Hello everyone lucifer :), here and today we are going to see reports created by me on password hacking tools that are hydra and crunch tool.
working process of both tools is different because hydra is used for brute force attacks and crunch can be used as a word list or password-generated tool.
so let’s start with the hydra tool and then the crunch tool
Hydra
Abstract
Here we are using the hydra tool to brute-force a login on a service like FTP, ssh, etc. we can say we are going to crack the default username and password of any login credentials over the network.
we can download or create a list of default usernames and passwords which can be used for the brute force attack on the server machine.
Objective
trying to login via default username and password on a local VM machine by brute force attack using hydra tool
Introduction
It is a password-cracking tool that can be used to perform brute-force attacks on a password. Generally, we use hydra for cracking passwords of various systems including Unix, Linux, and windows.
It uses different types of dictionary attacks and pre-computed hash tables for cracking passwords, or we can say that brute force any password over any system network or server.
It is a fast and effective tool, but it is also potentially very dangerous, as it can be used to gain unauthorized access to any system.
this is why it is very important to use strong, and unique passwords and to secure systems against brute-force attacks to protect against tools like a hydra tool.
Methodology
we are using this tool on our personal machines so here am not using any disclosed password list from the internet. for demonstrating it am creating my own username and password list.
Steps:-
1. create two text files containing username and password lists for each
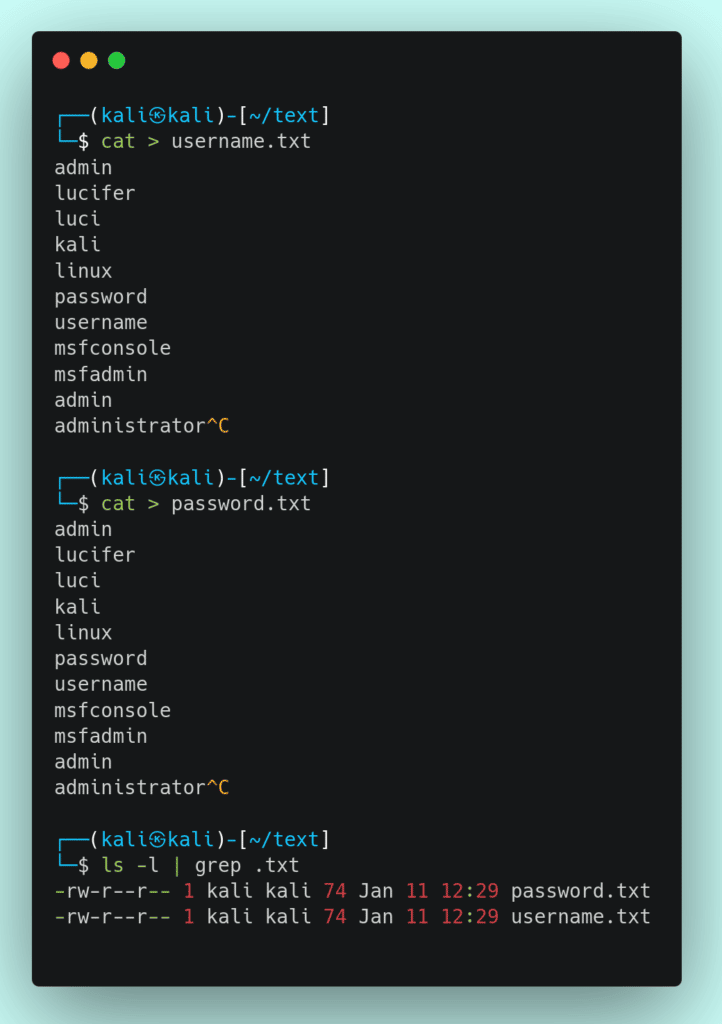
2. check that you have installed it in your system or not by this executing this command [hydra]
3. Use hydra for brute force attack and get the login credentials by command [hydra –L {path username} -P {path password} ftp://targetip] instead of FTP you can use ssh telnet etc., anyone.
Conclusion
we can use this tool to get login credentials of any server via their open port service. It may be a major server misconfiguration that hydra can use to get credentials.
Here the server is not configured for limiting the logins per user which result in a successful brute force attack. We can use it on every port service which gives a better result as compared to doing only one.
Crunch
Abstract
so basically crunch is a password-generator tool that is able to generate specific types of passwords as per your requirement.
It can generate a list of passwords as per the keywords and length you specified in it.
we need this tool because if we want to brute force anyone’s password, and we know some patterns of how he uses a password then as per that patterns and clues we are able to generate a specific list of passwords by the crunch tool.
Objective
generate a password list of a minimum of 6 and maximum of 8 characters which start from upper case characters then lower case and special characters with symbols
Introduction
It is a word list generator where you can specify a standard character set or a character set you specify, and it generates all possible combinations of characters up to a specified length.
It is often used to create word lists that can be used to guess passwords or to crack password hash dictionaries.
Methodology
Here we are going to generate a password list by specifying the character set and length as we require, and we will store that output in a text file.
Steps
1. First, we need to check whether we have installed it in our system or not by command [ crunch ]
2. create a password list with a specific set of characters and lengths and then store it in a text file. Command [ crunch 3 6 abcd -o ./password.txt ]
here 3 is the minimum length and 6 is the maximum length of the words. there are some keywords in the crunch tool that are placed after [ -t ] for special characters. [ @ – lower case ] [ % – numbers ] [ , – upper character ] [ ^ – symbol ]
Let’s generate a special character password list that is like a combination of five letters.
You can see the generated list by generating it in your system. Follow the steps and commands as specified then you can generate a password list as per your requirement.
from the above command, we can generate a password list like Aa0A!, Aa0A@, Aa0A#, Aa0A$, Aa0A%, Aa0A^, Aa0A&, Aa0A*, Aa0A(, Aa0A), Aa0A-, Aa0A_, Aa0A+, Aa0A=, Aa0A~, Aa0A`, Aa0A[, Aa0A], Aa0A{, Aa0A}, etc.
The total words we get in that password list are 1115400 words.
If you have any queries regarding the above content, or you want to update anything in the content, then contact us with your queries. You can directly post your question in the group.
Connect with us on these platforms