Learn about some of the technologies used to Extending Your Network out onto the Internet and the motivations for this.
Room Link Extending Your Network
Port forwarding is an essential component in connecting applications and services to the Internet. Without port forwarding, applications and services such as web servers are only available to devices within the same direct network.
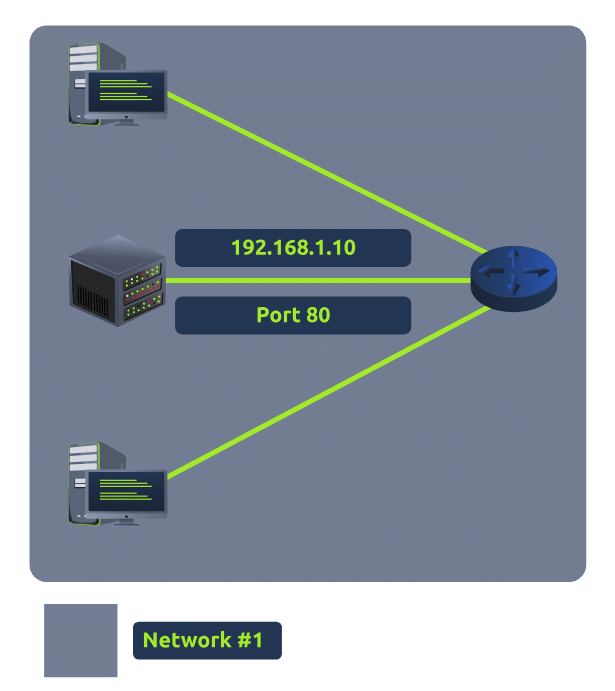
Take the network below as an example. Within this network, the server with an IP address of “192.168.1.10” runs a webserver on port 80. Only the two other computers on this network will be able to access it (this is known as an intranet).
If the administrator wanted the website to be accessible to the public (using the Internet), they would have to implement port forwarding, like in the diagram below:
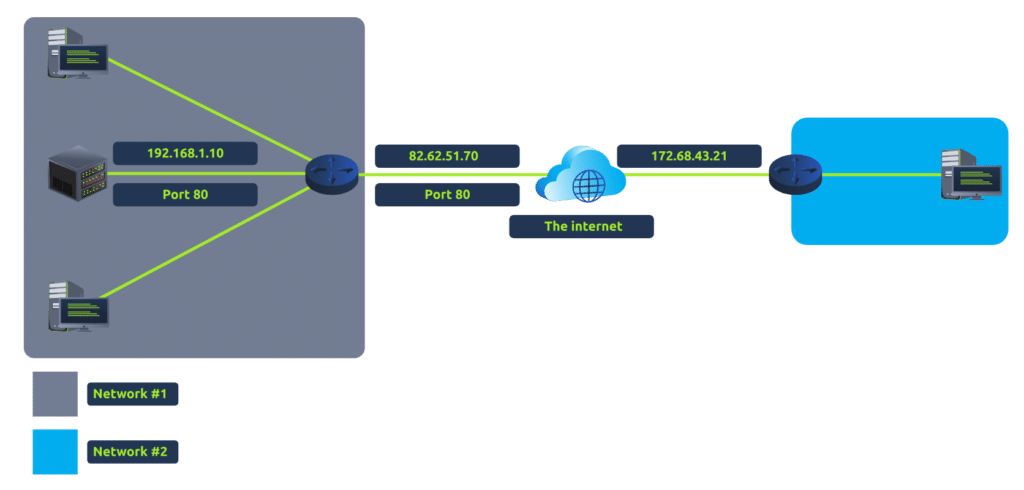
With this design, Network #2 will now be able to access the webserver running on Network #1 using the public IP address of Network #1 (82.62.51.70).
It is easy to confuse port forwarding with the behaviours of a firewall (a technology we’ll come on to discuss in a later task). However, at this stage, just understand that port forwarding opens specific ports (recall how packets work). In comparison, firewalls determine if traffic can travel across these ports (even if these ports are open by port forwarding).
Port forwarding is configured at the router of a network.
Question: What is the name of the device that is used to configure port forwarding?
Answer: router
Task 2 Firewalls 101 Extending Your Network
Question: What layers of the OSI model do firewalls operate at?
Answer: Layer 3, Layer 7
Question: What category of firewall inspects the entire connection?
Answer: Statefull
Question: What category of firewall inspects individual packets?
Answer: Stateless
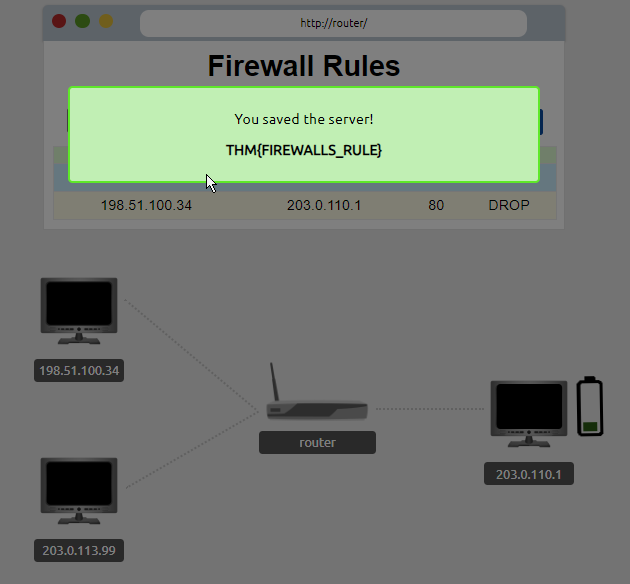
Task 3 Practical Firewall Extending Your Network
Deploy the static site attached to this task. You must correctly configure the firewall to prevent the device from overloading to receive the flag!
Question: what is the flag?
Answer: THM{FIREWALLS_RULE}
Task 4 VPN Basics Extending Your Network
Question: What VPN technology only encrypts & provides the authentication of data?
Answer: ppp
Question: What VPN technology uses the IP framework?
Answer: ipsec
Task 5 LAN Networking Devices
Question: What is the verb for the action that a router does?
Answer: routing
Question: What are the two different layers of switches? Separate these by a comma I.e.: LayerX,LayerY
Answer: layer2,layer3
Task 6 Practical Network Simulator
Question: What is the flag from the network simulator?
Answer: THM{YOU’VE_GOT_DATA}
Question: How many HANDSHAKE entries are there in the Network Log?
Answer: 5
Thank you for reading this post, don't forget to subscribe!