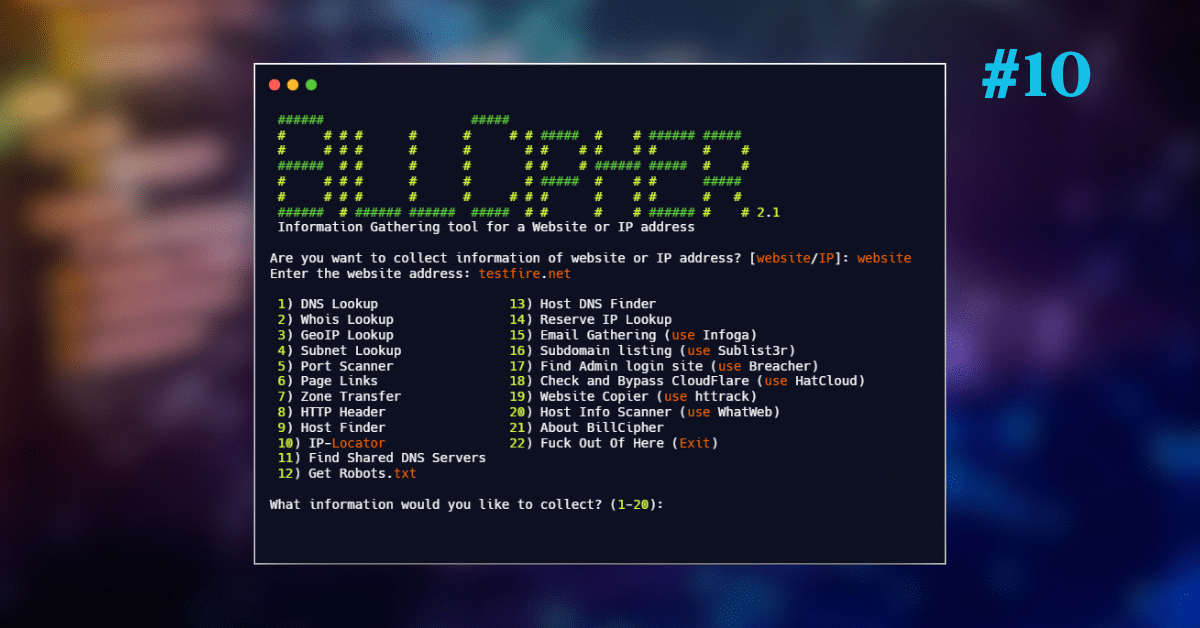
BillCipher is an open-source command line tool for information gathering of any website, domain, and IP address. It is an Open-source intelligence information-gathering tool available for Linux OS.
This tool is straightforward to use and helpful in doing reconnaissance. It is freely available on GitHub by Bahatiphill.
It is somewhat similar to the other information-gathering tool, including Metasploitable 1 and Metasploitable 2.
BillCipher can work in any operating system if they have and support Python2, Python 3, and Ruby. It is developed with Python and Ruby languages.
It has many modules, such as database interaction, command completion, interactive help, and built-in convenience functions. It provides a very powerful environment for OSINT-based information gathering.
Information that can be gathered by using this tool
- DNS lookup
- Whois lookup
- GeoIP Lookup
- Subnet lookup
- Port Scanning
- Page Links
- Zone Transfer
- HTTP Header
- Host Finder
- IP-Locator
- Find Shared DNS Server
- Get Robots.txt
- Host DNS Finder
- Reverse IP lookup
- Email Gathering (use Infoga)
- Subdomain listing (use Sublis3r)
- Find Admin Login Site (use Breacher)
- Check and Bypass Cloudflare (use HatCloud)
- Website Copier (use httrack)
- Host Info scanner (use WhatWeb)
How to install and run BillCipher
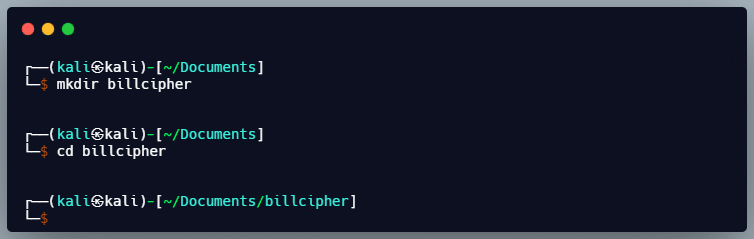
1. First, create a directory for keeping the tool files and navigate to it.
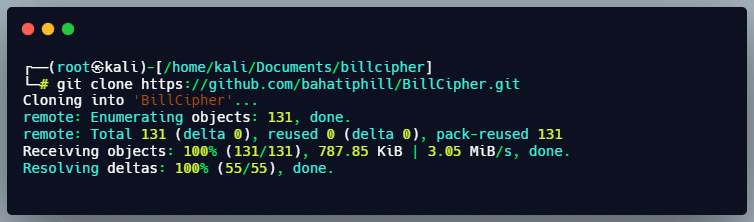
2. Now, we need to clone the BillCipher Repo from GitHub in this directory. GitHub Link [click here]
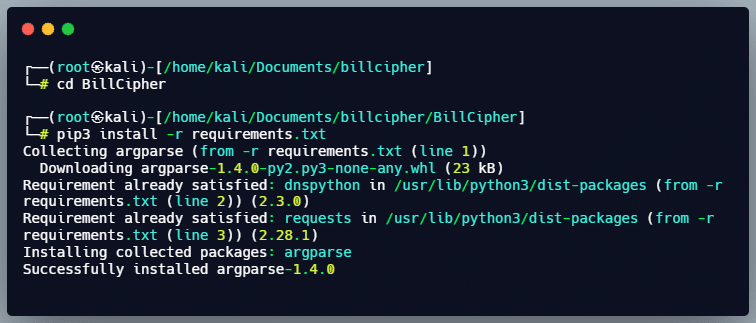
3. Navigate to the tool directory, then install the requirement.txt file by entering the command [pip3 install -r requirements.txt]
4. Now you can run the tool by entering the command [python3 billcipher.py]
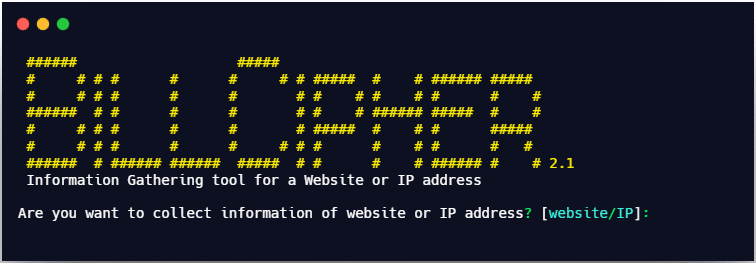
This is how you can install billcipher in your Linux OS.
How to use it for information gathering
1. first, run the tool in the terminal by the command as shown above.
2. After that, you need to specify whether your target is a website or an IP. Here I am choosing a website by entering the command [website] and then enter the website domain name [here, testfire.net]. Now you need to specify what information you want to gather by choosing the option number.
I want DNS information so I will choose [1] and press enter.
[website] -> [testfire.net] -> [1]
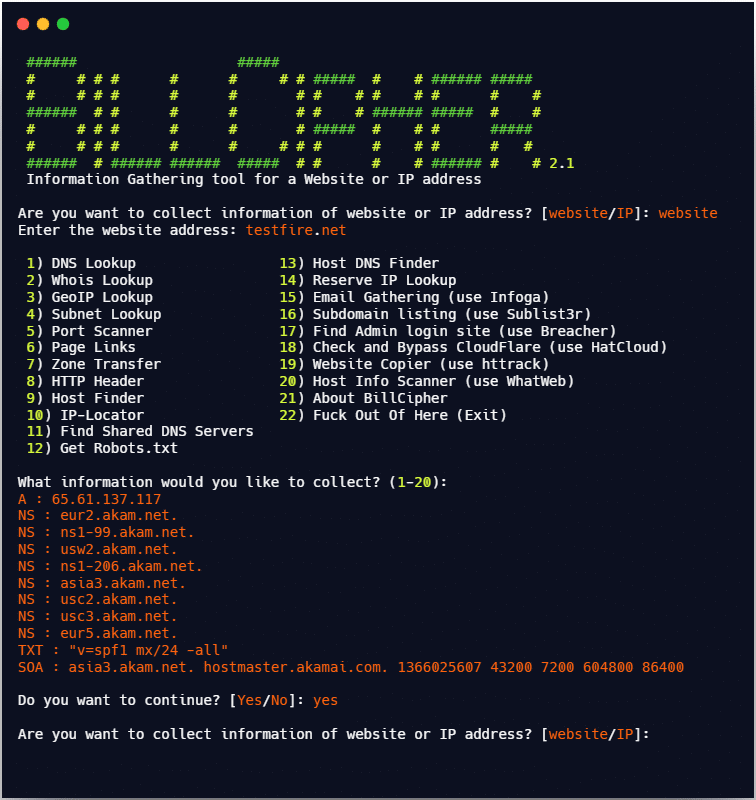
Reverse IP Lookup
For getting information about reverse IP lookup we need to choose option 14
[website] -> [testfire.net] -> [14]
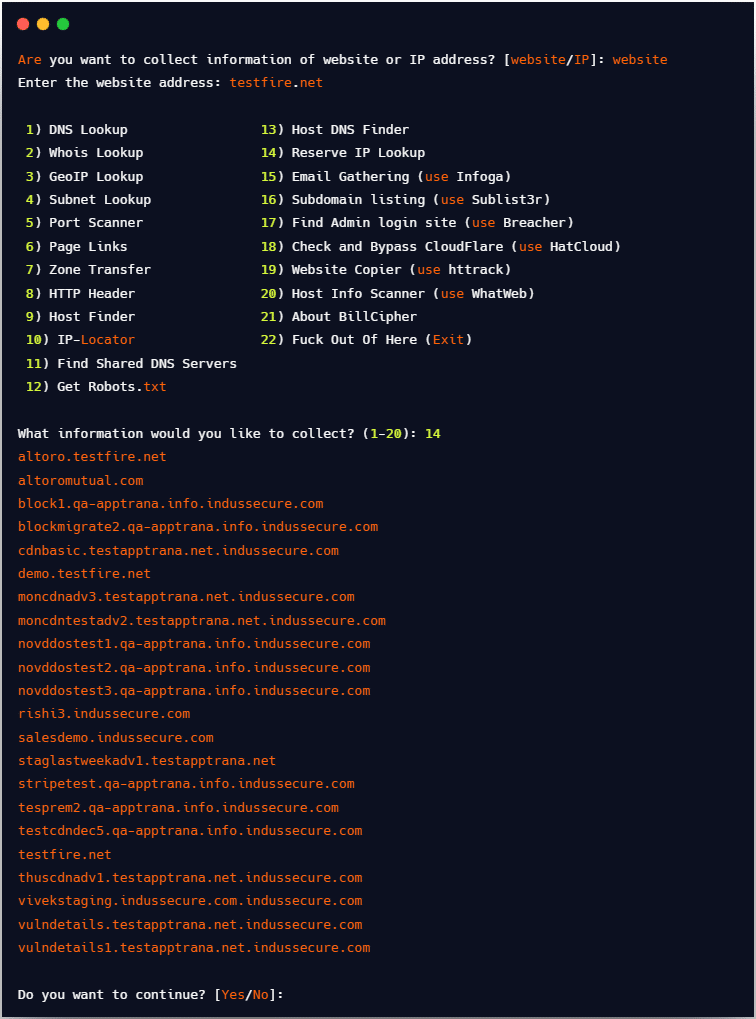
This is how you can use different tools or modules in BillCipher for footprinting your target and collecting different information about the target.
Do practice with other modules and see what results you were getting from them.
The process will be the same for every module first enter what your target is like IP address or website, then specify their name for the website it will be the domain name and for the IP address, it will be the numerical value of the IPv4 address and then choose your module and get the information from there.
Thank you for reading this post, don't forget to subscribe!