The network scanning tools are commonly used for discovering and identifying live hosts, open ports, running services, on a target network, location info, net BIOS info, and information about all TCP/IP and UDP open ports.
The information we will gather from network scanning tools can be used for creating an active profile of the network infrastructure of the target organization.
These are the list of some standard network scanning tools for PC that we are going to use and explain.
- Nmap
- Hping3
- Metasploit
- NetScanTools Pro
Network scanning tools for mobile devices
- IP Scanner
- Fing
- Network Scanner
Nmap
Nmap’s sort for network mapper is a free and open-source tool for network scanning which is used to discover hosts and services on a computer network and to create a map of the network infrastructure of the target network.
Nmap is widely used for security scans and to identify what service or port that was running on the host server, and it is also known as the information-gathering tool for networks. It is also used for getting information on what type of firewall is used by the host for securing the network infrastructure.
For getting the information from the target server and nmap send specially crafted packets to the target host and then analyze the responses to accomplish its goal. It can scan a very large variety of network connections more than 100 of thousands of machines.
Nmap might have many methods and modules for scanning that includes port scanning (TCP and UDP), OS detection, version detection, ping sweeps, and so on.
This tool is useful for both persons like administrators and attackers as per their specific needs. Most of the time network administrators use this tool for creating network inventory, managing service upgrade schedules, and other monitoring of host or service uptime.
An attacker can use this tool as for getting the network infrastructure detail of the target organization these detail includes the live host on the network, open ports, and active services, type of filters or firewalls, MAC details, OS detail along with their version details.
the common syntax for using the nmap tool is that
nmap <option> <Target IP address> 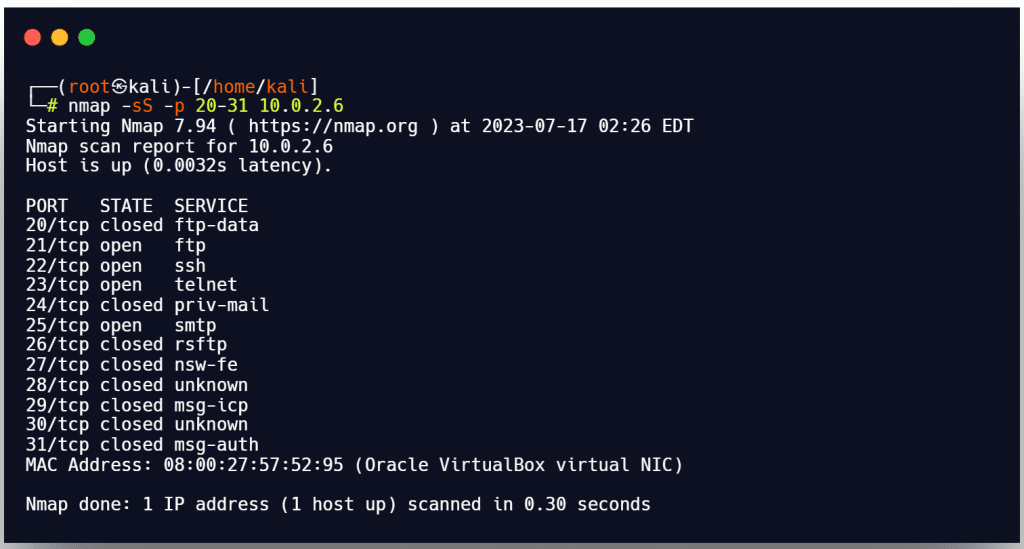
For more detail about the Nmap tool [click here]
Hping3
Hping3 is a command line-oriented network scanning tool that can send custom-crafted packets for the TCP/IP protocols. It creates the custom packets for the TCP/IP protocol that sends ICMP echo request and support TCP, UDP, ICMP, and raw IP protocol.
This tool will be able to perform network security auditing, firewall testing, manual path MTU discovery, advanced traceroute, remote OS fingerprinting, remote uptime guessing, TCP or IP stack auditing, and other functions.
This network tool is able to send custom TCP/IP packets and display target replies like the ping program does with ICMP replies. The hping3 handles fragmentation, arbitrary packet body, and size and can be used in order to transfer files Encapsulated under supported protocols.
It can discover whether the host is active or not even when the host block ICMP packets. its firewalk uses allow the discovery of open ports behind the firewall. it has a traceroute function that can help an attacker to send files between covert channels.
With the help of hping tool, an attacker can create the behavior of an idle host and gain information about the target network, such as the service that the host offer, the port supporting the service, and the OS of the target.
the common syntax for the hping3 tool is
hping3 <options> <Target IP>Hping3 commands with different techniques
This is the list of the common hping command like ICMP ping, ACK scan, and many more.
ICMP Ping
example:- hping3 -1 10.0.2.6
Sending an ICMP request or ping to every host on the network is known as an “ICMP sweep” or “ICMP scanning,” and it is used to find out which hosts are online.
This protocol is used by the OS, routers, switches, and IP-based devices as a connectivity tester between various hosts using the ping command for echo requests and echo responses. The argument -1 on the command line causes Hping to run an ICMP ping scan.
You can enter -1 or –ICMP as the command line argument. With the previously mentioned command, hping works similarly to a ping utility by sending an ICMP echo request to 10.0.0.25 and receiving an ICMP reply.
ACK scan on port 21
Example:- hping3 –A 10.0.2.6 -p 21
This scanning method can be used to check for firewalls and their rule sets. Simple packet filtering permits connection establishment (packets with the ACK bit set), but an effective dynamic firewall prohibits connection establishment.
By including the -A argument in the command line, Hping can be set up to perform an ACK scan. Here, you perform the scan and set the ACK flag in the query packets.
When a host doesn’t answer a ping request, you run this scan. Hping uses this command to determine whether a host is active on a network. It responds with an RST response if it discovers a live host and an open port.
UDP scan on port 21
Example:- hping3 –2 10.0.2.6 -p 21
Hping’s default protocol is TCP. Hping operates in the UDP mode when the command line argument -2 is used to specify. You can specify the argument in the command line using either –udp or -2.
Hping transmits UDP packets to port 21 on the host (10.0.2.6) by executing the previously stated command. If the port is closed, it returns an ICMP port unreachable message; if the port is open, it does not return any message.
Collecting initial sequence
Example. hping3 10.0.2.6 -Q -p 139
Hping gathers all the TCP sequence numbers produced by the target host (192.168.1.103) using the -Q argument on the command line.
Firewall and timestamps
Example. hping3 -S 10.0.2.6 -p 21 --tcp-timestamp
A lot of firewalls discard TCP packets that lack the TCP Timestamp option set. You can use Hping to enable the TCP timestamp option and try to estimate the target host’s uptime and timestamp update frequency by adding the –tcp-timestamp argument to the command line (10.0.2.6).
SYN scan on ports 21-31
example. hping3 -8 21-31 –S 10.0.2.6 –V
You are running Hping in the scan mode to check a number of ports on the target host by using the command-line argument -8 or –scan. You can run a SYN scan by adding the argument -S. As a result, the aforementioned command runs an SYN scan on the target host’s ports 21-31.
FIN, PUSH, and URG scan on port 21
Ex. hping3 –F –P –U 10.0.2.6 –p 21
You can set FIN, PUSH, and URG packets in the probe packets by adding the command line options -F, -P, and -U. You are running FIN, PUSH, and URG scans on port 21 on the target host (10.0.2.6).
when you issue this command. You won’t get a response if port 80 is open. If the port is shut down, Hping will respond with an RST.
Scan the entire subnet for live host
Example: hping3 -1 10.0.2.x --rand-dest –I eth0
This command causes Hping to perform an ICMP ping scan on the entire subnet 10.0.2.x, which entails sending an ICMP echo request to every host on the eth0 interface between 10.0.2.0 and 10.0.2.255 at random.
The hosts with open ports will reply with an ICMP response. Since you did not specify a port in this instance, Hping by default sends packets to port 0 on all IP addresses.
Intercept all traffic containing HTTP signature
Example:- hping3 -9 HTTP –I eth0
The Hping will enter the listen mode when the argument -9 is used. As a result, when you type the command -9 HTTP, Hping starts listening on port 0 (of all the devices connected to interface eth0 in the network), intercepts all packets that contain the HTTP signature, and dumps the contents of those packets from the end of the signature to the end of the packet.
SYN flooding a victim
Ex. hping3 -S 10.0.2.1 -a 10.0.2.254 -p 22 --flood
The attacker employs TCP SYN flooding techniques using spoofed IP addresses to perform a DoS attack.
Metasploitable
An open-source project called Metasploit offers the resources, information, and tools needed to conduct thorough security audits and penetration tests. It offers details on security flaws and helps with IDS signature development and penetration testing.
It makes it easier for attackers, payload writers, and exploit writers to do their jobs. The modular design of the framework, which enables the combination of any exploit with any payload, is a significant benefit.
It gives you the tools you need to carry out the manual testing phase of a penetration test as well as the ability to automate the discovery and exploitation process.
Metasploit Pro can be used to find open ports and services, exploit them, move deeper into a network, assemble proof, and report test results.
NetScanTools Pro
An investigation tool called NetScanTools Pro enables you to troubleshoot, watch, find, and detect devices on your network. You can quickly gather data using this tool about the local LAN as well as Internet users, IP addresses, ports, and other things.
The target system has flaws and open ports that attackers can exploit. The ability to automatically or manually (using manual tools) list IPv4 and IPv6 addresses, hostnames, domain names, email addresses, and URLs is helpful to attackers.
Numerous network tools and utilities, such as active, passive, DNS, and local computer tools, are combined in NetScanTools Pro.
some additional scanning tools are listed below:
▪ sx (https://github.com)
▪ Unicornscan (https://sourceforge.net)
▪ SolarWinds Port Scanner (https://www.solarwinds.com)
▪ PRTG Network Monitor (https://www.paessler.com)
▪ OmniPeek Network Protocol Analyzer (https://www.savvius.com)
Network scanning tool for mobile devices
IP scanner
In order to identify all the active computers and Internet-connected devices on your local area network, IP Scanner for iOS scans the network. Along with pinging and port scanning, it enables attackers to conduct network scanning operations.
The original and best professional macOS and iOS network scanner. Easily determine the identity of all machines and internet devices on a LAN. IP Scanner is available on macOS and iOS in our updated free version and new Ultra app with loads of pro features.
Fing
An Android and iOS mobile app called Fing scans the network and provides detailed information like the IP address, MAC address, device vendor, and ISP location.
It enables attackers to identify all Wi-Fi networked devices, their IP, and MAC addresses, as well as the brand name of the vendor or device manufacturer.
Additionally, it enables hackers to use specific ports, including SSH, FTP, NetBIOS, and others, to conduct network pinging and traceroute operations.
Network Scanner
Attackers can locate active hosts in a network’s address space by using the Android mobile application Network Scanner. Additionally, it shows the IP addresses, MAC addresses, host names, and vendor information of all the connected devices.
With the aid of this tool, attackers can port scan targets using particular port numbers.
If you have any queries regarding the above content, or you want to update anything in the content, then contact us with your queries. You can directly post your question in the group.
Connect with us on these platforms