Network devices are the building blocks and backbone of today’s contemporary and large-scale networks and systems. The role of network devices is to ensure reliable and efficient transfer, filtering, and management of data across or within networks.
Room Link Network Device Hardening
Many network devices range from basic layer one hubs or repeaters to layer two switches, layer three routers, load balancers, virtual private networks, and intrusion prevention systems.
Learning Objectives
The room aims to teach techniques for identifying and mitigating security vulnerabilities, hardening network device configurations, and implementing security best practices.
By the end of this room, you should be able to assess and strengthen network device security, enhance network resilience, and effectively defend against common cyber threats. Learning Pre-requisites
An understanding of the following topics is recommended before starting the room:
Let’s begin!
Task 2 Common Threat and Attack Vectors Network Device
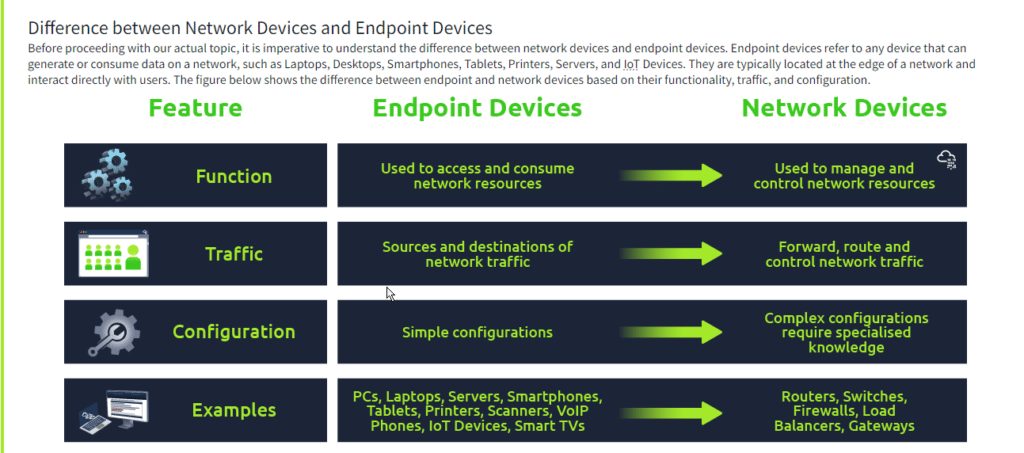
Question: The device that is used to control and manage network resource is called?
Answer: network device
Question: A threat vector that includes disruption of critical devices and services to make them unavailable to genuine users is called?
Answer: denial of service
Task 3 Common Hardening Techniques
Question:
Suppose you are configuring a router; which of the following could be considered an insecure protocol:
A: HTTPS
B: FTP
C: SSH
D: IPsec
Answer: B
Question: The protocol for sending log messages to a centralised server for storage and analysis is called?
Answer: Syslog
Task 4 Hardening Virtual Private Networks
Question: Update the config file to use cipher AES-128-CBC. What is the flag value linked with the cipher directive?
for updating the conf file navigate and open server.conf file with nano in terminal. file can be located at /etc/openvpn/server/server.conf
you’ll find the flag for all question 1, 2 and 3. update the configuration and save it
Answer: Standard Hardening Practices
Question: Update the config file to use auth SHA512. What is the flag value linked with the auth directive?
Answer: Standard Hardening Practices
Question: As per the config file, what is the port number for the OpenVPN server?
Answer: 1194
Task 5 Hardening Routers, Switches & Firewalls
Question: Update the password of the router to TryHackMe123.
To update the default password navigate to System -> Administrator -> Router password Now enter the desired password.
Answer: no answer
Question:
Question: What is the default SSH port configured for OpenWrt in the attached VM?
navigate System -> Administrator -> SSH Access
Answer: 22
Question: Go through the General Settings option under the System tab in the attached VM. The administrator has left a special message in the Notes section. What is the flag value?
Answer: THM{SYSTEM101}
Question: What is the default system log buffer size value for the OpenWrt router in the attached VM?
Hint: System -> System -> Logging
Answer: 64
Question: What is the start priority for the script uhttpd?
Hint: System -> Startup -> Initscripts
Answer: 50
Task 6 Hardening Routers, Switches & Firewalls – More Techniques
Question: What is the name of the rule that accepts ICMP traffic from source zone WAN and destination zone as this device?
Hint: Navigate to Network -> Firewall -> Traffic Rules
Answer: Allow-Ping
Question: What is the name of the rule that forwards data coming from WAN port 9001 to LAN port 9002?
Hint: Naviate to Network -> Firewall -> Port Forwards
Answer: THM_PORT
Question: What is the version number for the available apk package?
Hint: Navigate to System -> Software then apply filter as apk
Answer: 2.12.2-1
Task 7 Important Tools for Network Monitoring
Question: Are network monitoring tools capable of detecting bandwidth bottlenecks? (yea/nay)
Answer: yea
If you have any queries regarding the above content, or you want to update anything in the content, then contact us with your queries. You can directly post your question in the group.
Connect with us on these platforms