Hello everyone, today in this article we are going to discuss cyber threat intelligence, what is it, and how it helps a security researcher, in the real-life scenario for analyzing threat behavior.
So basically, the word threat is defined as the possibility of a malicious attempt to damage or disrupt a computer network or system.
A threat is known as an occurrence of an unusual activity that is intended to damage and interrupt the operational and functional activities of an organization.
It can affect the integrity and availability factor of an organization. The impact of threats is very great and may affect the state of physical IT assets in an organization.
The threat can be accidental, intentional, or due to the impact of some action.
Cyber Threat Intelligence
Cyber threat intelligence is usually known as CTI, It is the process of collection and analysis of the information about the attacker and threat to draw a pattern that provides an ability to make decisions for preparedness, prevention, and response action against various types of cyber attacks.
CTI can be known as the process of recognizing or discovering any unknown threats that an organization may face from an attacker before a necessary defense mechanism can be applied to avoid such an occurrence.
It involves collecting, researching, and analyzing security trends, and technical development in the field of cyber threat (including cybercrime, hacktivism, and espionage).
Getting prior knowledge about the threat may help the organization in planning and decision-making to handle the threat impact, which is a piece of threat intelligence.
The main purpose of CTI is to aware everyone of the existing or emerging threats and prepare them to develop a proactive cyber security posture in advance of exploitation.
The process where any unknown threat that converted into a possibly known threat, helps an organization to anticipate the attack before it happened, which leads to a better and more secure system.
Threat intelligence can be useful in achieving secure data sharing and global transactions among organizations.
The threat intelligence process can be used to identify the risk factor data responsible for malware attacks, SQL injections, web application attacks, data leaks, phishing, denial-of-service attack, and other cyber attacks.
Threat intelligence is very useful for an organization to mitigate any type of cyber threat attack with effective planning and execution.
Along with threat analysis, cyber threat intelligence also strengthens the organization’s defense system, creates awareness about impending risk, and aids in responding against such risk.
Types of cyber threat intelligence
Cyber Threat Intelligence is the theoretical information that describes the behavior of the threat and guides the organization in making various defense decisions. The information about threats is extracted from a huge collection of sources and information.
Cyber Threat Intelligence provides operational insights from outside the organization for issuing alerts on emerging threats to the organization.
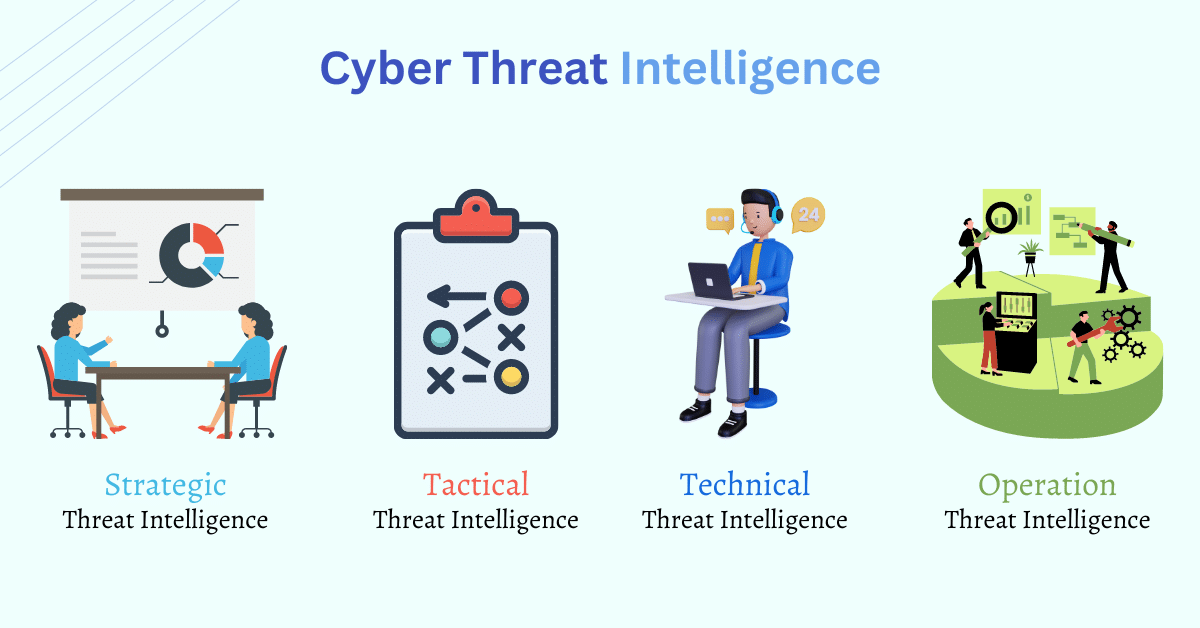
For the better management of information that is collected from different sources, it is important to subdivide threat intelligence into 4 different types. these subdivisions are performed based on the consumer goals of the intelligence.
Threat intelligence is generally divided into 4 different types that are:-
- Strategic threat intelligence
- Tactical threat intelligence
- Operational threat intelligence
- Technical threat intelligence

Strategic threat intelligence
It provides high-level information about cyber security posture, and threats, details about the financial impact of various cyber security activities, attack trends, and the impact of a high-level business decision.
This information is consumed by the high-level executives and management of the organization, such as IT management and CISO.
This will help the management to identify current cyber threat risks, unknown future risks, threat groups, and attribution of breaches.
The report obtained from the intelligence will provide a risk-based view for focusing on the high-level concepts of risk and their probabilities.
Strategic threat intelligence deals with long-term issues and provides real-time alerts for threats to the organization’s critical assets, which includes IT infrastructure, employee, applications, and customers.
Strategic threat intelligence is generally used by the management team of an organization to make a strategic business decision for analyzing the threat effect.
Based on the analysis, the management team will allocate staff and a sufficient budget to protect the company’s critical IT assets.
The general strategic threat intelligence includes the following information
- the financial impact of cyber activity
- risk and impact of data breaches and any intrusions
- Attack trends and threats actor
- statistical information on data breaches, data theft, and malware
- cyber attack that involves geopolitical conflicts
- information on how attacker TTPs changeover time
Tactical threat intelligence

Tactical threat intelligence is very useful in protecting the organization’s resources. It gives information about the Tactic, technique, and procedure used by a threat hacker to perform the attack.
It is used by cyber security researchers or professionals that include IT service managers, security operations managers, network operation center (NOC) staff, administrators, and security architects.
Tactical threat intelligence helps the security researcher in understanding, how the attacker will be able to perform their attack on the organization.
It also helps to identify the problem of information leakage from the organization and assess the technical capabilities and goals of the advisory with their attack vectors.
By using tactical threat intelligence security professionals can develop, detect and mitigate strategies for reducing the threat risk by applying security patches and updating security products with identified indicators, and patching vulnerable systems.
The data collected in tactical threat intelligence is generated from campaign reports, malware, incident reports, attack group reports, and human intelligence, among other information.
The Intelligence Report can be obtained by reading white or technical papers, communicating with other organizations, or purchasing reports from any 3rd party vendors.
this intelligence information is highly technical that includes topics like malware, campaign, techniques, and tools in the form of a forensic report.
Operational Threat Intelligence

Operational threat intelligence is useful for getting information about Any is specific threats against the organization.
It helps security professionals for getting information about security events and incidents that helps them in defending and disclosing the potential risk, it will also aware them with insights into the attacker’s methodology, identify past malicious activities, and perform investigation on malicious activity in a more efficient way.
This threat intelligence is used by security managers and heads of incident response, network defenders, security forensics, and fraud detection teams.
It will help an organization in understanding the possibility of threat attackers and their intentions, capabilities, and opportunity to attack vulnerable IT assets and the impact of a successful attack.
In some cases, only government organizations have the authority to collect this type of intelligence information.
Doing so helps incident response and forensic teams to deploy security assets to identify and stop upcoming attacks, improve early-stage attacks, detect capabilities, and reduce attack damage to IT assets.
The intelligence information used in this threat intelligence can be generally collected from the sources like humans, social media, and chat rooms; it can also be collected from real-world activities and events that can result in a successful cyber attack.
The operational threat intelligence information can be obtained by analysis of human behavior, threat groups, and by similar means.
This information will help an organization to prevent and predict any future cyber attack and help in enhancing its incident response plan and mitigation strategies.
operational threat intelligence can be shown as a report that contains identified malicious activity, recommended courses of action, and warning of emerging attacks.
Technical Threat Intelligence
This threat intelligence will help security researchers or professionals for getting information about the resources used by an attacker to perform the attack. This will include command and control channels, tools, and other items that are used in the attack.
Threat intelligence has a shorter lifespan as compared to tactical threat intelligence because it mainly focuses on specific IOCs.
It provides rapid distribution and response to threats. for example, a piece of malware used to perform an attack in tactical threat intelligence, whereas the detail related to the specific implementation of the malware comes under technical threat intelligence.
Other examples of technical threat intelligence include the specific IP addresses and domains used by malicious endpoints, phishing email headers, and checksums of malware, among other details.
This threat intelligence is used by SOC staff and incident response teams.
The intelligence information used in technical threat intelligence is obtained from active campaigns, attacks that are performed on other organizations, or data feeds provided by external 3rd parties.
This information is generally collected as a part of an investigation of attacks performed on various organizations.
This information helps security researchers to add the identified indicator to the defensive system such as IDs and IPS, firewalls, and endpoint security systems, thereby enhancing the detection mechanism used to identify the attacks at an early stage.
It will also help the security researcher by identifying malicious traffic and IP addresses that are suspected of spreading malware and spam emails in the network.
Thank you for reading this post, don't forget to subscribe!