Hello everyone, in this article we will discuss how we can footprinting any website to find vulnerabilities and loopholes inside it.
The tools and services we are going to use in this section are:-
- Ping command utility
- Photon
- Central Ops
- HTTrack Website Copier
- GRecon
- CeWL
Let’s Start with our first tool
Footprinting through Ping Command Line Utility
Ping command line utility is available in both Windows and Linux systems you can directly access it by going to the terminal of both operating systems.
Ping is a popular command line utility tool used for testing network connections between devices. It will help us in getting the network infrastructure of the victim’s network and domain, and IP address information of the website.
Let’s start with the window’s terminal and our target website will be microsoft.com
1. The first step is to see if the website is active for connection or not by ping command [ping microsoft.com]
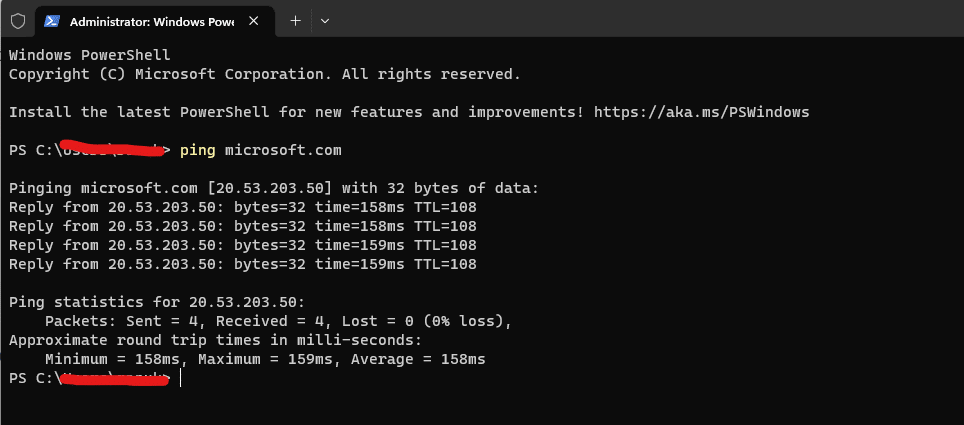
2. Now here we’re getting information about the IP address of our target domain it is showing a response coming from that IP address which is showing that the host server is up and ready for an incoming connection.
3. Now we will apply some filters to the command for some specific result we want [ping microsoft.com -f -l 1500]
Here the -f: refers to the specific setting, not fragmenting flag in the packet, -l: refers to the specific buffer size.
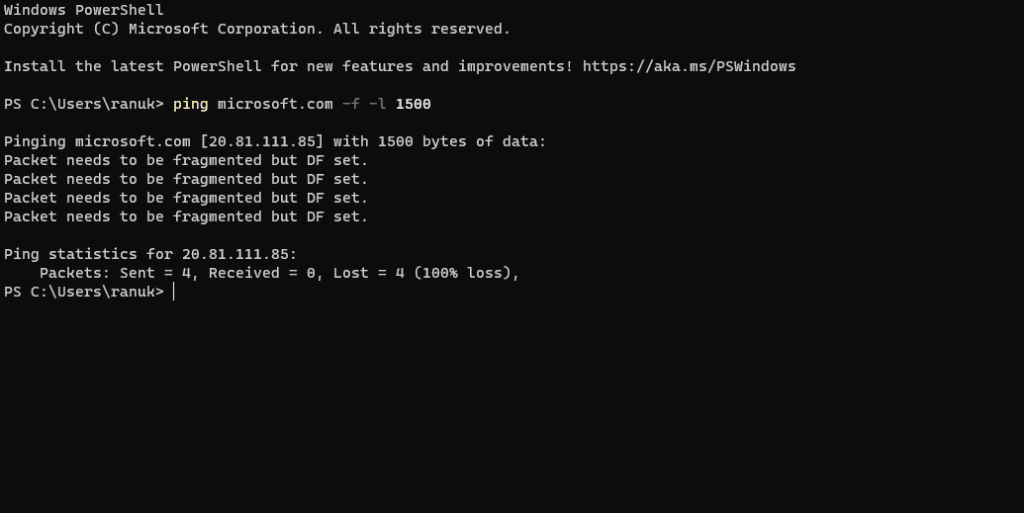
4. here we are seeing that our maximum packet size is less than 1500 bytes now we need to try different values for getting a packet size of more than X bytes and for getting a maximum frame size.
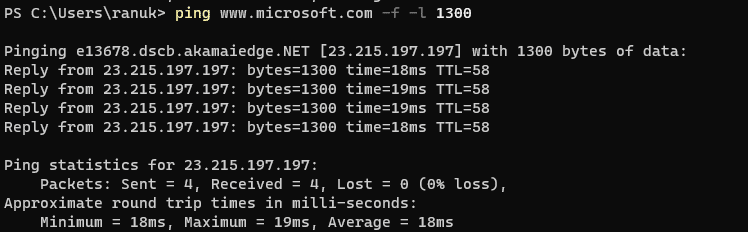
5. now here we’re getting our maximum frame size which is 1300 because microsoft.com is replying with a successful ping at this size. So here it is showing that 1300 bytes is the maximum frame size on this machine’s network.
6. Now we will set TTL for our request for that we will type [ping www.microsoft.com -i 3] this will set the time to live (-i) value as 3. The maximum value you can set for TTL is 255
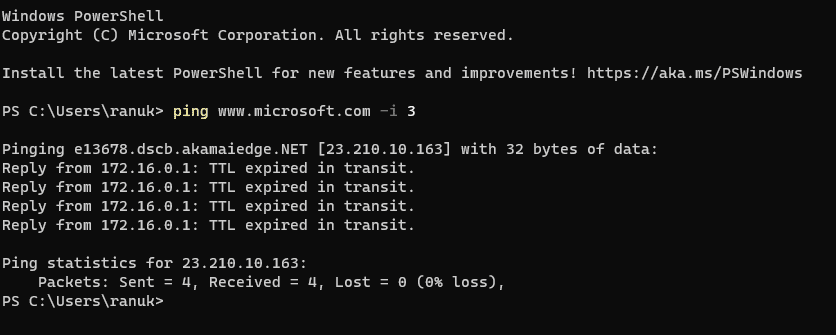
7. here we are getting the reply from microsoft.com as TTL expired in transit which means the router discarded the frame because its TTL has expired (reached 0).
8. Now we will execute a new command where we set the different values for the TTL and number echo request to be sent by typing this [ping www.microsoft.com -i 3 -n 1 ]. Here we are giving the values TTL 3 and -n value to 1 to check the life span of the packet.
Note:- -n specifies the number of echo requests to be sent to the target.
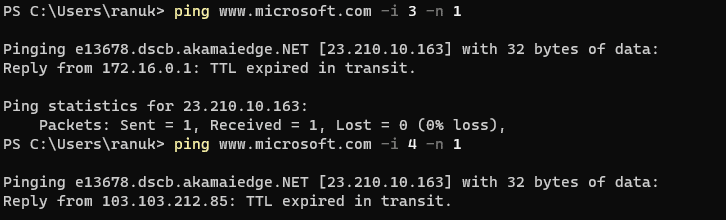
9. now we will change the value of TTL until we get the right one, so now we need to increase the value of -i every time [ping microsoft.com -i (x+1) -n 1]
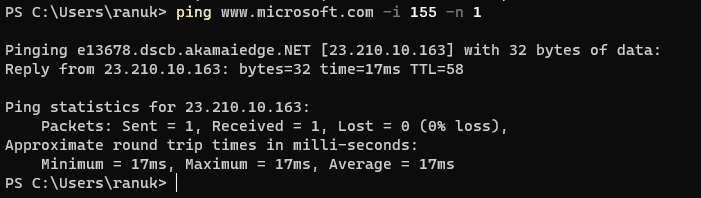
10. Here I got the final TTL value as 155 which is replying from the destination host (microsoft.com)
11. The above session is demonstrating the knowledge about gathering information about the target website using the ping command-line utility tool.
Footprinting through Photon
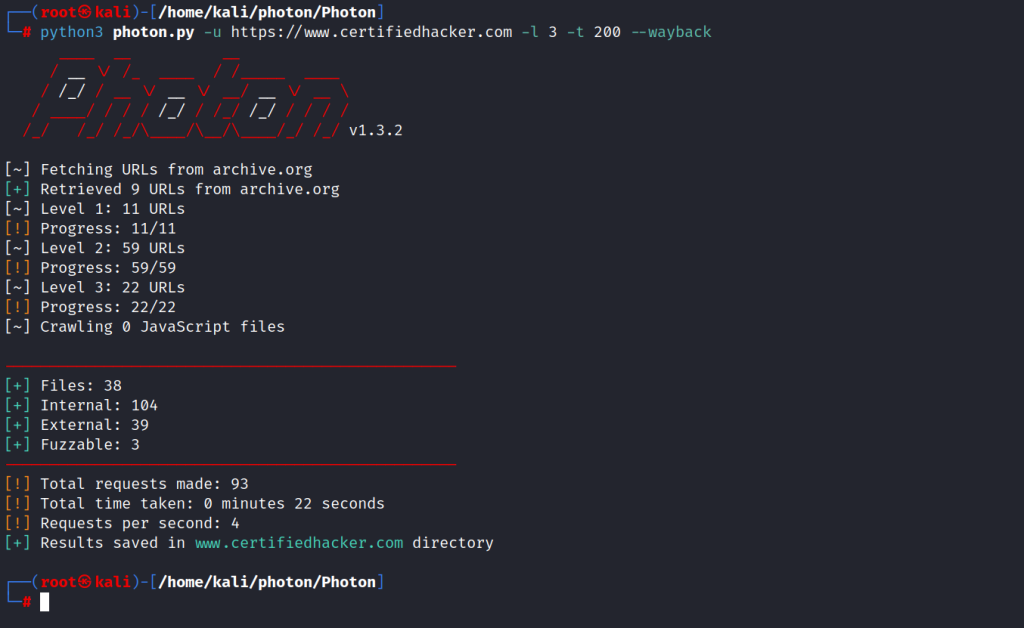
Photon is a command line script developed in Python for gathering information about target urls such as URLs (in-scope and out-of-scope), URLs with parameters, email, Social Media Accounts, Files, Secret keys, and subdomains.
You can export the extracted information in JSON format.
For detailed information about the photon tool and how to install and use it then [click here]
Footprinting through central ops
Central Ops is an online network scanner tool that is used for investigating domains and IP addresses, DNS records, traceroute, nslookup, whois searches, etc.
Here our target website will be Microsoft.com, and we are going to gather information about it by using the central ops online network scanner tool.
1. Navigate to the central ops website [click here]
2. Now type the URL of the target website you want to gather information in the search box referred to as enter a domain or IP address and then click ok
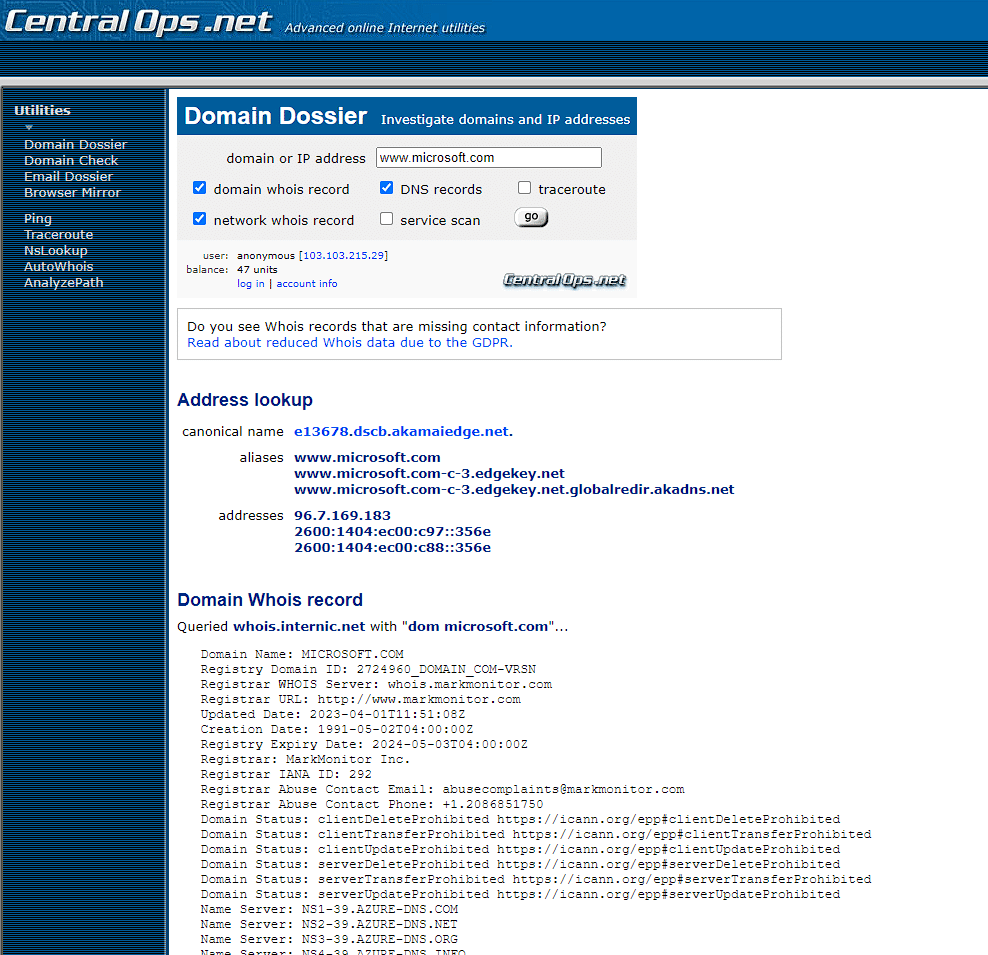
you can scroll down to the page for information such as Network Whois records and DNS records, and other detailed information about the website you want to know.
This is how we can gather information about any website by using the Central Ops online tool.
Mirroring a target website through the HTTrack website copier tool
Website mirroring is the process of making a clone of the original website. This process is helpful in website footprinting by analyzing the cloned website on your local system.
There are many websites mirroring tools available in the market for paid and free. These tools include such as HTTrack Website Copier, HTTrack is an offline browser utility that downloads a website from the Internet to a local directory, builds all directories recursively, and transfers HTML, images, and other files from the web server to another computer.
Now we will use the HTTrack tool to make a clone of the target website and store it in our local system. We are targeting www.certifiedhacker.com as our target. This will help us in analyzing and identifying possible exploits and vulnerabilities.
Now for further steps and detailed information about using and downloading this tool follow this link [Click Here]
Footprinting website with GRecon
GRecon (Greei-Conn) is a simple Python tool that automates the process of Google-Based Recon AKA Google Dorking The current Version 1.0 Run 7 Search Queries (7 Micro-Plugins) on the specified Target Providing Awesome Results.
The current version of Grecon can find information from Google search queries that include:-
- Subdomains
- Sub-Subdomains
- Signup/Login Pages
- Dir Listing
- Exposed Docs
- PDF, XLS, DOCX, etc
- WordPress Entries
- Pasting Sites
- Records in Pastebin, Ghostbin, etc
For more detailed information about this tool such as how to use and install it in Linux OS then [click here].
Thank you for reading this post, don't forget to subscribe!