Hello everyone, welcome back to our new article on the threat intelligence life cycle, this article will help you in understanding the different phases in the threat intelligence life cycle.
The threat intelligence life cycle is the continuous process of developing intelligence from raw data that support organizations to develop defensive mechanisms towards emerging risks and threats.
The higher-level executive of the company always provides continuous support to the intelligence team by evaluating and giving feedback at every stage.
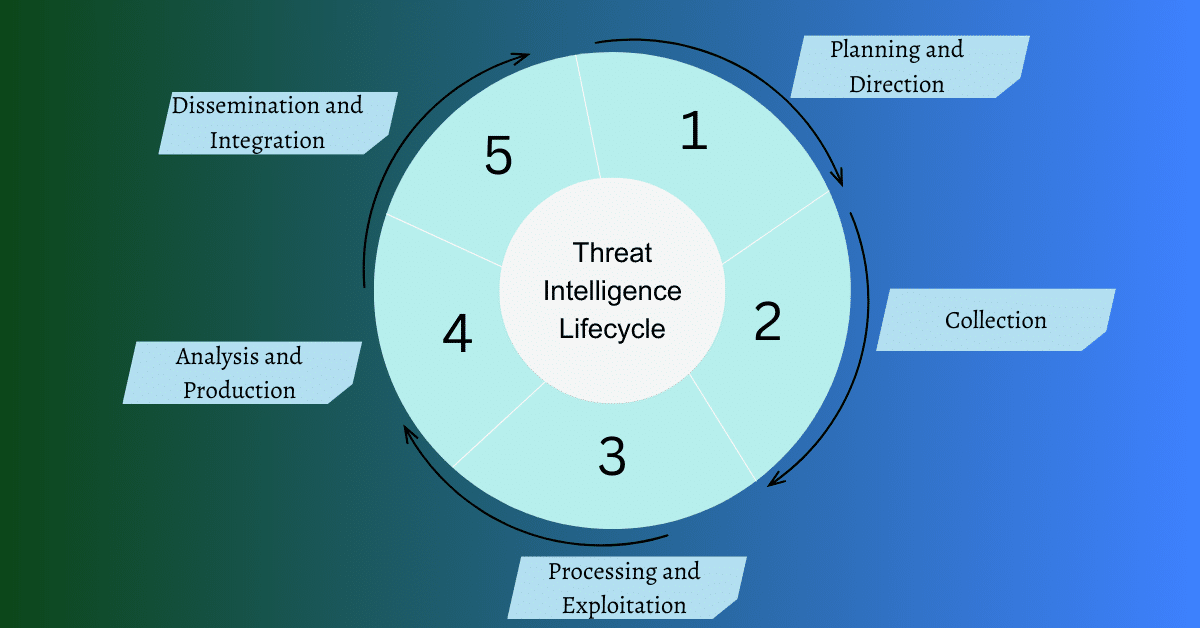
the threat intelligence life cycle consists of 5 phases:
- planning and direction
- Collection
- professing and exploitation
- analysis and production
- dissemination and integration
Planning and direction
This is the first phase in the threat intelligence life cycle which helps the security professionals for developing a proper plan based on the strategic intelligence requirement.
For example which intelligence information should be prioritized first and which will be last, what will be the basic requirements for developing a threat intelligence, etc.
This phase defines the process of the intelligence program from its data collection to the delivery of the final intelligence product and acts as a basis for the complete intelligence process.
The planning and direction phase includes some basic things like identifying the requirement of data, the method that is used to collect the data and creating a collection plan.
The requirement is set in such a way that effective and genuine intelligence data can be gathered using the constant number of resources from various open sources of intelligence (OSINT).
The data can also be collected from various internal and external sources. During planning and direction, an intelligence team is created with key roles and responsibilities that are also formulated.
Also, the planning and requirement are set for the further stages of the cycle to give proper support for its functioning.
Collection
This is the second phase in the threat intelligence life cycle which helps security professionals for collecting the desired intelligence information that is defined in phase one.
The information or the data collected in the second phase can be obtained from many ways like technical or human means.
The collection of the data can be operated directly or secretly based on the confidentiality of the information that we are going to collect.
The intelligence information that is collected over here, can be obtained from the sources like human intelligence (HUMINT), imagery intelligence (IMINT), measurement and signature intelligence (MASINT), signal intelligence (SIGNT), open source intelligence (OSINT), and IoCs, and from any 3rd party vendor.
This information can include the collection of data from critical applications, network infrastructure, security infrastructure, security measures, Etc.
The collection of the data process is completed then the collected data is transferred for processing in the next stage.
Processing and Exploitation

The data collected before this stage is not available in the proper format because it is in the form of raw data.
The data collected from the previous stages are processed for exploitation and transformed into useful information that could be understood by the consumers.
In this stage, the raw data is converted into meaningful information by highly trained professionals using sophisticated technology and tools.
This interpreted data is converted into a usual format that can be directly used in the data analysis phase.
The processing of data should effectively require a proper understanding of the data collection plan, the requirement of the consumer, the analytical strategy, and the types of data being processed.
Many automated tools are used to apply data processing functions such as structuring, decryption, language translation, parsing, data reduction, filtering, data correlation, and data aggregation.
Analysis and Production
In the last stage the data is processed into the proper format, for further intelligence now in this phase we will analyze the intelligence for getting we find information formed this phase.
The analysis in this phase includes facts, finding, and forecasts, which will enable the estimation and anticipation of the attack and result. The analysis should be actionable, timely, accurate, and objective.
To extract timely and accurate information a security professional needs to implement different types of reasoning techniques that include deduction, induction, abduction, and scientific methods based on confidence.
As we know the information is generated from many different sources, so the security professional need to combine these various sources into a single entity in this phase.
The raw data we collected is need to be converted into information by applying various data analysis technique that includes qualitative and quantitative analysis, machine-based techniques, and statistical methods.
After the analyzed information, provides sufficient data for identifying a threat, then it is evaluated for intelligence.
The analysis and production phase is responsible for identifying potential threats to the organization and further helping in developing an appropriate countermeasure to respond to the identified threats.
Dissemination and Integration
The analyzed information from the last stage is now ready for integration and distribution to the intended users and consumers, this can be done either by automated means or by manual methods.
Most of the threat information types used for dissemination includes threat Intelligence Report, security alerts, attacker TTPs, threat indicators, and tool configuration information for using tools to automate all the phases of threat intelligence.
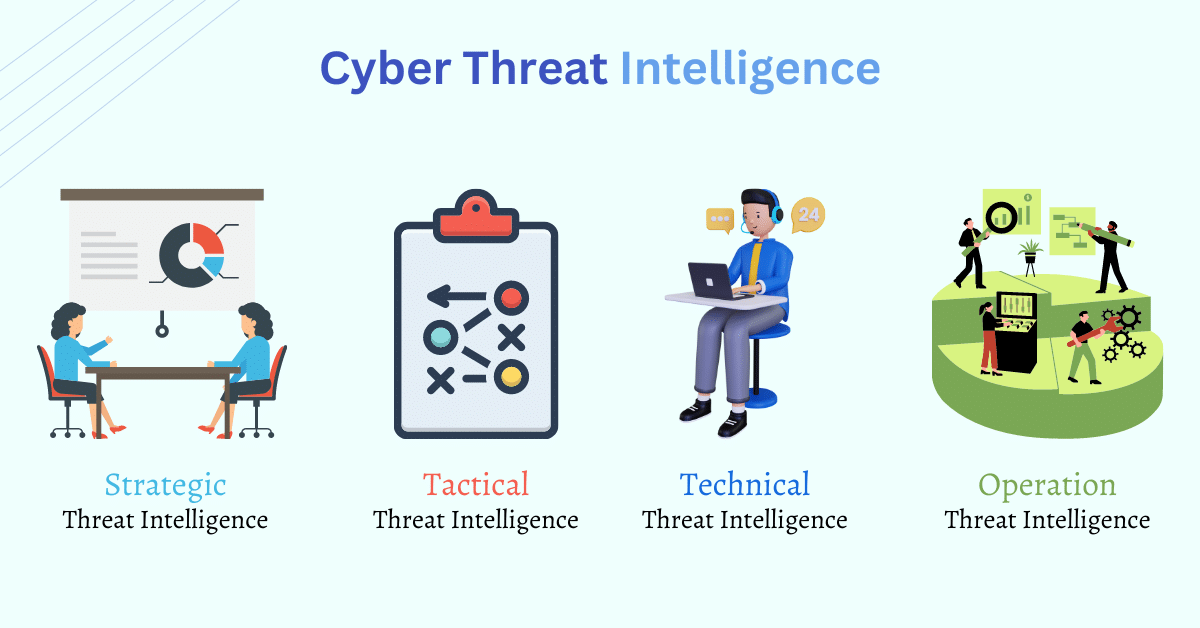
There are many Intelligence reports generated to meet the requirement of the management team and higher-level executives at different phases of strategic, operational, tactical, and technical levels.
Strategic threat intelligence is consumed by high-level executives and management teams to focus on high-level business strategies.
Operational threat intelligence is consumed by cyber security professionals such as security managers and network defenders that mainly focus on specific threats to the organization.
Tactical threat intelligence is consumed by cyber security professionals such as administrators, IT service and SOC managers, and architects that mainly focuses on hacker tactics, techniques, and procedures for performing the attack.
The technical threat intelligence is consumed by the incident response team and SoC staff which includes information related to the identified IoCs.
The disseminated intelligence helps the organization in building strong defensive and mitigation strategies for known threats.
Sharing threat intelligence information internally or externally helps an organization to be aware and also to enhance the current security posture and risk management processes.
This phase also provides feedback giving more input to the information required thereby repeating the threat intelligence life cycle.
feedback is an assessment that describes whether the extracted intelligence meets the requirement of the intelligence consumer. this feedback helps in producing more accurate intelligence through relevant and timely assessment.
Thank you for reading this post, don't forget to subscribe!