Hello everyone lucifer here, and today in this article we are going to discuss cyber kill chain methodology which is used by security researchers to prevent any type of cyber attacks.
The cyber kill chain methodology is a framework developed for securing cyberspace based on the concept of a military kill chain. it is also known as the component of intelligence-driven defense for the identification and prevention of malicious intrusion activities into the system or network.
It will help security researchers in identifying the process and steps that attackers follow to complete their goals.
Cyber Kill chain
The main goal of the cyber kill chain methodology is that actively enhance intrusion detection systems and response to any type of cyber attack.
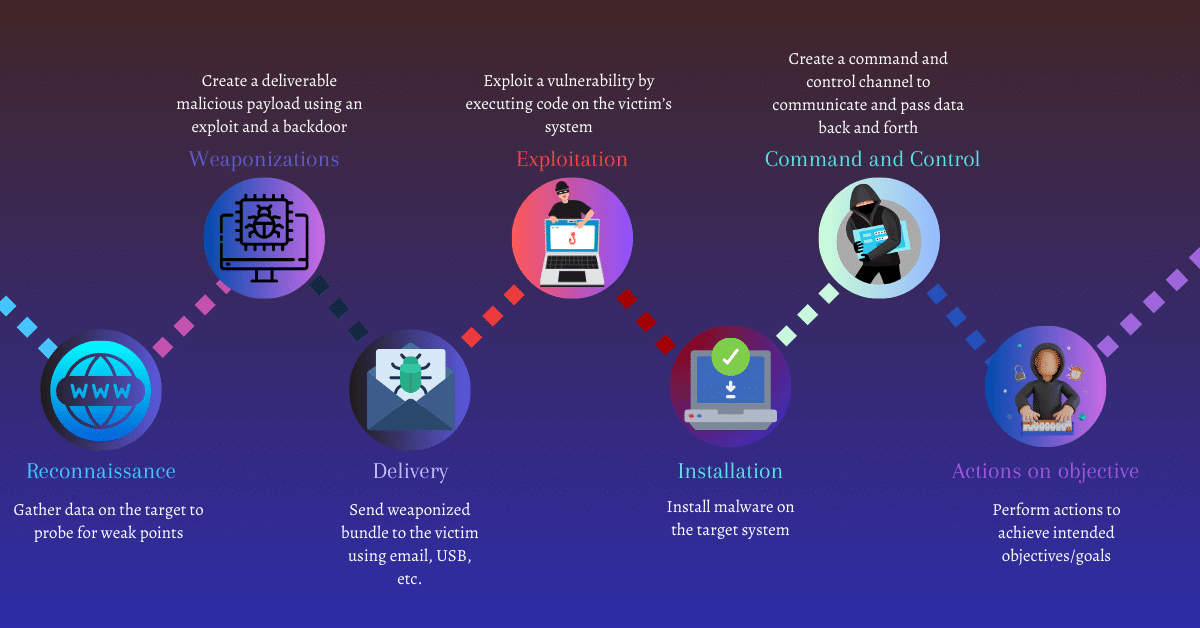
This methodology contains 7 phases of protection mechanisms to mitigate and reduce the cyber threat against any type of cyber attack on the system or network.
According to Lockheed Martin, cyber attacks might occur in 7 different phases from reconnaissance to the final accomplishment of the objective.
So the cyber kill chain methodology helps security researchers or professionals to reduce the security risk at the different stages of a security attack and helps them to prevent the attack before it proceeds at any stage or phase.
Phases of cyber kill methodology
There are total 7 phases in the cyber kill chain methodology that re:-
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and control
- Actions on objectives
Reconnaissance
It is also known as the first phase of hacking in which an attacker performs reconnaissance on the target for collecting as much as information about the target which will help the attacker for doing future attacks on the victim’s system.
The information collected by the attacker is the publicly available information on the Internet like network information, system information, or organizational information of the target.
By performing reconnaissance on the target network an attacker can gain information such as their network blocks, specific IP addresses, their open ports and closed ports, port services, and employee detail.
For getting this information on the target an attacker can use some automated tools to obtain information on the targeted network servers, services, vulnerabilities in applications, and any type of default login credentials about the targeted network and systems.
all this information can help attackers in gaining backdoor access to the target network
Activities performed by an attacker in the phase of reconnaissance include the following:
- Gathering publicly available information about the target organization with the help of the Internet or through social engineering
- Performing analysis of various online activities and publicly available information
- Gathering information from social networking sites and web services
- Obtaining information about websites visited
- Monitoring and analyzing the target organization’s website
- Performing Whois, DNS, and network footprinting
- Performing and scanning to identify open ports and services
Weaponization
This is the second phase where an attacker analyzes the data collected in the previous stage for identifying any type of known vulnerabilities and techniques that can be useful for exploiting and gaining unauthorized access to the target network.
Based on the data available from the vulnerabilities identified during analysis, the attacker selects a vulnerability to create a tailored deliverable malicious payload (remote access malware weapon) using an exploit and backdoor to send it to the victim.
An attacker can target any specific network device, operating system, endpoint device, or even individual within the organization to carry out their attack. this can always be dependent upon what type of vulnerability the attacker got during the analysis phase.
For example, an attacker may send a phishing email to the employee of the target organization which may include a malicious attachment such as a virus or worm, that can be resulted in installing a back door on the system that allows remote access to the attacker when downloaded and installed by the person who got the mail.
The following are the activities that can be performed by the attacker during the weaponization phase:-
- Identifying appropriate malware payload based on the analysis
- creating new malware payload or selecting, reusing, and modifying the available malware payload based on the identified vulnerabilities
- creating a phishing email campaign
- leveraging exploit kits and bot Nets
Delivery
As in the previous phase, we created malware or a backdoor for the known vulnerability in the targeted system now it’s time to deliver those payloads to the victim system.
The delivery phase mainly focuses on delivering the weapon we created as the payload to our victim system for exploiting it.
The payload can be transmitted to the intended victim as an email attachment, or malicious link on the website, or through a vulnerable web application or USB drive.
In this stage, we can measure the effectiveness of the defense strategies implemented in the target organization on whether the intrusion attempt of the attacker is blocked or not.
The attacker can perform the following activities that are:
- Sending phishing emails to the employees of the target organization
- Distributing USB drives containing malicious payloads to employees of the target organization
- Performing attacks such as watering holes on the compromised website
- Implementing various hacking tools against the operating system application and servers of the target organization
Exploitation
After the delivery phase our weapon is successfully transmitted to the intended victim now in this phase the exploitation triggers the attacker’s malicious code to exploit the vulnerability in the operating system application or server on the target system.
In this stage, a targeted organization may face threats such as authentication and authorization attacks, arbitrary code execution, physical security threats, and security misconfiguration.
An attacker can include the following activities during the exploitation phase:
- exploiting software or hardware vulnerabilities to gain remote access to the target system
Installation
The attacker downloads and installs malicious software on the target system to maintain access to the target network for an extended time. The attacker can install a back door to gain remote access to the targeted system.
After the successful exploitation of the malicious code to the targeted system an attacker can be able to spread the infection to the other system in the network.
It is also necessary for the attacker for hiding their presence of malicious activity from the security controls like firewalls using various techniques such as encryption.
These are the following activities can we perform by the attacker in the phase of installation
- Downloading and installing back doors from malicious software
- Maintaining and gaining remote access to the targeted system
- Applying various methods and tactics for keeping the back door hidden and running in the targeted system
Command and control
In this phase, an attacker creates a command and control channel for establishing two-way communication between the victim’s system and the attacker-controlled server to communicate and pass the data back and forth.
The attacker implements techniques such as encryption to hide the presence of such channels. By the use of the channel, an attacker can perform remote exploitation on the target system or network.
these are the following activities that can be performed by the attacker during the command and control phase:
- establishing the two-way communication channel between the victim system and the targeted control server
- leveraging channels such as web traffic, email communication, and DNS message
- applying privilege escalation techniques
- hiding any evidence of compromise using techniques such as encryption
Actions on Objective
In this face, an attacker controls the victim’s compromised system from a remote location which results in accomplishing the attacker’s intended goals.
Now the attacker can gain access to confidential data to disrupt the service or network or destroy the operational capabilities of the target by gaining access to its network and compromising more systems.
the attacker can use this as a launching point to perform other attacks.