Checking the open ports and services in active systems is the next phase in the network scanning procedure. Numerous port scanning techniques can be used to find open ports and services.
While attackers use port scanning techniques to find open ports and services that are operating on a host to compromise the network, administrators frequently use them to confirm the security policies of their networks.
Additionally, users occasionally leave needless open ports on their devices without realizing it. Such open ports are exploited by an attacker to initiate attacks.
TCP Connect/Full-Open Scan
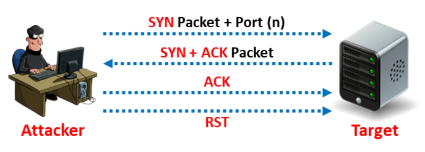
Among the TCP scanning methods that are most dependable is TCP Connect/Full Open Scan. The OS’s TCP connect() system call attempts to establish a connection to each port of interest on the target machine during TCP Connect scanning.
The connect() function will successfully establish a connection with the host on that specific port if it is listening; if not, it will produce an error message indicating that the port is not reachable. The target machine and TCP Connect scan conclude their three-way handshake.
The client transmits a SYN packet during the TCP three-way handshake, and the recipient responds with a SYN+ACK packet. The connection is then completed when the client sends an ACK packet in response to the SYN+ACK packet. Once the handshake is completed, the scanner sends an RST packet to end the connection.
Over a slow connection, it would take a long time to make a separate connect() call for each targeted port in a linear fashion. Using multiple sockets simultaneously, the attacker can speed up the scan. I/O, which employs non-blocking, enables the attacker to establish a brief time-out window and observe every socket at once.
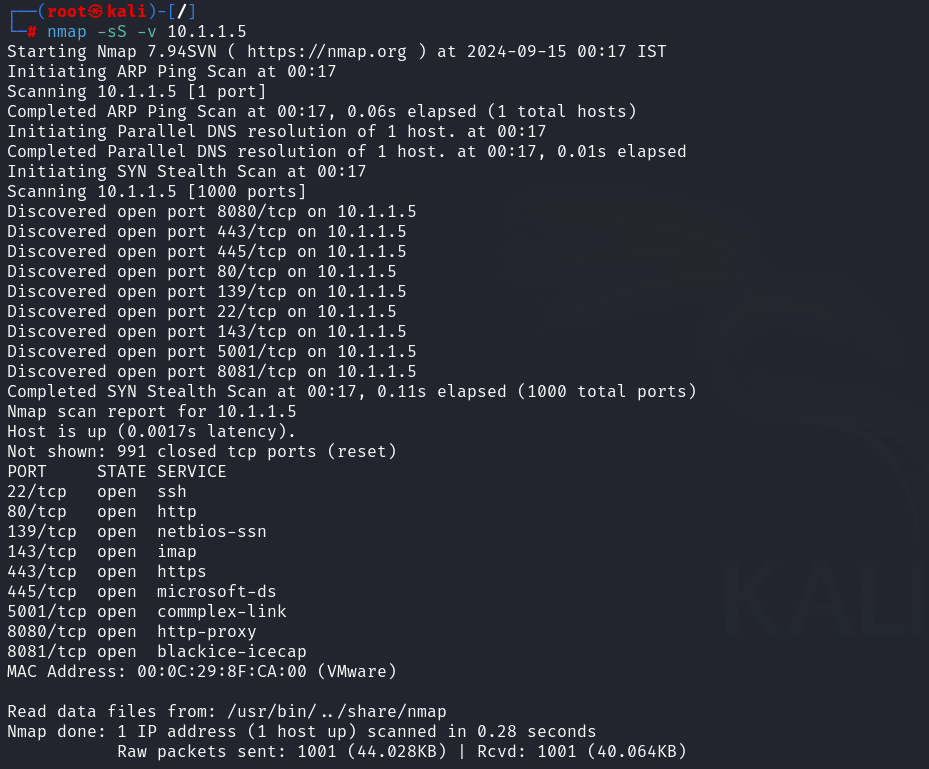
The -sT option in Nmap is used to execute a TCP connect/full open scan.
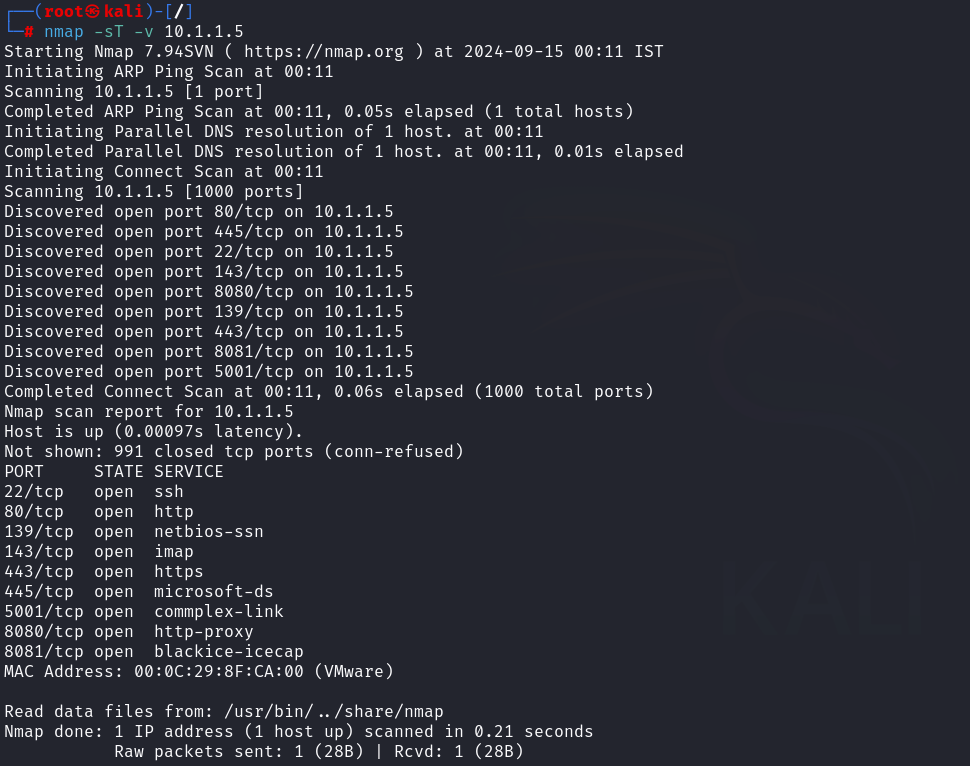
This kind of scan has the disadvantage of being simple to identify and filter. The link will be visible in the target system’s logs. Superuser rights are not necessary for this kind of scanning.
Stealth Scan (Half-Open Scan)
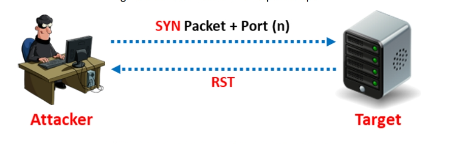
In order to do a stealth scan, the client and server’s TCP connection is abruptly terminated prior to the three-way handshake signals being completed, leaving the connection partially open. Without requiring any further packet exchanges or TCP handshaking, a stealth scan delivers a single frame to a TCP port.
With this kind of scan, one frame is sent and one response is anticipated. The link is only partially established by the half-open scan, which ends midway. Because the stealth scan just transmits the SYN packet, it is also referred to as a “SYN scan.” By doing this, the service is unable to alert the incoming connection. One covert way to scan ports is with TCP SYN, often known as half-open scanning.
The three-way handshake technique is also used in the stealth scan. The final step involves inspecting the packets coming into the interface, cutting the connection, and then starting over to find the distant ports.
The following describes the stealth scan procedure.
- If the port is open, the server replies with a SYN/ACK packet after receiving a single SYN message from the client on the designated port.
- The remote port is in the “closed” state if the server replies with a RST packet.
- An establishment of a connection is contingent upon the client sending the RST packet to close the initiation.
Hackers conceal themselves as normal behind network traffic and employ stealth scanning techniques to get around firewall rules and logging systems. The -sS option in Zenmap is used to run a TCP half-open/stealth scan.
Inverse TCP Flag Scan
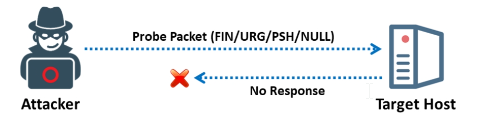
Attackers transmit TCP probing packets with or without a TCP flag (FIN, URG, or PSH) set. When the port is closed, the target host sends the attacker a RST; when the port is open, the attacker receives no response from the host.
Sending SYN packets to the targeted hosts’ sensitive ports is detected by security mechanisms like firewalls and intrusion detection systems (IDS). SYN flag scan attempts with the half-open state can be recorded using programs like Syslog.
Depending on the security measures in place, probing packets that have been enabled with TCP flags may occasionally slip past filters without being noticed. In an inverted approach, the closed ports can only send the response back, therefore a half-open SYN flag is used to probe the target.
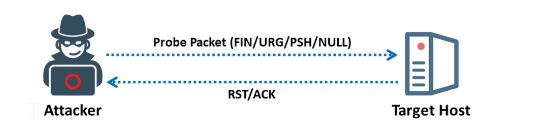
When a host closes a port, RFC 793 states that a RST/ACK packet is sent to reset the connection. Attackers use this capability to their advantage by sending TCP probe packets with different TCP flags set to each port of the target host.
Security devices such as firewalls and intrusion detection systems (IDS) detect the sending of SYN packets to the sensitive ports of the targeted hosts. Syslog and other programs can record SYN flag scan attempts in the half-open condition.
Probing packets that have been enabled with TCP flags may sometimes pass through filters undetected, depending on the security mechanisms in place. Since the closed ports in an inverted technique can only send the response back, the target is probed using a half-open SYN flag.
RFC 793 specifies that a RST/ACK packet be transmitted to reset the connection when a host closes a port. Attackers take use of this feature by sending TCP probe packets to each port of the target that have distinct TCP flags configured.
Xmas Scan
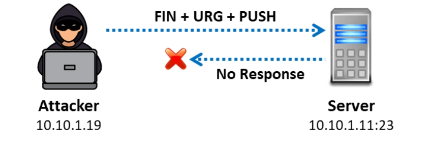
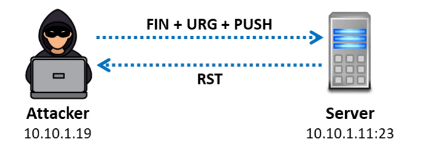
The FIN, URG, and PUSH flags are set to deliver a TCP frame to a remote device during an Xmas scan, a sort of inverted TCP scanning technique. You won’t hear back from the remote system if the target has opened the port. You will receive a remote system respond with a RST if the target has closed the port. This port scanning method can be used to search through big networks to determine which hosts are online and what services they provide.
Every TCP flag set is described by this method. Some systems hang when all flags are set, which is why the flags are frequently set in the absurd URG-PSH-FIN sequence. Attackers utilize the RST packet and the TCP Xmas scan to check if any ports on the target machine are closed. Only systems that comply with the TCP/IP implementation based on RFC 793 are able to use this scan. It is incompatible with all current Microsoft Windows versions.
TCP Maimon Scan
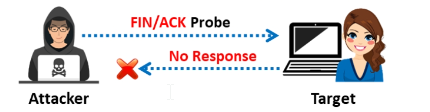
The probe utilized in this scan is FIN/ACK, however it is otherwise quite similar to the NULL, FIN, and Xmas scan techniques. The RST packet should typically be issued in response to a probe request in order to ascertain if the port is open or closed. However, if the packet is discarded in response to a probe, the port is open in many BSD systems.
When a port remains unresponsive to several retransmissions of the Maimon scan probe, Nmap considers it to be open|filtered. If the probe receives a RST packet in response, the port is closed. When the destination host returns an ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13), the port is filtered. The TCP Maimon scan in Zenmap is done with the -sM option.
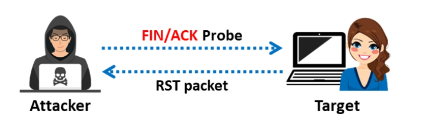
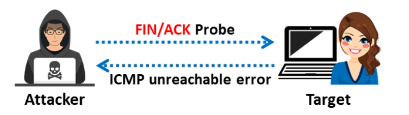
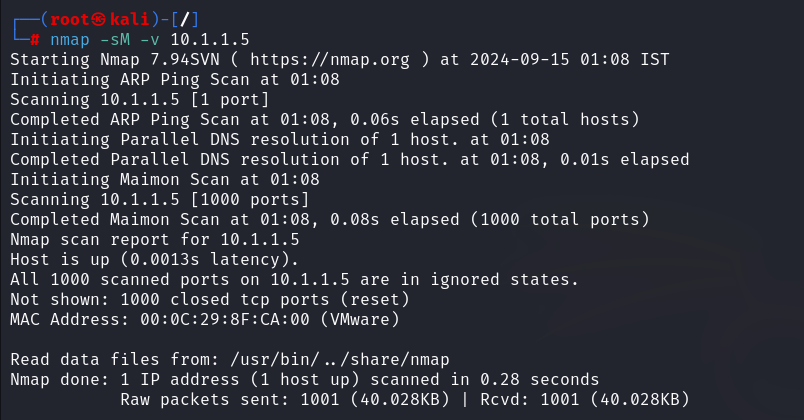
ACK Flag Probe Scan
To determine if a port is open or closed, attackers send TCP probe packets with the ACK flag set to a remote device. They then examine the header data (TTL and WINDOW field) of the received RST packets. The BSD-derived TCP/IP vulnerabilities are exploited by the ACK flag probe scan.
TTL-Based ACK Flag Probe scanning
In this scanning technique, you will first need to send ACK probe packets (several thousands) to different TCP ports and then analyze the TTL field value of the RST packets received. In Zenmap, the syntax nmap –ttl [time] [target] is used to perform TTL-based scan.
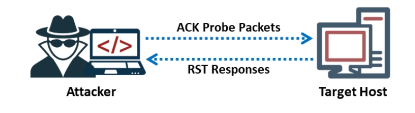
If the TTL value of the RST packet on a particular port is less than the boundary value of 64, then that port is open. An example showing a log of the first four RST packets received is presented below
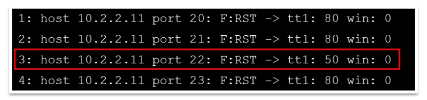
n this example, port 22 returned a TTL value of 50, which is less than 64; all other ports returned a TTL value of 80, which is greater than 64. Therefore, port 22 is open.
Window-based ACK Flag Probe scanning\
In this scanning technique, you will first need to send ACK probe packets (several thousands) to different TCP ports and then analyze the window field value of the received RST packets. The user can use this scanning technique when all the ports return the same TTL value. In Zenmap, the -sW option is used to perform a window scan.
If the window value of the RST packet on a particular port is non-zero, then that port is open. An example showing a log of the first four RST packets received is presented below:
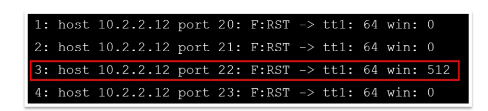
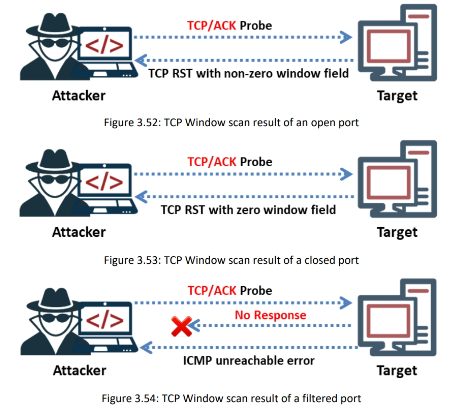
The above figure shows that the TTL value returned for each packet is the same; hence, you cannot perform TTL-based ACK flag probe scanning to find the open ports. Therefore, when you observe the window value, the third packet has a non-zero window value, which means that the port is open. When the returned RST value is zero, then the port is closed. If there is no response even after many retransmissions and an ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) is returned, then the port is inferred to be a filtered port.
Checking the Filtering Systems of Target Networks
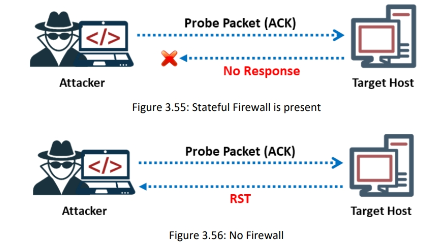
The ACK flag probe scanning technique also helps in checking the filtering systems of target networks. The attacker sends an ACK probe packet to check the filtering mechanism (firewalls) of packets employed by the target network. Sending an ACK probe packet with a random sequence number and getting no response from the target means that the port is filtered (stateful firewall is present); an RST response from the target means that the port is not filtered (no firewall is present).
Third-Party and Spoofed TCP Scanning Methods
IDLE/IP ID Header Scan
Background Process: IDLE scans are highly stealthy because they use a third-party system (called a “zombie”) to conduct the scan indirectly. The attack works by exploiting predictable IP ID sequencing in the zombie host. The process works as follows:
- The attacker sends a spoofed SYN packet to the target with the zombie’s IP address as the source.
- The target responds to the zombie, not the attacker.
- By monitoring the zombie’s IP ID changes, the attacker can infer whether the target port is open or closed. An increase in the IP ID value suggests the target responded to the SYN packet, meaning the port is open.
Since the target only sees traffic coming from the zombie and not the attacker, this method hides the attacker’s IP address.
UDP Scanning Techniques
UDP Scanning
Background Process: UDP scans are more challenging than TCP scans because UDP is connectionless, meaning it lacks the SYN/ACK and RST responses used in TCP scanning. In a UDP scan:
- The scanner sends a UDP packet to the target.
- If the port is open, there is usually no response unless the service is configured to reply (e.g., a DNS server might send a response to a DNS query).
- If the port is closed, the target responds with an ICMP Port Unreachable message.
Due to the lack of direct responses from open ports, this technique is slower and less reliable than TCP scanning. Additionally, many systems limit the rate at which they send ICMP responses, further slowing down the scan.
SCTP Scanning Techniques
SCTP (Stream Control Transmission Protocol) is commonly used in telecom networks and has distinct scanning techniques.
SCTP INIT Scanning
Background Process: In SCTP INIT scanning, the attacker sends an INIT chunk to the target port:
- Open ports respond with an INIT-ACK chunk.
- Closed ports respond with an ABORT chunk.
This method is similar to the TCP SYN scan but applies to SCTP-based services. It allows the scanner to determine the state of SCTP ports and whether services are running on them.
SSDP Scanning Techniques
SSDP (Simple Service Discovery Protocol) is used to discover network devices in UPnP environments.
SSDP and List Scanning
Background Process: An SSDP scan works by sending M-SEARCH requests to a multicast address that SSDP-enabled devices listen to. Devices that support SSDP respond with their service information.
Attackers use this method to find devices such as printers, cameras, or other IoT devices on the network. The scan reveals services running on those devices, which could be exploited if they are misconfigured or outdated.
IPv6 Scanning Techniques
IPv6 introduces a significantly larger address space, which changes how scanning techniques work.
IPv6 Scanning
Background Process: IPv6 scanning typically focuses on known or predictable address ranges (such as multicast or local network segments), as the vast address space makes traditional brute-force scanning infeasible. Scanners may target specific addresses based on patterns or devices likely to be assigned to certain ranges.
Thank you for reading this post, don't forget to subscribe!







