Banner grabbing, or OS fingerprinting, identifies the operating system on a remote target, helping attackers exploit OS-specific vulnerabilities. There are two methods: observing banners when connecting to services (e.g., FTP) and analyzing system architecture via binary files.
More advanced techniques use stack querying, which analyzes packet responses, including TCP connection requests and initial sequence number (ISN) analysis to detect random number generation patterns.
Another approach involves sending ICMP messages and evaluating the target’s replies to further identify the OS.
Banner Grabbing Techniques
Active Banner Grabbing:
Active banner grabbing involves sending specifically designed TCP/IP packets to the target system to examine its responses. Since different operating systems have unique TCP/IP stack implementations, they respond to these packets in distinct ways. Tools like Nmap use several tests to gather OS fingerprints:
- Test 1: TCP packet with SYN and ECN-Echo flags.
- Test 2: NULL TCP packet (no flags).
- Test 3: TCP packet with URG, PSH, SYN, and FIN flags.
- Test 4: TCP packet with the ACK flag.
- Test 5: SYN packet to a closed port.
- Test 6: ACK packet to a closed port.
- Test 7: TCP packet with URG, PSH, and FIN flags to a closed port.
- Test 8: UDP packet to a closed port for ICMP “port unreachable” response.
- Test 9: TCP Sequence ability test to analyze sequence number patterns.
The purpose of these tests is to observe the sequence generation patterns from the target system, which provides clues about the OS. Different systems have different patterns:
- Older UNIX systems use the traditional 64K sequence method.
- Systems like FreeBSD and newer Solaris versions implement random increments.
- Linux 2.0 and newer AIX versions generate truly random sequences.
- Windows systems use a time-dependent sequence model, where the sequence numbers increase at a fixed interval
Passive banner grabbing:
Passive banner grabbing, similar to active banner grabbing, is a technique used to analyze the implementation of network stacks and detect operating systems based on the response of the target system.
However, while active banner grabbing involves sending requests and analyzing responses, passive banner grabbing is a stealthier approach.
It focuses on capturing packets and sniffing the network traffic to study specific tell-tale signs that may reveal the OS used by the target.
Key Techniques for Passive Banner Grabbing
- Banner Grabbing from Error Messages: Error messages, such as those providing details about the server type, OS, and SSL tools, can be insightful.
- Sniffing the Network Traffic: By analyzing network traffic, an attacker can determine the OS used by a remote system.
- Banner Grabbing from Page Extensions: Web extensions such as
.aspx(often associated with IIS servers and Windows systems) may help in identifying the server’s operating system.
Key Parameters to Determine an OS
Four key parameters often used in passive OS identification are:
- TTL (Time to Live): This parameter measures how long a packet can remain on the network before it’s discarded.
- Window Size: The size of the window set by the operating system for receiving data.
- DF (Don’t Fragment) Bit: Determines if fragmentation is allowed for the packet.
- TOS (Type of Service): Indicates the quality of service specified by the OS.
Passive fingerprinting is neither fully accurate nor limited to these four signatures. However, one can improve its accuracy by looking at several signatures and combining the information.
Example:
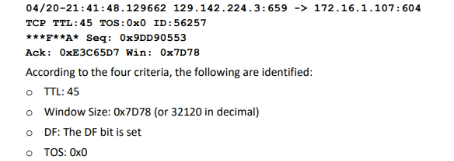
Using this information, the OS can be identified by comparing the values with a signature database. Let’s break down the key elements:
- TTL Analysis: The TTL value observed is 45. Given that the packet originally had a TTL of 64, it indicates the source was likely a Linux or FreeBSD system. To verify this, a stealthy traceroute can be conducted with a TTL set to one or two hops fewer than the default (typically 30 hops). This approach reveals the network path and upstream provider without direct contact with the remote host.
- Window Size Analysis: The window size of
0x7D78(or 32120 in decimal) is characteristic of Linux systems. FreeBSD and Solaris also maintain a consistent window size throughout a session. Conversely, Cisco routers and Microsoft Windows NT exhibit more variability in window size. Accurate measurement of window size is best after the initial TCP handshake due to TCP slow start effects. - DF Bit: The DF bit is commonly set across most systems, providing limited value for OS detection. However, it helps identify systems like SCO or OpenBSD that do not use the DF bit.
- TOS: TOS values are influenced more by the protocol rather than the OS itself. As such, TOS is less reliable for OS detection and more session-based.
By analyzing TTL and window size against a signature database, one can reasonably identify the OS—e.g., Linux kernel 2.2.x. Despite its effectiveness, passive fingerprinting has limitations similar to active fingerprinting. Notably, applications generating their own packets (e.g., Nmap) might not align with OS signatures, and hosts can adjust packet attributes (TTL, window size, DF, TOS) to evade detection.
Why Banner Grabbing?
Banner grabbing is a technique used by attackers to identify the operating system (OS) running on a target host. Understanding the OS helps attackers determine system vulnerabilities and potential exploits that could be used in subsequent attacks. This information is crucial for formulating effective attack strategies.
How to Identify Target System OS
Identifying the OS of a target system is essential for attackers to compromise a network or machine. Different OSs implement various standards to enable communication across networks, involving protocols like IP, TCP, and UDP. By analyzing specific parameters in these protocols, attackers can reveal details about the OS. Key parameters include:
- Time to Live (TTL):
The TTL field in the IP header indicates how long a packet can stay in the network before being discarded. Different OSs set different TTL values, which can help in identifying the OS. - TCP Window Size:
The TCP window size field determines the amount of data that can be sent before receiving an acknowledgment. This size varies among OSs and can be used to infer the OS in use.
| Operating System | TTL | TCP Header Size |
|---|---|---|
| Linux | 64 | 5840 |
| FreeBSD | 64 | 65535 |
| OpenBSD | 255 | 16384 |
| Windows | 128 | 65535 bytes to 1 Gigabyte |
| Cisco Routers | 255 | 4125 |
| Solaris | 255 | 8760 |
| AIX | 255 | 16384 |
Attackers can utilize Wireshark, Nmap, Unicorn Scan, and Nmap Script Engine, among other tools, to do OS discovery on the target machine. Attackers can also obtain the target OS specifics by using the IPv6 fingerprinting technique.
OS Discovery using NMAP and Unicorn scan
Using Nmap
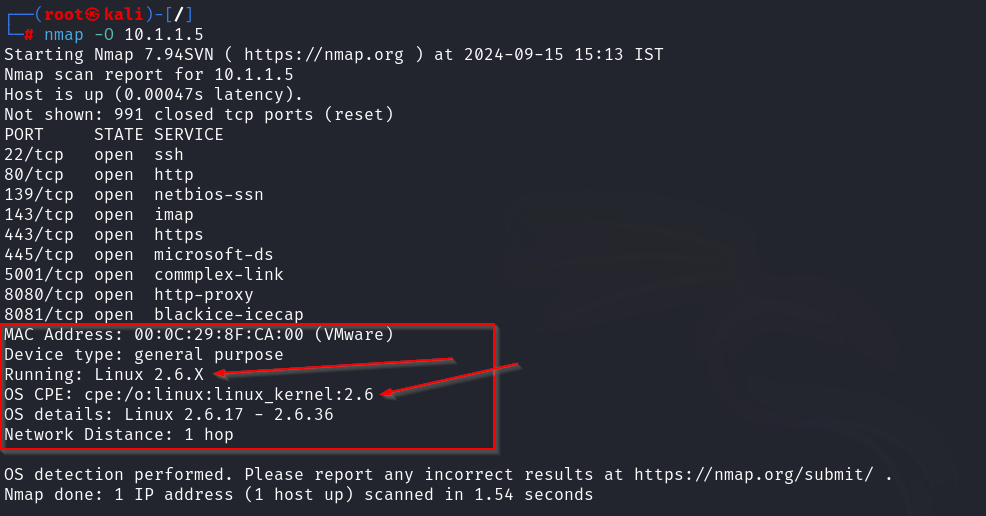
It is crucial to determine the operating system that is installed on the target computer in order to exploit it. Attackers can use a variety of techniques to obtain the target’s operating system data.
One of the best tools for carrying out OS discovery tasks is Nmap. The OS information of the target machine is displayed by OS discovery, which can be done with Nmap’s -O option.
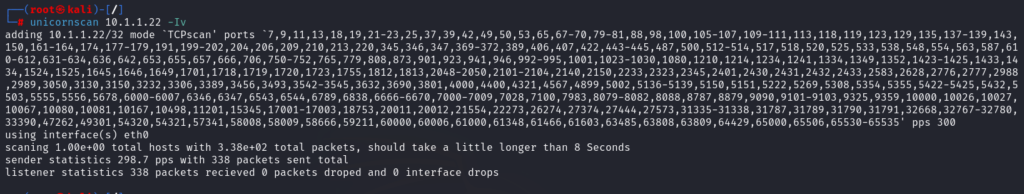
OS Discovery using Unicorn scan
The OS of the target machine in Unicornscan can be determined by looking at the TTL values in the obtained scan result. The syntax #unicornscan is used to run Unicornscan. Given that the snapshot displays a ttl value of 128 following the scan, the operating system may be Microsoft Windows.
OS Discovery using Nmap Script Engine
The Nmap Scripting Engine (NSE) facilitates the writing and sharing of scripts, which can be used to automate a multitude of networking operations. These scripts can run in parallel just as quickly and efficiently as Nmap.
Attackers can also perform OS discovery on the target system by utilizing different scripts in the Nmap Script Engine. For instance, the built-in Nmap script smb-os-discovery is used to gather OS data from the target system using the SMB protocol.
NSE may typically be enabled in Nmap by using the -sC option. Attackers can use the –script option if they want to specify the custom scripts. The Nmap normal and XML outputs together with the NSE findings will be shown.
OS Discovery using IPv6 Fingerprinting
Another method for determining the OS on the target computer is IPv6 Fingerprinting. Similar to IPv4, it is capable of sending probes, waiting for and gathering replies, and comparing those responses to a fingerprint database.
IPv6 fingerprinting differs from IPv4 fingerprinting in that it makes use of an additional set of sophisticated IPv6-specific probes in addition to a different IPv6-specific OS detection engine.
Nmap uses the IPv6 fingerprinting technique to determine the target OS by sending around 18 probes in the following sequence.
- Sequence generation (S1–S6)
- Neighbor Solicitation (NS)
- Node Information Query (NI)
- ICMPv6 echo (IE1)
- ICMPv6 echo (IE2)
- UDP (U1)
- TCP explicit congestion notification (TECN)
- TCP (T2–T7)
In nmap, the -6 option along with the -O option is used to perform OS discovery using the IPv6 fingerprinting method. Syntax: # nmap -6 -O
Thank you for reading this post, don't forget to subscribe!