Cybersecurity is big business in the modern-day world. The hacks that we hear about in newspapers are from exploiting vulnerabilities. In this room, we’re going to explain exactly what a vulnerability is, the types of vulnerabilities and how we can exploit these for success in our penetration testing endeavours.
An enormous part of penetration testing is knowing the skills and resources for whatever situation you face. This room is going to introduce you to some resources that are essential when researching vulnerabilities, specifically, you are going to be introduced to:
- What vulnerabilities are
- Why they’re worthy of learning about
- How are vulnerabilities rated
- Databases for vulnerability research
- A showcase of how vulnerability research is used on ACKme’s engagement
Room Link Vulnerabilities 101
Task 2 Introduction to Vulnerabilities
Question: An attacker has been able to upgrade the permissions of their system account from “user” to “administrator”. What type of vulnerability is this?
Answer: operating system
Question: You manage to bypass a login panel using cookies to authenticate. What type of vulnerability is this?
Answer: application logic
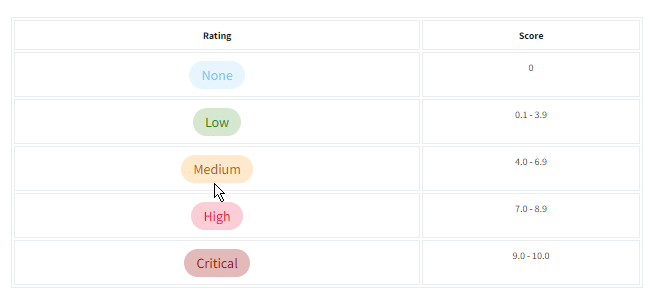
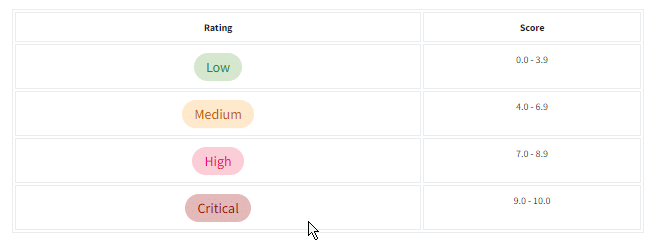
Task 3 Scoring Vulnerabilities (CVSS & VPR)
Question: What year was the first iteration of CVSS published?
Answer: 2005
Question: If you wanted to assess vulnerability based on the risk it poses to an organization, what framework would you use?
Note: We are looking for the acronym here.
Answer: VPR
Question: If you wanted to use a framework that was free and open-source, what framework would that be?
Note: We are looking for the acronym here.
Answer: CVSS
Task 4 Vulnerability Databases
Question: Using NVD, how many CVEs were published in July 2021?
Answer: 1554
Question: Who is the author of Exploit-DB?
Answer:OFFSEC
Task 5 An Example of Finding a Vulnerability
Question: What type of vulnerability did we use to find the name and version of the application in this example?
Answer: version disclosure
Task 6 Showcase: Exploiting Ackme’s Application
Question: Follow along with the showcase of exploiting ACKme’s application to the end to retrieve a flag. What is this flag?
Answer: THM{ACKME_ENGAGEMENT}