Blog
What is deep web, dark web and surface web?
- by Team Ciphers Security
- January 8, 2023
- 0 Comments
Blog
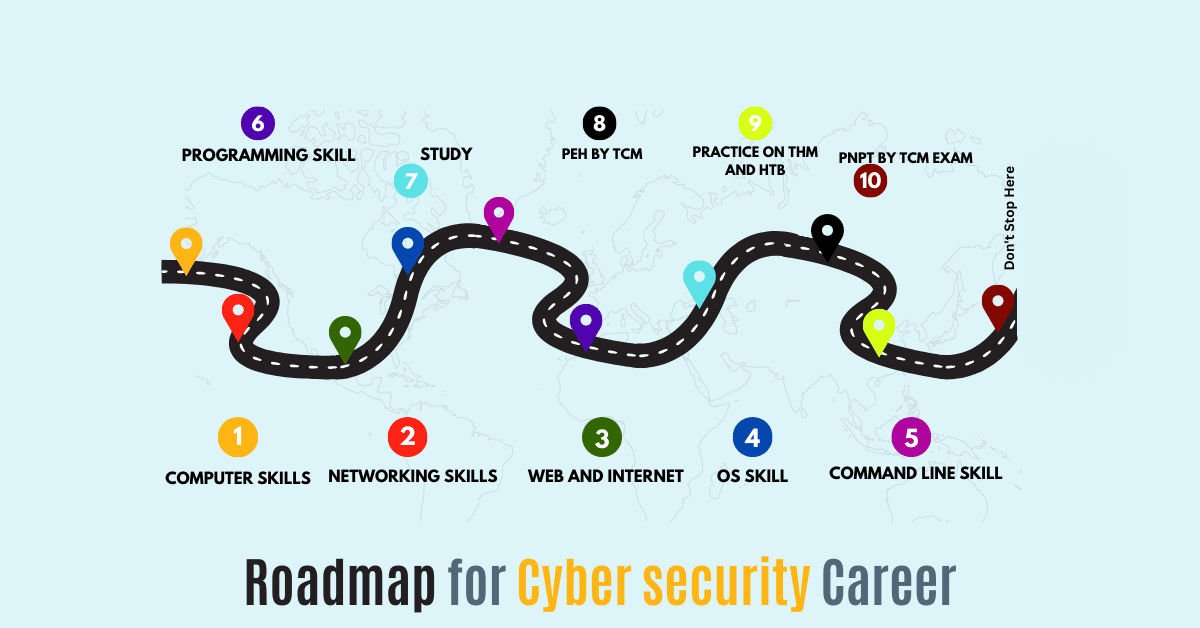
How to start a career in Cyber Security in 2025
- by Team Ciphers Security
- December 22, 2022
- 0 Comments
Tools
Blog
How to use NMAP for penetration testing
- by Team Ciphers Security
- December 21, 2022
- 0 Comments