Whaling is a term that refers to A targeted Phishing Attack You Can’t Afford to Ignore.
A particularly targeted phishing attempt called “whaling” poses as a genuine email and targets senior executives. Whaling is a type of social engineering-based digital fraud where the goal is to persuade victims to do a secondary action, like starting a wire transfer of money.
Although it doesn’t take a lot of technological expertise, whaling can yield significant profits. It is therefore among the greatest hazards that companies face.
Although cloud storage and file hosting sites, online services, and e-commerce sites are getting a higher percentage of attacks, financial institutions, and payment services are the organizations that are attacked the most.
Compared to standard phishing emails, whaling emails are more sophisticated because they typically target chief (or “c-level”) executives and typically
include customized information about the intended company or person; communicate a feeling of urgency; and are written with a strong grasp of business terminology and tone.
What are the risks of whaling
A type of social engineering known as “whaling emails” aims to convince its target to perform a secondary action, like:
- clicking on a link to a site that delivers malware
- requesting a transfer of funds to the attacker’s bank account
- requests for additional details about the business or individual to conduct further attacks
Reputational Wreckage
Loss of Trust: Information about a whaling attack has the potential to damage public confidence in a company, harming its reputation and making it more difficult to draw in clients and investors.
Investor Confidence: A decline in an organization’s stock price and fewer investment prospects could result from investors losing faith in its governance and security protocols.
Media Scrutiny: Whaling attack victims frequently experience unfavourable press coverage, which exacerbates the harm to their reputation.
Financial Fallout
Data breaches and fraud: Whaling operations that are successful frequently result in the exposure of private data, including bank records, corporate secrets, and consumer information. Serious penalties, legal action, and harm to one’s reputation may arise from this.
Business Disruption: Whaling malware can seriously impair operations by freezing computers, stopping production, and interfering with vital procedures. Revenue, productivity, and consumer trust may all suffer as a result.
Extortion: Cybercriminals may use hacked systems or stolen data to blackmail businesses, demanding large ransoms in order to return things to normal.
Mitigating the Risks
Security Awareness Training: By teaching staff members how to spot and report questionable emails as well as whaling methods, you may dramatically lower the likelihood that an attack will be successful.
Sturdy Security Measures: Whaling attempts can be greatly discouraged and their effects lessened by putting in place layered security solutions such as email filtering, multifactor authentication, and endpoint protection.
Incident reaction Plan: Minimizing damage and guaranteeing a prompt and efficient reaction can be achieved by having a clearly defined plan for reacting to and recovering from whaling assaults.
Evolving whaling techniques
Whaling emails were initially not all that difficult to distinguish from their less focused phishing equivalents. But even a watchful eye finds it challenging to recognize effective whaling emails because of the widespread use of fluid professional language, industry expertise, personal references, and spoof email addresses.
Executives should be aware of the combination of highly targeted content and various other strategies that can lower their risk of becoming a victim of a whaling attack.
Most importantly, each of these innovations either takes advantage of pre-existing trustworthy connections or combines a cyberattack with non-cyberfraud strategies.
Whaling email with a phone call
The NCSC is aware of multiple instances in which an email request for whaling was received and then confirmed by phone.
This is an example of social engineering, often known as cyber-enabled fraud. The phone conversation accomplishes two goals: it verifies the email request and reassures the victim that they have had a “real world” connection, which allays fears of a cyberattack.
It is commonly known that supply chain assaults are on the rise, wherein the network of a partner or supplier organization is breached to obtain access to the target organization.
On the other hand, new whaling attacks have created believable-looking whaling emails by utilizing readily available information about partners or suppliers.
An organization should be aware that if it promotes its partners—charities, legal firms, think tanks, or academic institutions—it could get emails from dishonest people posing as these reliable sources.
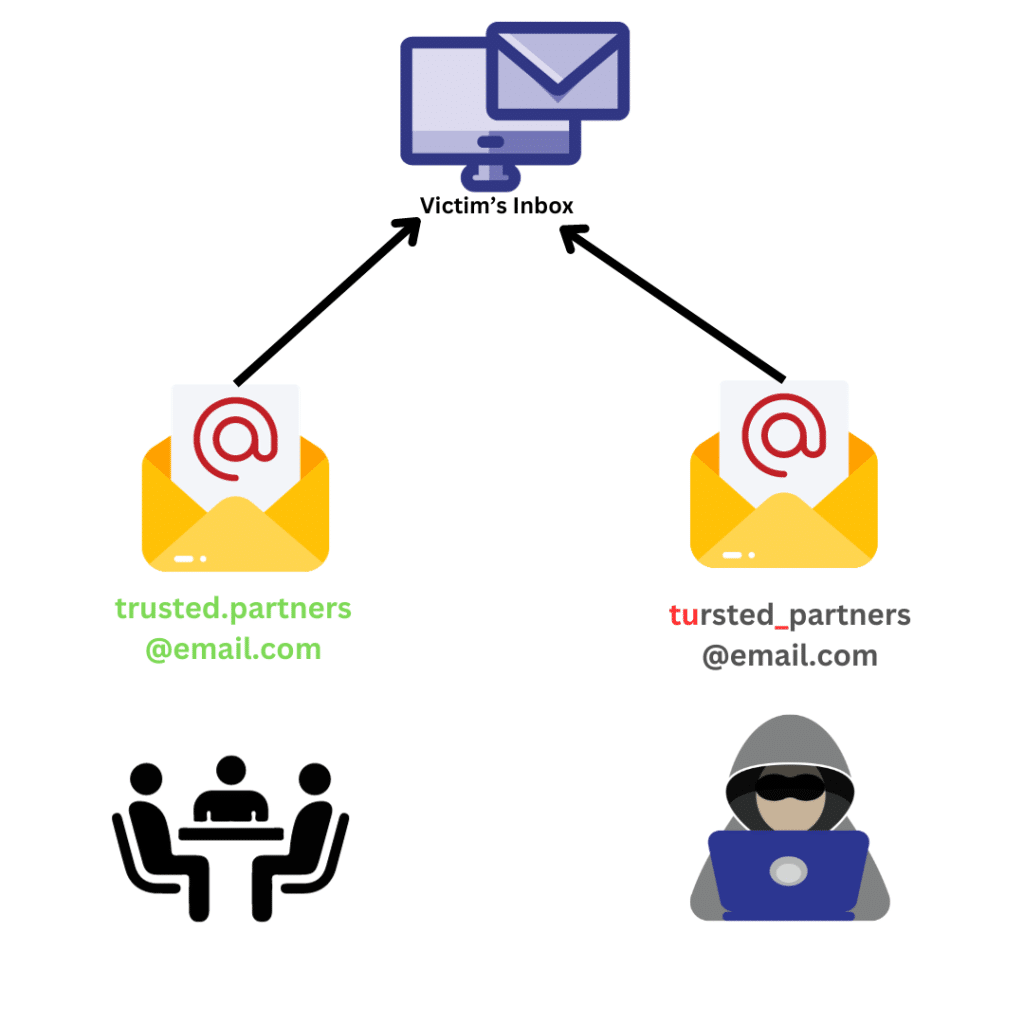
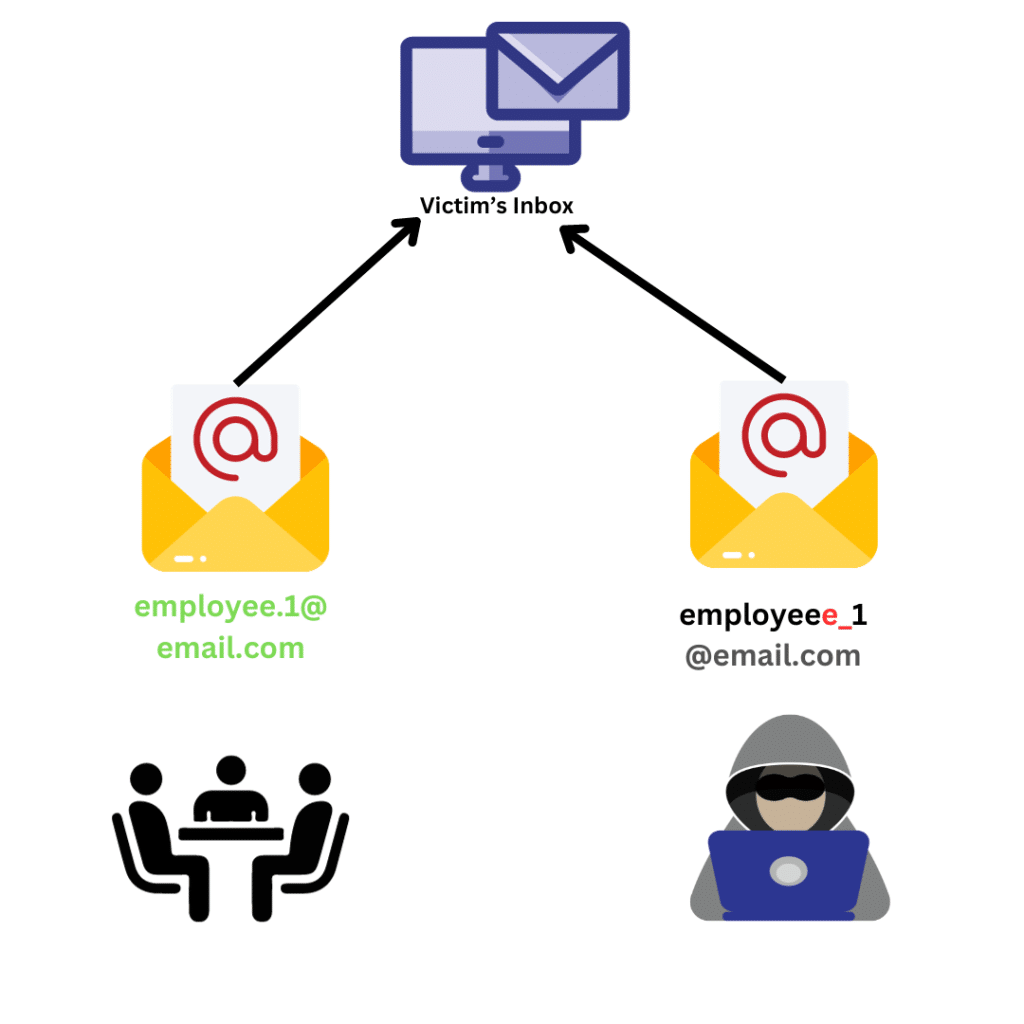
This occurs when an employee’s email account is either hacked or spoof to make other staff members believe they are getting a genuine request from a coworker.
This works particularly well when a highly senior executive’s email address is spoof to ask a junior employee of, say, the finance department for an urgent payment.
Online social networking is becoming a more and more popular means of conducting debates, hiring staff, and establishing business ties.
Malicious actors can, however, use social media accounts—both personal and professional—to find and get in touch with senior leaders.
In a more social setting, they offer a wealth of information for social engineering, and victims are frequently less alert to attacks. 2015 saw a 150% rise in social media phishing assaults, according to Proof Point.
Catching your white whale
It is important to keep in mind that whaling is a form of social engineering, and that in order to reassure the victim, hostile actors will employ techniques that take advantage of well-established trust systems that exist outside of the cyber world.
Even with user awareness and training, some attacks are too skilfully designed to be detected, thus simply alerting your staff about social engineering dangers won’t make them immune.
Recognizing the limitations of such measures, employee and executive training on social engineering techniques should be viewed as one of several user-based and technical defences against attacks.
Similarly, whilst organizations should ensure training is supported by hardened technical defences, malicious actors are increasingly employing techniques to evade automated detection and prevent analysis of attack methodology.
As such, organizations should accept that a successful whaling attack is a possibility, and put in place checks and processes to mitigate the damage.
Thank you for reading this post, don't forget to subscribe!