Hello there, in this article we are to discuss nmap which is generally a network mapper tool for collecting different types of information like open ports, version detail, OS details, etc.
If you are involved in cyber security then definitely know the concept of penetration testing which is typically known as ethical hacking, and it involves testing of network with its protocols and security for your organization.
This article will help you in understanding different concepts and techniques used in nmap. Like we will see what is nmap, nmap commands, nmap in Linux, nmap scans, nmap scripts, penetration testing with nmap, etc.
how nmap helps in penetration testing
So first, we need to know what is penetration testing basically here penetration testing is also known as “pen testing”. which is a practice of simulated attack on any computer network, server, or web application to test its security and identify any vulnerabilities which can be exploited by a hacker.
Nmap will help us in many ways to pen-test a network with its predefined scripts and commands. We can communicate with the server or network by using nmap and see what are the defense protocols level of that server.
Further, we will check all the ports and their information with nmap and see if any critical information is released or not which can help a hacker to exploit it. And if we found anything critical we can fix it before any hacker will exploit it.
What is nmap?
Network Mapper (NMAP) is a free and open-source tool for network scanning which is used to discover hosts and services on a computer network, and to create a map of the network.
It is widely used for security scans and to identify that what is the service, OS, and ports that were running on the host server, and it is also known as an information-gathering tool for networks. It is also used for getting information on what type of firewall is used by the host for securing the network.
Basically, it is available for all types of operating systems available like windows, Linux, and macOS. However, this article is written from a Linux user’s perspective. I am currently using this tool in Kali Linux 2022.
It can be used to scan a range of IP addresses or a specific host, and it can also be used to identify the type of operating system and the services running on a particular host. Moreover, it is also used by network administrators and security professionals to identify vulnerabilities and security weaknesses in a network.
Types of nmap scans
There are several types of scans that can be performed with nmap, each with a different purpose and level of intensity. Some common types of nmap scans include:
- Ping scan: This type of scan sends a simple ping request to each host in the specified range to determine which hosts are online.
- Port scan: This type of scan determines which ports on a host are open and listening for connections.
- Version scan: This type of scan attempts to identify the version of the software running on each open port on a host.
- OS detection scan: This type of scan uses various techniques to determine the operating system of a host.
- Stealth scan: This type of scan uses techniques to evade detection by firewalls and other security measures.
- Timing scan: This type of scan allows the user to adjust the speed and intensity of the scan, which can be useful for avoiding detection or for scanning large networks.
- Script scan: This type of scan allows the user to run custom scripts or plugins to perform specific tasks, such as checking for vulnerabilities or gathering detailed information about a host.
- TCP connect scan: This type of scan establishes a full TCP connection to each port in the specified range, which can be useful for bypassing firewalls that block other types of scans.
- TCP SYN scan: This type of scan, also known as a “half-open” scan, sends an SYN packet to each port in the specified range and waits for a response. This type of scan is less resource-intensive than a TCP connect scan and is less likely to be detected.
- UDP scan: This type of scan sends a UDP packet to each port in the specified range and waits for a response. This can be used to identify open UDP ports on a host.
- ACK scan: This type of scan is used to determine which ports on a host are filtered (i.e., blocked) by a firewall.
- Window scan: This type of scan is used to determine the size of the TCP window on each host in the specified range.
- FIN scan: This type of scan is used to determine which ports on a host are closed.
- Maimon scan: This type of scan is similar to a FIN scan, but it uses a different packet flag (the Maimon flag) to determine which ports are closed.
- Xmas scan: This type of scan is used to determine which ports on a host are open or filtered by a firewall. It is called an Xmas scan because it sets the FIN, URG, and PSH flags in the TCP header, which gives it a “decorated” appearance similar to that of a Christmas tree.
Some key points before proceeding to commands
You’ll get nmap preinstalled in Kali Linux. no need to install it and if you don’t have Kali Linux then you can get its virtual image from its official website. for downloading a virtual image of Kali Linux click here
Results you’ll get after scanning
- the status of ports: Either the port will be in an open state or closed state
- Filtered: port is protected by advanced firewall rules.
- Unfiltered: Port is accessible but unable to determine whether it is in an open state or closed.
- TCP wrapped: It means that the TCP 3-way handshake is completed, but we are not authorized to interact with the particular ports
Nmap commands
Before going further ill explain here something all the commands were tested on a private test server so don’t try these commands on any live server.
It is very harmful because the server created a log file when someone interacts with it, so if you do these on any live server it will create a log that this IP was trying to communicate with us.
You can these commands on the Metasploitable server, which is a private server for pen-testing.
So, let’s start with getting practical knowledge of each and every commands
Nmap ports scanning with syn
It comes under active information gathering where we are interacting with the live server to get information about its ports. So basically, here we will send a syn packet to the port we want and wait for the reply, in the reply port will send back an SYN-ACK packet that shows the port open.
If the port is closed, the host will send back an RST packet, indicating that the connection cannot be established.
The process of syn scanning is
- that nmap sends an SYN packet to the target host on the specified port.
- If the port is open, the target host sends back an SYN-ACK packet.
- nmap responds with an RST packet, effectively closing the connection.
- If the port is closed, the target host sends back an RST packet.
Different types of syn scanning
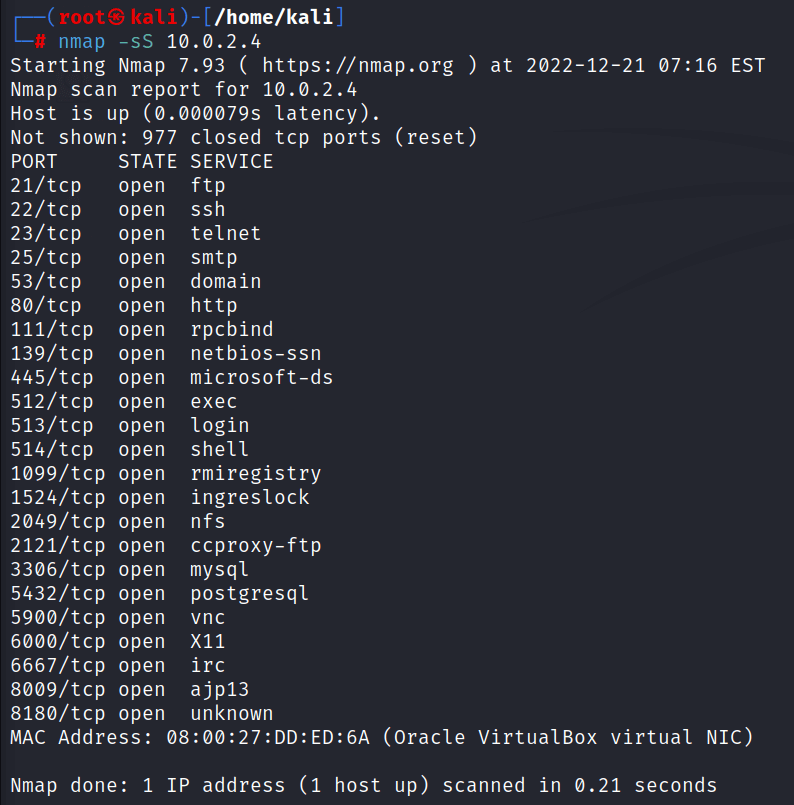
1: For scanning all ports at one time
nmap -sS [target ip address]
s = scanning
S = SYN scanning10.0.2.4 is a private server that we are targeting
2: For scanning, any fixed port we want to know is open or closed
nmap -sS -p [port number] [target ip address]
-s = scanning
-S = SYN
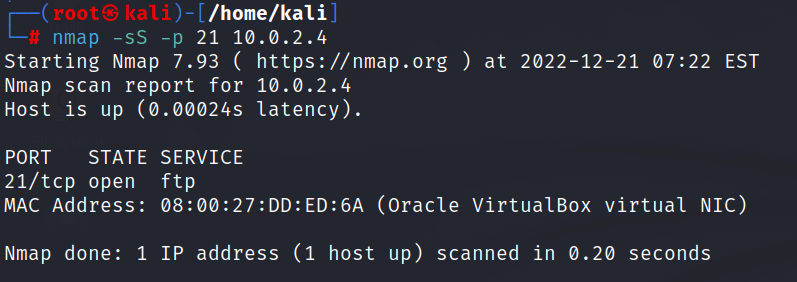
-p = Port number detailHere we are getting details of only one port which is 21, and it is in the open state. it means this port is replying to us with ACK-SYN packets.
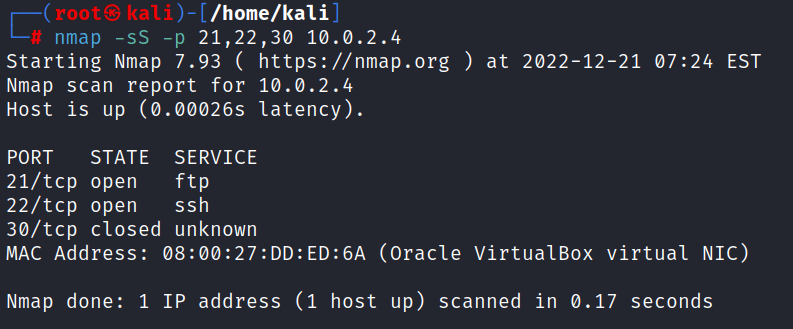
3: Scanning multiple fixed ports, forgetting their state details if it is open or closed
nmap -sS -p [port1, port2, port3, port4, etc] [Target ip address]here we’re getting the information of 3 ports which are port 21, 22, and 23.
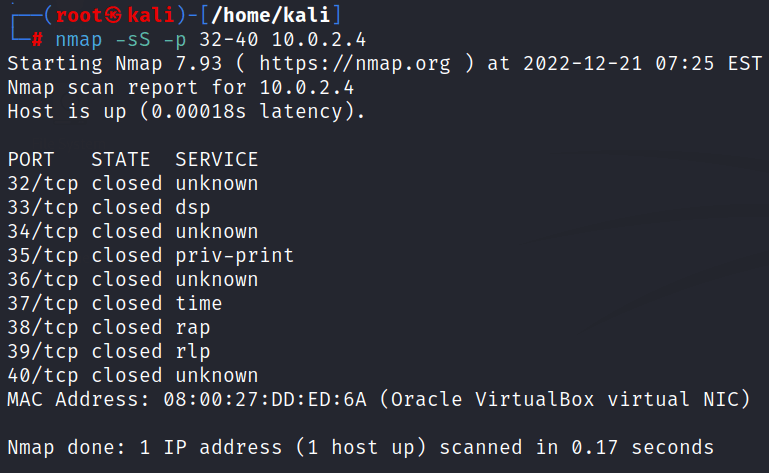
4: Scanning multiple ports in range. it is different from the last because here will give a range of ports from which nmap will scan every port that comes under that range but in the last technique we are just giving multiple port numbers.
nmap -sS -p [range for the ports] [target ip address]Here we are giving a range for scanning ports which is 32-40. and then we are getting details of every ports comes under the range of 32-40
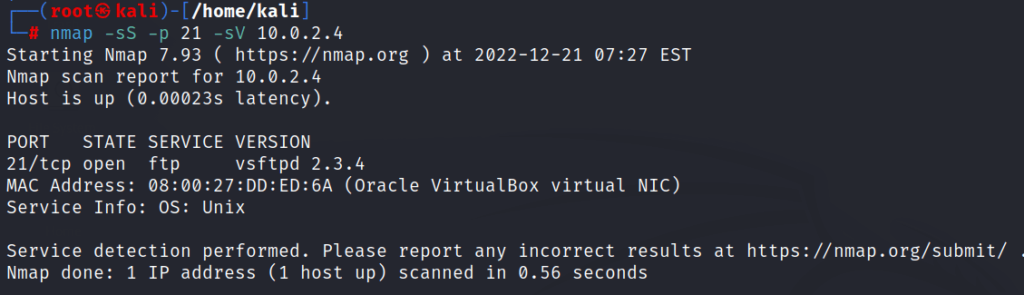
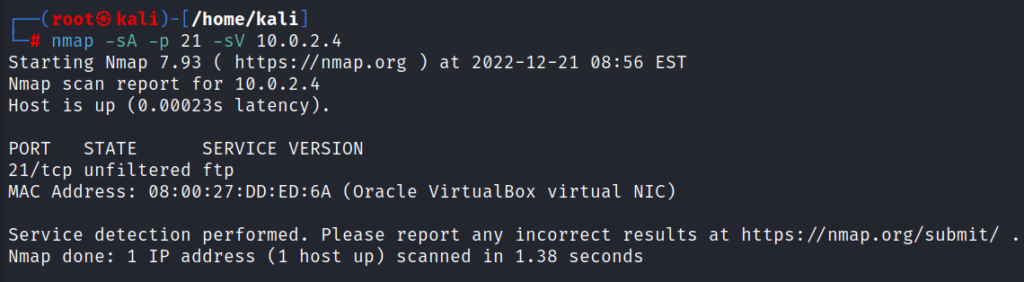
5: command for getting version details of the port or ports
nmap -sS -p [port number or range or multiple ports] -sV [target ip address]
-sV = scanning versionhere we’re getting version details of port 21 as in the figure below
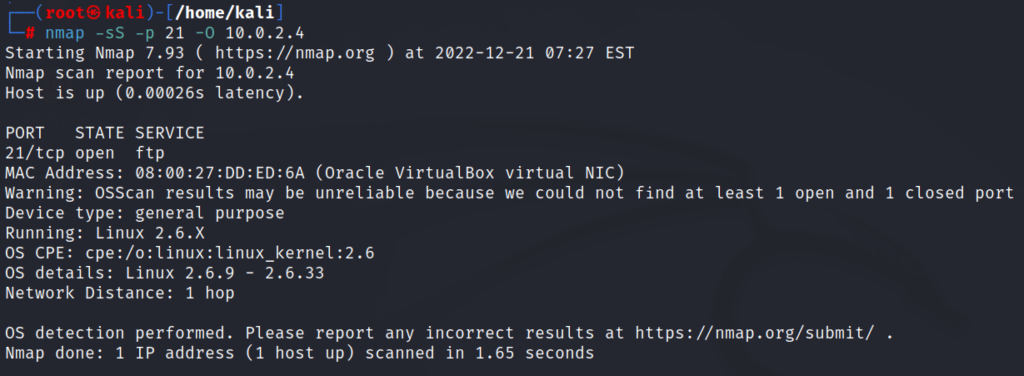
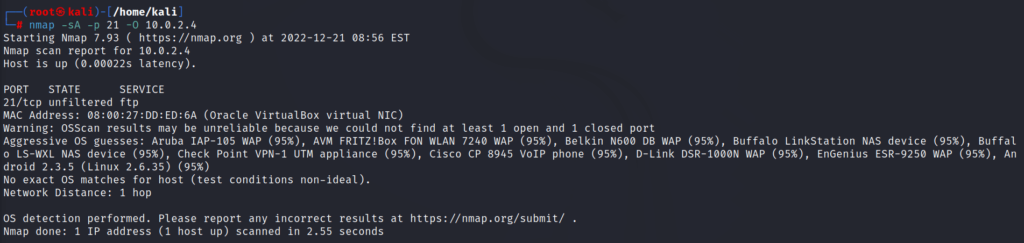
6: command for getting OS details running on the particular port
nmap -sS -p [port number or range] -O [target ip address]This script will help you in getting the OS details of any particular port you specified
Acknowledge Scanning
ACK scan is a type of scan that is used to determine which ports on a host are filtered (i.e., blocked) by a firewall. In this scan, nmap sent multiple ACK packets to the target server without getting any SYN packets from the server. This is typically misleading the server with multiple acknowledge packets request.
Here is a summary of how an ACK scan works:
- nmap sends an ACK packet to the target host on the specified port.
- If the port is open, the target host sends back an RST packet.
- If the port is filtered, the target host does not send any response.
The commands for the ACK scan are the same as the SYN commands. So I am not going to briefly describe every command just going to show all commands in one place.
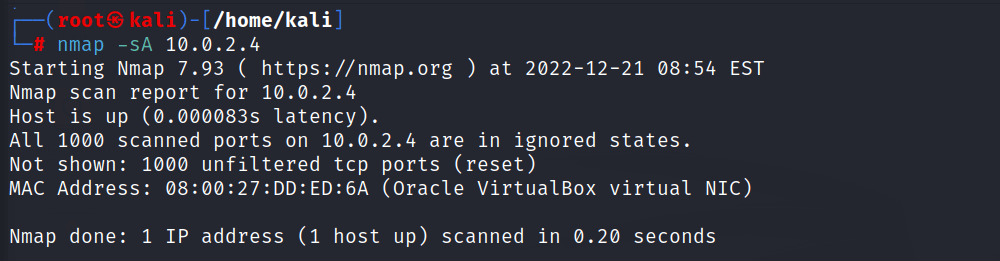
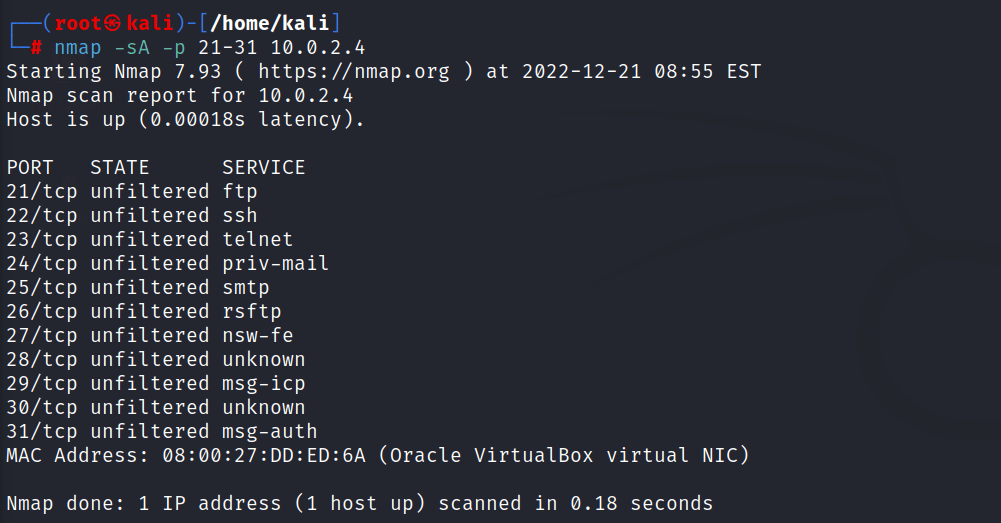
For scanning all ports in the network with ACK scan
\\
nmap -sA [target ip address]
//
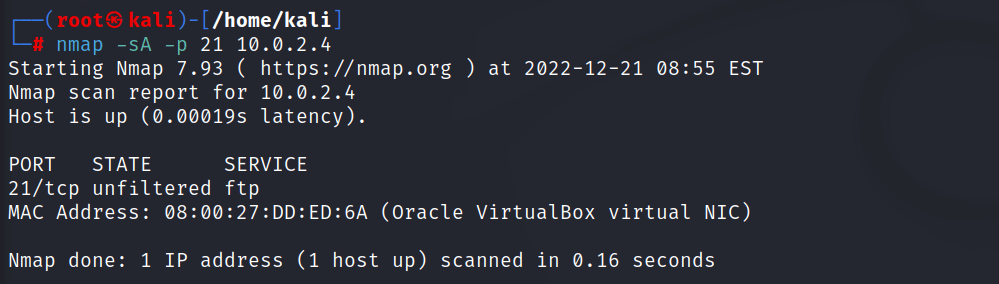
for scanning with fixed port number
\\
nmap -sA -p [port number] [target ip address]
//
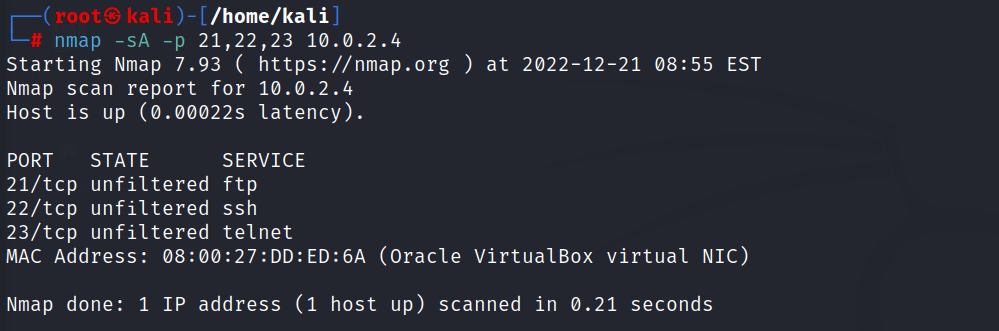
for scanning multiple ports
\\
nmap -sA -p [port1, port2, port3, port4, etc] [target ip address]
//
for scanning multiple port comes under a fixed range
\\
nmap -sA -p [range for ports ex 1-100] [target ip address]
//
for getting version detail of the port
\\
nmap -sA -p [port number] -sV [target ip address]
//
for getting OS details of any port
\\
nmap -sA -p [port number] -O [target ip address]
//output for every nmap ACK scanning command
FIN scanning
FIN scanning is like a bye message. as example when we were ending our conversation with anyone we say bye for confirming them we are leaving no more conversation will go on.
as the same fin will work nmap sends a FIN packet to each port in the specified range and waits for a response.
If the port is open, the host will send back an RST packet, indicating that the connection cannot be established. If the port is closed, the host will not send any response.
Here is a summary of how a FIN scan works:
- nmap sends a FIN packet to the target host on the specified port.
- If the port is open, the target host sends back an RST packet.
- If the port is closed, the target host does not send any response.
The commands for the FIN scan are the same as the SYN commands. So I am not going to briefly describe every command just going to show all commands in one place.
For scanning all ports in the network with FIN scan
\\
nmap -sF [target ip address]
//
for scanning with fixed port number
\\
nmap -sF -p [port number] [target ip address]
//
for scanning multiple ports
\\
nmap -sF -p [port1, port2, port3, port4, etc] [target ip address]
//
for scanning multiple port comes under a fixed range
\\
nmap -sF -p [range for ports ex 1-100] [target ip address]
//
for getting version detail of the port
\\
nmap -sF -p [port number] -sV [target ip address]
//
for getting OS details of any port
\\
nmap -sF -p [port number] -O [target ip address]
//Try the output of every command with yourself on any private server. and examine whatever result you were getting from the FIN scan. The results will not be the same as old scans may be you’ll get the answer or won’t anything.
XMAS scanning in nmap
Xmas scan is a type of scan that is used to determine which ports on a host are open or filtered by a firewall.
In this type of scan, nmap sets the FIN, URG, and PSH flags in the TCP header and sends the packet to each port in the specified range.
If the port is open, the host will send back an RST packet, indicating that the connection cannot be established. If the port is filtered, the host will not send any response.
This can be useful for identifying potential vulnerabilities in a network. The name “Xmas scan” comes from the fact that the packet appears “decorated” with flags, similar to a Christmas tree.
Here is a summary of how a Xmas scan works:
- nmap sets the FIN, URG, and PSH flags in the TCP header and sends the packet to the target host on the specified port.
- If the port is open, the target host sends back an RST packet.
- If the port is filtered, the target host does not send any response.
The commands for the XMAS scan are the same as the SYN commands. So I am not going to briefly describe every command just going to show all commands in one place.
For scanning all ports in the network with XMAS scan
\\
nmap -sX [target ip address]
//
for scanning with fixed port number
\\
nmap -sX -p [port number] [target ip address]
//
for scanning multiple ports
\\
nmap -sX -p [port1, port2, port3, port4, etc] [target ip address]
//
for scanning multiple port comes under a fixed range
\\
nmap -sX -p [range for ports ex 1-100] [target ip address]
//
for getting version detail of the port
\\
nmap -sX -p [port number] -sV [target ip address]
//
for getting OS details of any port
\\
nmap -sX -p [port number] -O [target ip address]
//Try the output of every command with yourself on any private server. and examine whatever result you were getting from the XMAS scan. The results will not be the same as old scans may be you’ll get the answer or won’t anything.
NMAP fast scan
The fast scan is a type of scan that is designed to perform a scan as quickly as possible, without performing a thorough analysis of the host or its services.
In a fast scan, nmap only sends a minimum number of packets to each host and does not attempt to gather detailed information about the host or its services.
A fast scan is much faster than a thorough scan, but it may not provide as much detail about the hosts and their services.
Here is a summary of the process of a fast scan with nmap:
- The user specifies the range of IP addresses or hosts to scan, as well as any other desired options (such as the type of scan to perform).
- nmap sends a small number of packets (such as a ping request or an SYN packet) to each host in the specified range.
- nmap analyzes the responses from the hosts and creates a list of hosts that are online and responding to the packets.
- nmap performs a basic port scan on the online hosts, identifying which ports are open and listening for connections.
- nmap produces a report indicating the status of each host and the open ports that were detected.
The commands for the FAST scan are the same as the SYN commands. So I am not going to briefly describe every command just going to show all commands in one place.
Fast scanning will scan all the ports at a time no need to specifiy ports
\\
nmap -F [target ip address]
//
for getting version and os details
\\
nmap -F -sV -O [target ip address]
//You can try these commands on a personal server to get outputs and analyze what report should it is generating.
NMAP TCP scanning
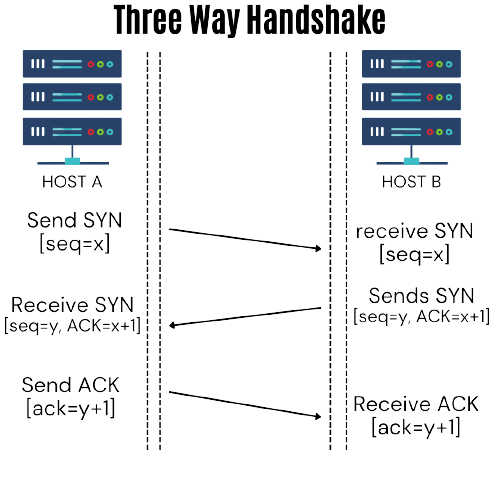
TCP scan is a type of scan that is used to determine which ports on a host are open and listening for connections. In a TCP scan, nmap establishes a full TCP connection to each port in the specified range and then closes the connection.
Here is a summary of the process of a TCP scan with nmap:
- The user specifies the range of IP addresses or hosts to scan, as well as any other desired options (such as the type of scan to perform).
- nmap sends an SYN packet to the target host on the specified port, initiating a TCP connection request.
- If the port is open, the target host responds with an SYN-ACK packet, indicating that it is ready to establish a connection.
- nmap responds with an ACK packet, completing the three-way handshake and establishing a full TCP connection.
- nmap closes the connection by sending a FIN packet to the target host.
- The target host responds with a FIN-ACK packet, acknowledging the closure of the connection.
The commands for the TCP scan are the same as the SYN commands. So I am not going to briefly describe every command just going to show all commands in one place.
nmap -sT [target ip address]
nmap -sT -sV -O [target ip address]you can try all the commands further than the same as the old ones. and try to get information from the servers by TCP scanning.
Try the output of every command with yourself on any private server. and examine whatever result you were getting from the TCP scan. The results will not be the same as old scans may be you’ll get the answer or won’t anything.
NMAP UDP scan
UDP scan is a type of scan that is used to determine which ports on a host are open and listening for connections using the User Datagram Protocol (UDP).
In a UDP scan, nmap sends a UDP packet to each port in the specified range and waits for a response. If the port is open and listening for UDP connections, the host will typically send back an ICMP “port unreachable” message. If the port is closed or filtered, the host will not send any response.
Here is a summary of the process of a UDP scan with nmap:
- The user specifies the range of IP addresses or hosts to scan, as well as any other desired options (such as the type of scan to perform).
- nmap sends a UDP packet to the target host on the specified port.
- If the port is open and listening for UDP connections, the target host sends back an ICMP “port unreachable” message.
- If the port is closed or filtered, the target host does not send any response.
The commands for the UDP scan are the same as the SYN commands. So I am not going to briefly describe every command just going to show all commands in one place.
nmap -sU [target ip address]
nmap -sU -p [port] -sV (version) -O (OS) [target ip address]you can try all the commands further than the same as the old ones. and try to get information from the servers by UDP scanning.
Try the output of every command with yourself on any private server. and examine whatever result you were getting from the UDP scan. The results will not be the same as old scans may be you’ll get the answer or won’t anything.
Thank you for reading this post, don't forget to subscribe!