further attackers can delete all the malware and malicious software which he installed in the targeted system for gaining For more information about that organization.