In this ever-changing sphere of cyber security, it becomes utmost important to understand the any hacking methodology. Such knowledge is directed not only to defend a system against an attack but also to conduct ethical hacking.
Hacking is not mere exploitation of weaknesses; rather it is basically a systematic process comprising planning, reconnaissance, exploitation, and post-exploitation activities.
This article discusses the stepwise methodology in hacking, presenting a step-by-step tutorial for cybersecurity professionals, ethical hackers, and any curious individual who wants to know how hackers function.
Introduction to Hacking Methodology
Hacking methodologies refer to the systematic method used by an attacker to identify, exploit, and leverage weakness in target systems. Although their intent could be malicious or ethical, methodologies used do not differ that much.
Ethical hackers or white-hat hackers will conduct their works of identifying and fixing vulnerabilities using similar methodologies before a black-hat hacker exploits them for wrongful gain. On the other hand, black-hat hackers draw upon the same techniques as white-hat hackers to gain personally, steal data, or to exploit others, either maliciously or frivolously.
An understanding of hacking methodology is fundamental for any security personnel to know what kind of process a hacker might use to evaluate, attack, or breach a system. This enhances their knowledge of how to predict a hacker’s malicious behavior and, therefore, protect their organizations’ systems and networks.
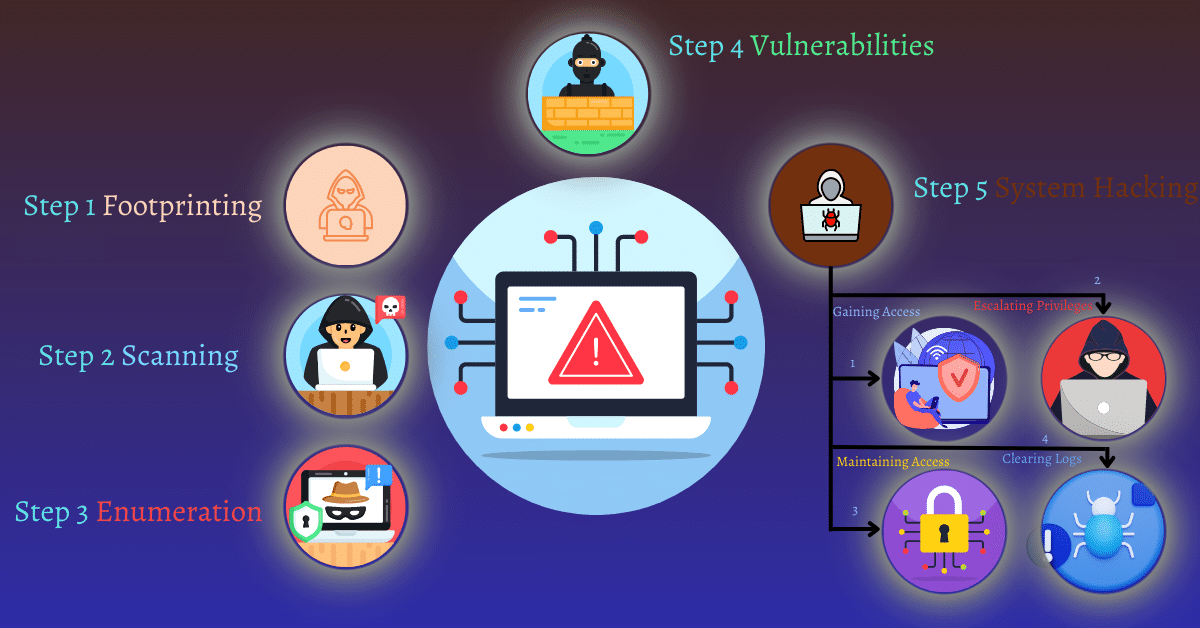
The Five Phases of Hacking
The hacking process can be broken down into five distinct phases. Each phase serves a specific purpose and builds upon the previous one. These phases are:
- Reconnaissance
- Scanning
- Gaining Access
- Maintaining Access
- Covering Tracks
Let’s explore each phase in detail.
Detailed Breakdown of Each Phase
Phase 1: Reconnaissance
Reconnaissance or information gathering is the first and most important step in the hacking process. The hacker now begins collecting as much information about the target as possible, from IP addresses to domain details, network topology, employee data, and so on.
They are broadly categorized into two types: passive and active:
Passive reconnaissance: The collection of information inactive with no kind of interaction with the target. Examples include searching public databases, social media, and websites.
Active reconnaissance: The interaction with the target using some kind of tool. Examples include pinging the target, or employing utilities such as Nmap to try to obtain information. The objective of reconnaissance is to identify possible ways into the system and find any form of exploits the attacker could utilize in later stages.
Phase 2: Scanning
Once complete, all the information gathered allows the hacker to proceed to scanning. During this stage, the hacker employs a series of tools and techniques to find open ports, services, and vulnerabilities residing in the target system.
Some of the key activities in the scanning phase include:
- Port Scanning: Finding open ports and services that are running on the target system.
- Network Mapping: Constructing a map of the target network to comprehend its formation.
- Vulnerability Scanning: Automated scans using tools like Nessus or OpenVAS, looking for known vulnerabilities.
Thus, in the scanning phase, all the weaknesses of the target are exposed for the hacker, which can later be taken advantage of.
Phase 3: Gaining Access
At this stage, the act of penetration commences. A hacker, with the knowledge acquired from the previous phases, now attempts to harness vulnerabilities to gain unauthorized access.
Common techniques you can expect in this phase may be the following:
- Exploiting Software Vulnerabilities: Taking advantage of known bugs or flaws in software packages with the help of exploits.
- Cracking: Password Cracking in other words brute-force or dictionary to guess passwords.
- Social Engineering: tricking a person to provide some sensitive information.
Once the hacker gets access, he can run his trojans or worms, grab password information, or install the backdoor on the target system for future access.
Phase 4: Maintaining Access
Once the hacker has a foothold inside the target system, the next goal is to maintain access to the system so that they can return and repeat the process of exploitation at their own timetable.
The keeping of access could take many forms:
- Install backdoors: These are hidden entry points through which a hacker could circumvent normal authentication.
- Rootkits: Installation of malicious software that provides the hacker with privileged access, remaining undetectable by the user.
- Creating new user accounts: Adding new accounts with administrative privileges to ensure continued access.
Maintaining access is most important for cybercriminals whose goal is to use the system for long-term purposes, such as to further their attacks or to steal data over a protracted period of time.
Phase 5: Covering Tracks
This last act in the media-theoretical ERP scheme is to leave minimal traces on the hacked system.
An attack remains undetected through the erasure of any incriminating communication that leaves tracks behind it.
Common techniques for covering tracks include:
- 1.Clearing Logs: Deleting or altering system logs to remove records of the hacker’s activities.
- 2.Using Encryption: Encrypting files and communications to hide their contents.
- 3.Spoofing IP Addresses: Masking the hacker’s real IP address to avoid being traced.
Hackers decrease the chances of getting caught and thus increase the chance of a successful attack.
Tools Used in Hacking Methodology
Hackers use a variety of tools to carry out their activities. Some of the most commonly used tools include:
Nmap: A network scanning tool used for port scanning and network mapping.
Metasploit: A penetration testing framework that provides exploits and payloads for gaining access to systems.
Wireshark: A network protocol analyzer used for capturing and analyzing network traffic.
John the Ripper: A password-cracking tool used to guess passwords through brute force or dictionary attacks.
Nessus: A vulnerability scanner used to identify known vulnerabilities in a system.
These tools are widely available and can be used for both ethical and malicious purposes.
Ethical Hacking vs. Malicious Hacking
While the methodology of hacking remains intact, the difference between ethical and malicious hacking lies in the purpose of their actions.
Ethical Hacking: This is done by cybersecurity professionals permitted by the target organization. And the objective of this exercise is to find and fix vulnerabilities before fretted by malicious hackers.
Malicious Hacking: This is done by individuals or groups aiming to inflict harm, steal data, or grant themselves unauthorized access for personal gain.
Thus, ethical hackers play an essential role in system and network security, and hence the malicious hackers become a considerable hazard to cybersecurity.
How to Defend Against Hacking Attempts
After grasping the hacker methodologies, let the defense against attacks commence. Here are a few pointers for protection:
- Routine Software Updates: Make sure the software and systems keep up with all new releases or versions to fix well-documented vulnerabilities.
- Adopt Strong Password Policy: Creating strong passwords and following up with a policy of two-factor authentication.
- Carrying Out Security Audits: Do portfolio evaluations and penetration tests to determine vulnerabilities or weaknesses.
- Network Traffic Monitoring: This would involve using an intrusion detection system (IDS) and an intrusion prevention system (IPS) to monitor activity and, if so instructed, block suspicious activity.
- Educate Employees: All employees should be made aware of social engineering attacks and how to avoid them.
Taking such steps will help to greatly minimize the chances that a company might fall prey to a hacker.
Protect Yourself: What and what not to do?
- Do not post sensitive information about security questions on social media.
- No brute-force-guessing passwords.
- Consider two-factor authentication.
- Be wary of emails requesting your password. Companies such as Heroku, Google, and others do not request your password for some type of promotion or service.
- Authenticate the source of communication.
- Investigate a link before you click on it.
- Scan any new file before clicking on it, especially batch files.
- Check for background services running on your device regularly, and don’t depend too much on what others have done on theirs.
- Be sure to update your antivirus software and set your system to provide root passwords for installation.
- Log out of sessions and clean caches.
- Inform your service providers if you suspect a compromise, for when confirmed inform the cyber-crime department. Such events are treated more seriously these days. Stay safe, and don’t become the victim!!
Thank you for reading this post, don't forget to subscribe!