Hello everyone, Varsha here welcome to my new article on the very interesting topic of cryptography that what substitution cipher is, and what are its various techniques.
In this article, I will explain what substitution is and what are its various techniques. This article helps you to understand substitution techniques and how to do mathematical calculations.
Substitution Cipher
A substitution-cipher is a type of cryptographic algorithm in which each letter in the plaintext is replaced with a different letter or symbol. Substitution-ciphers can be relatively easy to break, especially if the key is short or if the message is long, as there are many patterns that can be exploited to reveal the original message.
Types of substitution cipher
- Caesar Cipher
- A modified version of Caesar’s cipher
- Mono-alphabetic cipher
- Homophonic substitution cipher
- Polygram substitution cipher
- Polyalphabetic substitution cipher
- Playfair cipher
- Hill cipher
Caesar Cipher
The Caesar cipher is a simple substitution cipher that replaces each letter in the plaintext with a letter a fixed number of positions down the alphabet. For example, if the key is 3, the letter ‘A’ would be replaced with ‘D’, ‘B’ would be replaced with ‘E’, and so on. The Caesar cipher is relatively easy to break, as there are only a limited number of possible keys (26 in the case of the English alphabet) and the frequency distribution of letters in the English language is fairly predictable.
| Plain text | H | E | L | L | O | |
| Cipher text | K | H | O | O | R |
Ex: – Let’s take the plain text “HELLO” and the key used for encryption will be 3. Now we have to convert this plain text into cipher text with the help of the Caesar cipher.
After the encryption is done, we get our cipher text. The cipher text of plain text “HELLO” is “KHOOR”. To decode the message, the recipient would apply a shift of -3 to each letter in the ciphertext, resulting in the original plaintext “HELLO”.
A modified version of Caesar’s cipher
A modified version of the Caesar cipher is a cipher that uses a slightly different algorithm than the original Caesar cipher. One example of a modified Caesar cipher is the ROT13 cipher, which is a Caesar cipher with an offset of 13 places. In other words, in the ROT13 cipher, each letter is replaced by the letter that is 13 places further down the alphabet. So, for example, the letter “A” is replaced by the letter “N”, the letter “B” is replaced by the letter “O”, and so on.
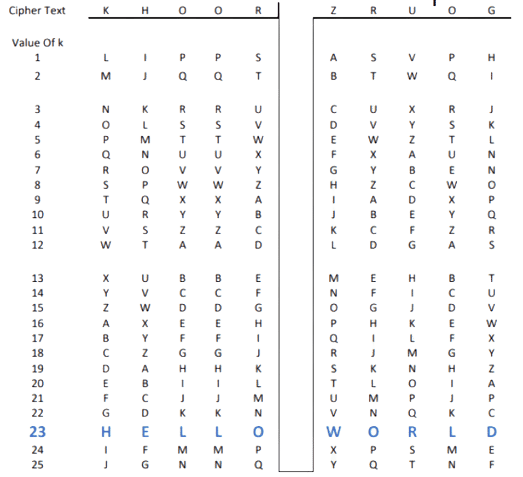
Ex: – Let’s take the cipher text “KHOOR ZRUOG” and the value of k will be 23. Now we have to convert this cipher text into plain text with the help of a modified version of Caesar’s cipher. In this, we replace all the alphabet with characters present at 23 places down the table.
After the decryption, we get our plain text “HELLO WORLD” or cipher text “KHOOR ZRUOG”.
This technique is used to decrypt the cipher text, and it is also not very much strong/secure because also in this we have only 25 possibilities.
Mono-alphabetic cipher
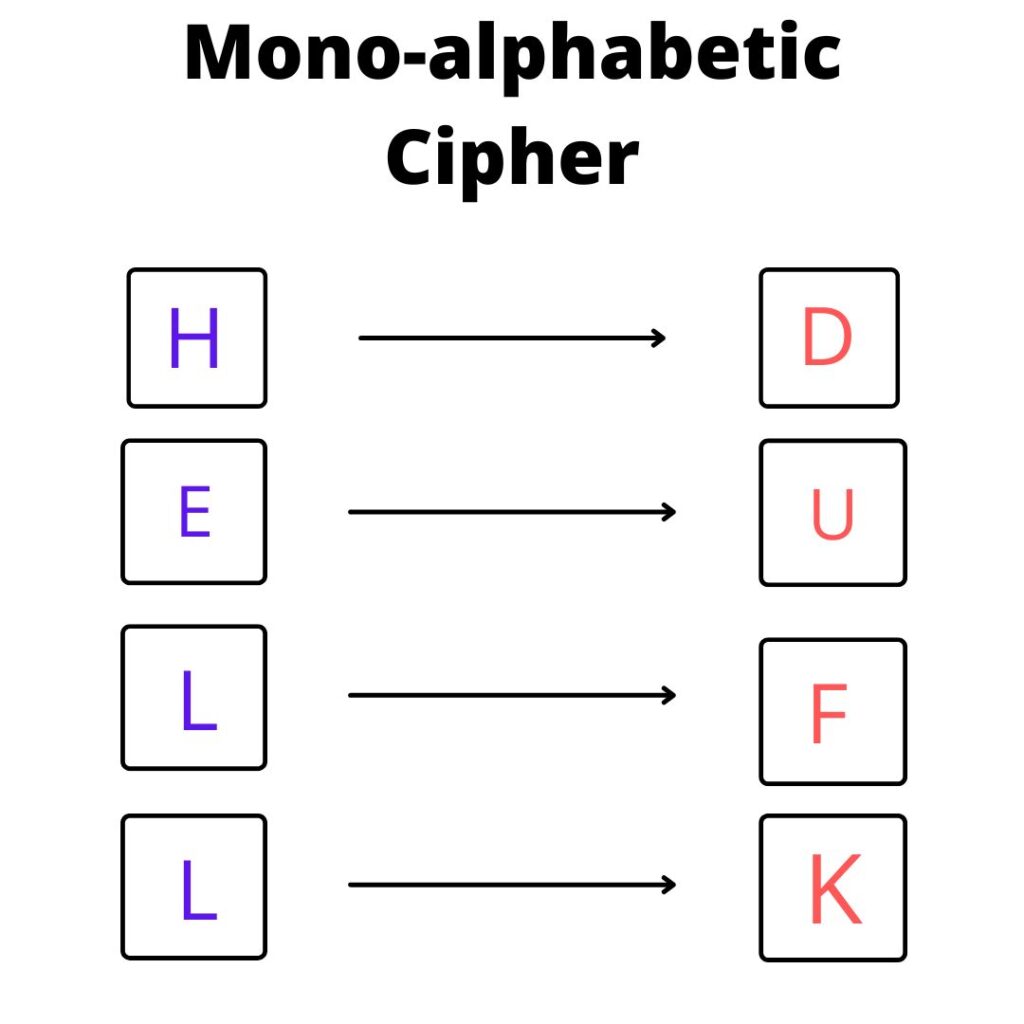
A monoalphabetic cipher is a type of simple substitution cipher in which each letter of the plaintext is replaced with a fixed letter or symbol, regardless of its position in the plaintext. But in monoalphabetic cipher, we can replace a single character with any other 25 characters, and the order of replacement is not fixed in this. Like in this we can replace A with any other characters from B to Z and B can be replaced with A or C to Z and so on.
Ex: – Let’s take our plain text “HELL”. Now we will replace all the characters of HELL with any other 25 characters, and we can repeat any character also.
Using this cipher, the plaintext message “HELL” would be encrypted as “DUFK”. Monoalphabetic ciphers are not very secure, as they can be easily broken using frequency analysis or other methods. They are mainly used for educational purposes or as a simple way to encrypt messages for fun.
Homophonic substitution cipher
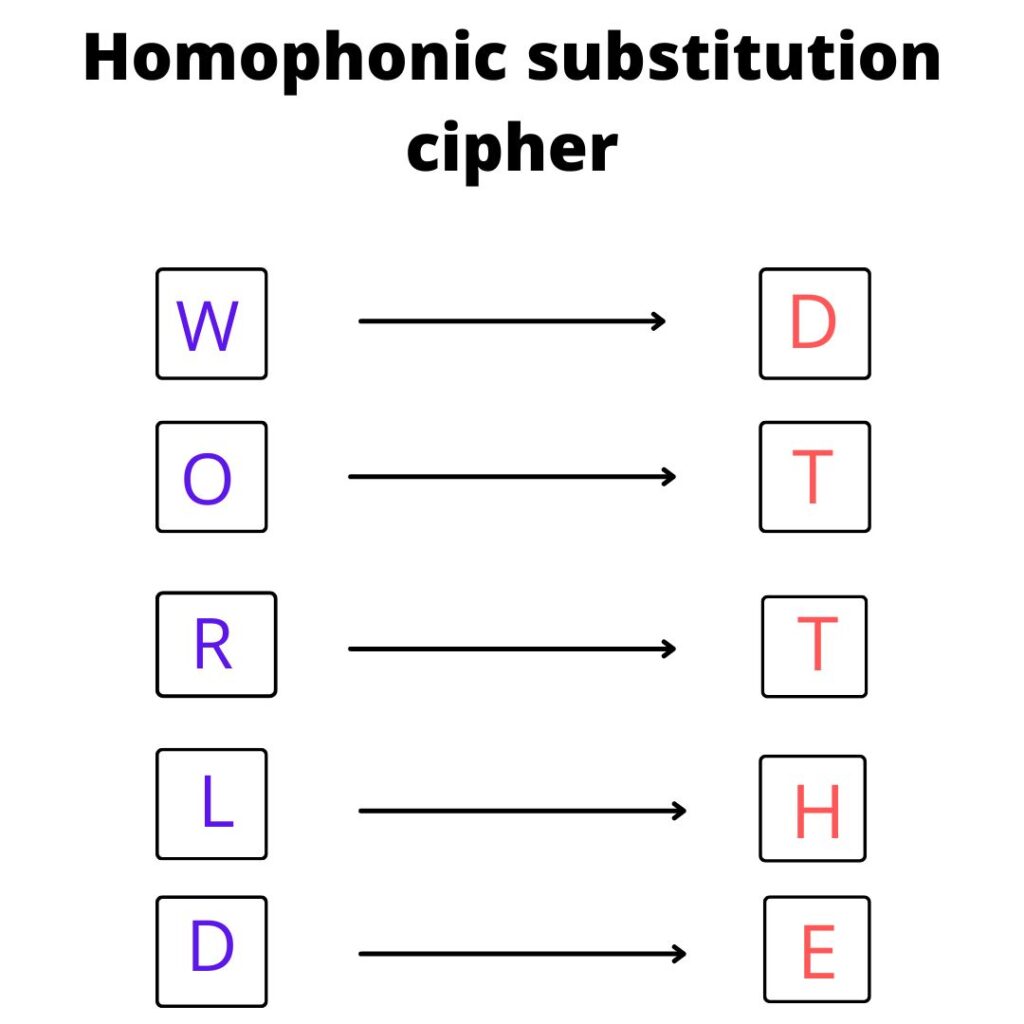
In this cipher, the plaintext letter “A” can be represented by the ciphertext letter “X”, and the plaintext letter “B” can also be represented by the ciphertext letter “X”. This makes it more difficult to determine the original plaintext based on letter frequency analysis.
In a homophonic substitution cipher, a single plaintext letter can be represented by multiple different ciphertext letters, and multiple different plaintext letters can be represented by the same ciphertext letter. This makes it more difficult to determine the original plaintext letter based on the frequency of the ciphertext letters, as multiple different plaintext letters can contribute to the frequency of a single ciphertext letter.
Ex: – Let’s take plain text “WORLD” and after encryption, it becomes “DTTHE”.
Homophonic substitution ciphers are more secure than monoalphabetic ciphers, but they can still be broken using other methods, such as word patterns or known plaintext attacks.
Polygram substitution cipher
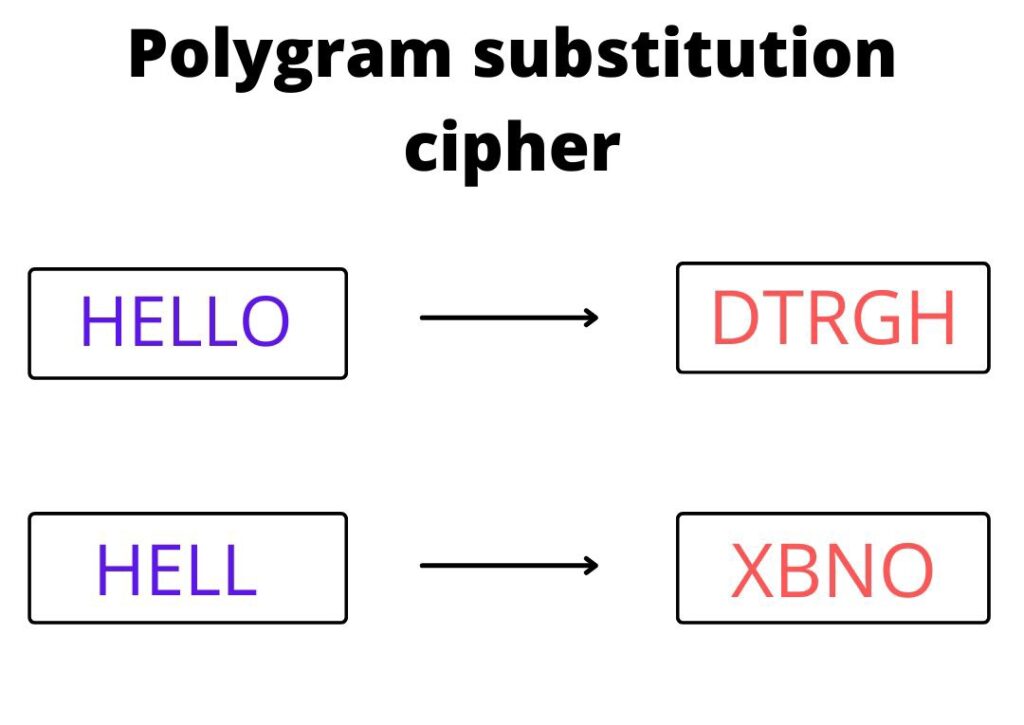
A polygram cipher is a type of substitution cipher in which groups of letters, rather than individual letters, are replaced with ciphertext. A polygram is a group of letters, typically of fixed size, that is treated as a single unit in the cipher. Polygram cipher is a block cipher in which not a single character is replaced for encryption but the whole block is replaced with another block.
Ex: – In this, we have to convert 2 blocks of plain text “HELLO” and “HELL” into cipher text with the help of polygram substitution cipher.
Polygram substitution ciphers can be more secure than monoalphabetic or homophonic ciphers, as they make it more difficult to determine the original plaintext based on letter frequency analysis or other methods. However, they are still relatively simple and can be easily broken using other techniques, such as known plaintext attacks or brute-force attacks.
Polyalphabetic substitution cipher
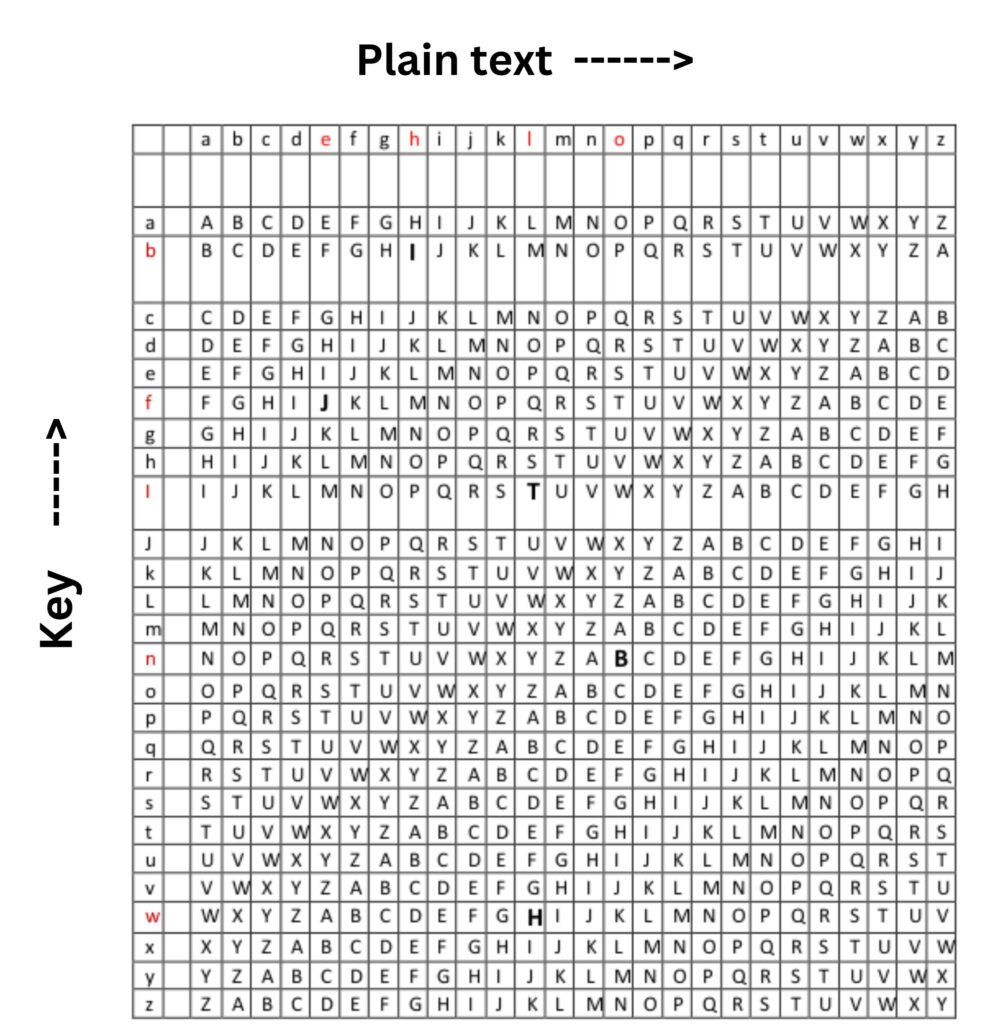
A polyalphabetic cipher is a type of substitution cipher in which the mapping between the plaintext letters and the ciphertext letters changes over the course of the message. This is done in order to make the cipher more resistant to attacks based on letter frequency analysis or other methods.
This cipher uses multiple one-character keys. Each key encrypts only one plain text character and for every character keys are different. The first key encrypts the first plain text alphabet, the second key encrypts the second plain text alphabet, and so on. After use, all keys are recycled. Thus, if we have 30 one-letter keys, every 30th character in the plain text would be replaced with the same key. This number (in this case, 30) is called the period of the cipher.
The logic for encryption is quite simple. For the key letter p and plain text letter q, the corresponding cipher text letter is at the intersection of the row titled p and column titled q. In this case, the cipher text would be F, based on the above table. In polyalphabetic cipher, we have to ensure that the size of the key should be equal to the size of plain text.
In the above figure, our plain text is “hello” and the key is “bfiwn” after encryption our cipher text is “IJTHB”.
Playfair cipher
The Playfair cipher is a polyalphabetic substitution-cipher that uses a 5×5 matrix of letters to encipher and decipher messages. It was invented by Charles Wheatstone in 1854 and is named after him and his friend and collaborator, Baron Playfair of St. Andrews.
The keyword is used to create the matrix of letters, which serves as the substitution table for the cipher. To create the matrix, start by writing the keyword (without repeating any letters) in a row. Then, fill in the rest of the matrix with the remaining letters of the alphabet in order, skipping any letters that have already been used in the keyword.
Steps for encrypting plain text: –
- Divide the plaintext message into pairs of letters.
- If the message has an odd number of letters, add an “X” to the end to make it an even number.
- For each pair of letters, locate them in the matrix and apply the following rules:
- If the letters are in the same row, replace them with the letters to their right (wrapping around to the left if necessary).
- If the letters are in the same column, replace them with the letters below them (wrapping around to the top if necessary).
- If the letters are in different rows and columns, replace them with the letters at the intersections of their rows and columns.
- Repeat this process for each pair of letters to produce the encrypted ciphertext.
Ex: – In this our plain text is “PLAYFAIR” which we have to encrypt with the help of Playfair cipher and the keyword used for encryption is “HELLO”.
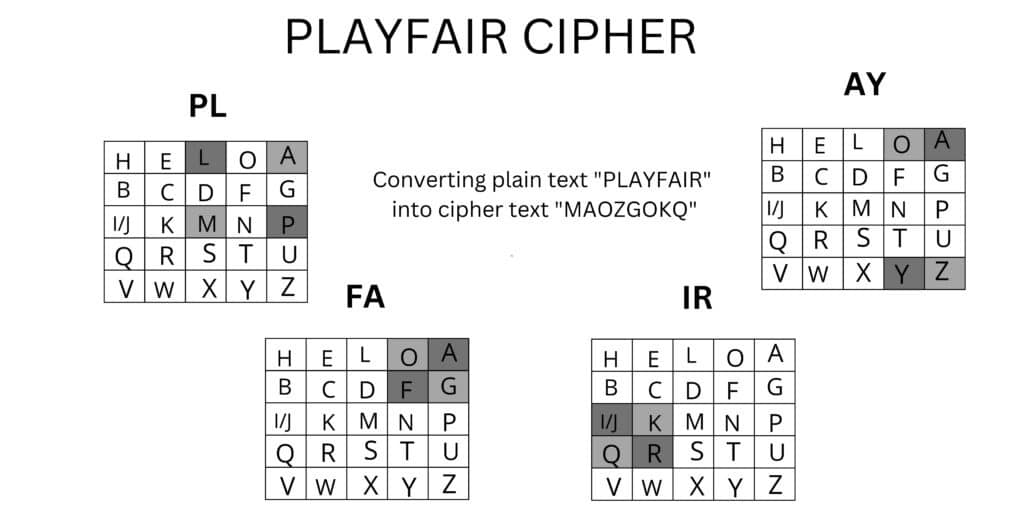
For converting “PLAYFAIR” into cipher text first, we break it into pairs of 2 alphabets as PL AY FA IR. After the encryption, our plain text was converted into cipher text as “MAOZGOKQ”.
Hill cipher
Hill cipher is a classical symmetric-key algorithm for encrypting and decrypting messages. It was developed by Lester S. Hill in 1929 and is an example of a block cipher, which means that it operates on fixed-size blocks of plaintext and ciphertext, rather than on individual characters.
Hill cipher is a type of polygraphic substitution-cipher. In the Hill cipher, the plaintext message is represented as a matrix, and a key matrix is used to transform the plaintext matrix into the ciphertext matrix. The key matrix must be invertible in order to decrypt the ciphertext back into the original plaintext.
Ex: – We take “RAT” as our plain text which we have to decrypt with the help of hill cipher. In the below diagram, it was explained step by step that how to create cipher text in hill cipher.



After the encryption, we got our cipher of plain text “RAT” as “HVB”.
Thank you for reading this post, don't forget to subscribe!