Hello, everyone lucifer is here to discuss a very important topic in information security which is the classification of security attacks. That means how many types of information security attacks are there.
This article will help you to classify security attacks and understand how they are working as a threat to our network security.
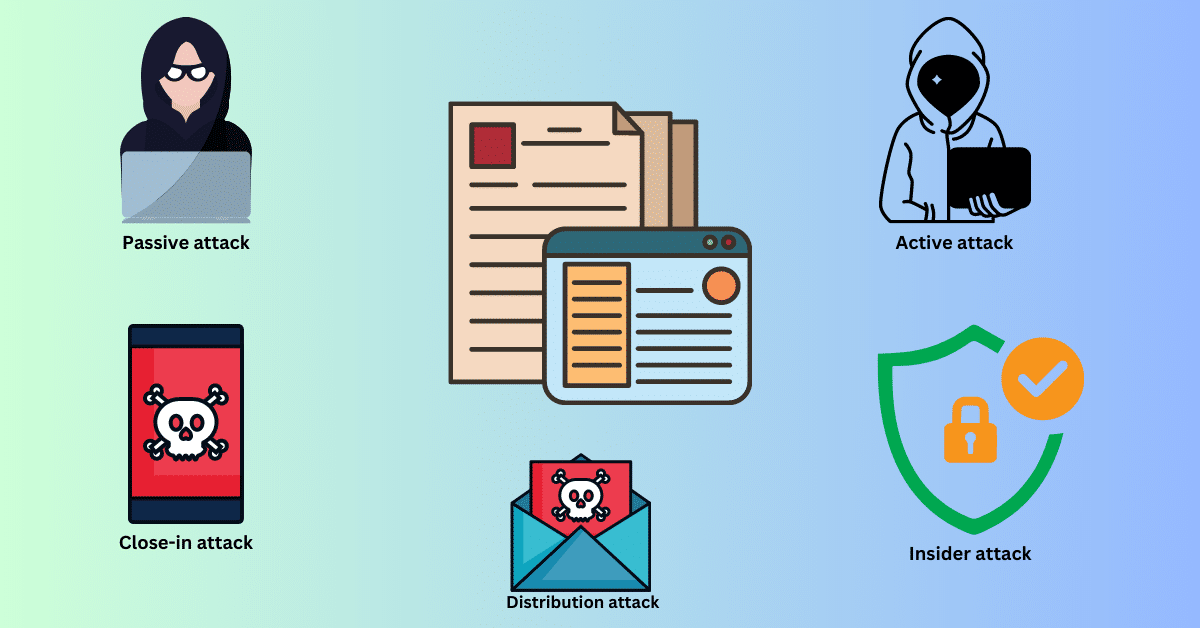
Security attacks are a major threat, or we can say the risk to our network security. Information security attacks are classified into 5 major types that are listed below:-
- Passive Attack
- Active Attack
- Close-in Attack
- Insider Attack
- Distribution Attack
Let’s discuss these attacks in brief:
Passive Attack

This attack is used to monitor data and network traffic without affecting any system and its resources. In a passive attack, the attacker only intercepts the data that is being transmitted over the victim’s network without any alteration in the data.
It is also a very useful attack for information gathering on a particular victim’s system gathering information like login credentials, sensitive data, or other information that could be used in future attacks.
A passive attack is very difficult to detect because the attacker has no active connection with the victim’s system or network.
This attack is helpful for attackers for getting information like unencrypted data in transmit, clear-text credentials, or other sensitive information that is useful in performing active attacks.
Examples of passive attacks:
- Footprinting
- Sniffing and eavesdropping
- Network traffic analysis
- The decryption of weakly encrypted traffic
Active Attack
Active attack with it’s it is clear that this attack involves active techniques and procedures for disrupting someone’s data.
This attack technique is used for altering data on the network in real-time while it is being transmitted between the users. with this attack, an attacker is able to modify, disrupt, or destroy data that is being transmitted over the network or system.
An attacker can launch an active attack on the victims’ system or network by actively sending traffic that can be detected. this attack is performed on the target network to exploit the information in transit.
The attacker always penetrates or infects the target’s internal network and gains access to a remote system to compromise the internal network.
Examples of active attacks:-
- Malware attacks
- Denial-of-service (DoS) attack
- Man-in-the-middle (MITM) attack
- Spoofing attack
- DNS and ARP Poisoning
- Profiling
- Arbitrary code execution
- Backdoor access
- Cryptography attacks
- SQL injection
- XSS attack
Close-in Attack
This attack is performed when the attacker has physical access to the victim’s computer or network. This allows the attacker to bypass the security controls and gain unauthorized access to sensitive information or systems.
The purpose of this attack is to gather or modify the information or disrupt its access. for example, an attacker might shoulder surf user credentials. An Attacker gains close accessibility through secret entry, open access, or both.
Close-in security attacks can be very difficult to detect because attackers involving in physical access to the system or network.
We can take several security measures to mitigate the risk of a Close-in Security attack:
- Implementing strong access controls
- restricting physical access to sensitive systems and server area
- Always monitoring system and network traffic for any unauthorized activity
Organizations must have very comprehensive security plans that include measures to address close-in security attacks, as well as other types of security threats.
Examples of Close-in security attacks:-
- A malicious USB insertion attack
- Shoulder Surfing
- Social engineering
- Tailgating
- Hardware attack
Insider attack
An insider security attack is a security breach that is performed by the trusted persons of the organization who have physical access to the company’s or victims’ systems, networks, or servers.
The person that is a current or ex-employees or maybe a friend of the victim who has privileged access to the vulnerable assets of the victim is responsible for an insider attack
Insider attacks can involve access to violates rules or intentionally cause a threat to the organization’s information or information system.
In this attack, an attacker can easily bypass security rules, corrupt valuable resources, access sensitive information, and misuse these assets to affect the organization’s confidentiality, integrity, and availability of the information system.
Insider attack results in an impact on the organization’s business operations, reputation, and profit.
It can be difficult to figure out an insider attack because the attacker has authorized access to the company’s digital assets.
Examples of insider attacks are:-
- Eavesdropping and wiretapping
- Theft of physical devices
- Social engineering
- Data theft and spoilation
- Pod slurping
- Planting keyloggers, backdoors, or malware
Distribution attacks
A distribution security attack can be performed by tampering with the hardware or software prior to installation. It can also be done by spreading malware or malicious content to numerous systems or users.
It has serious consequences for organizations and individuals, as it can result in stolen data, financial loss, and system or network compromises.
Distribution attacks can be done by inserting malware into legitimate software programs, such as their popular application or plugin, then distributing the infected programs to the users.
After the users download and install the infected programs, then the user inadvertently installs the malware into their systems. And it turns their system infected and accessible to the attacker for performing future attacks.
examples of distribution attacks :
- Email phishing
- Malicious websites
- Watering Hole attack
- Infected software attack
- Drive-by downloads
- Backdoors
Note:-
Distribute attacks can be done as
- Modification of software or hardware during production
- modification of software or hardware during distribution