Table of Contents
ToggleHello reader, this article is dedicated to discussing how you can extract information about your target organization by footprinting through web services tools.
Web services tools include social networking sites, people search services, alerting services, financial services, and job sites, that can provide information about the target organization.
The collected information may include infrastructure details, physical location, employees detail, network details, security infrastructure, and other critical information about the target organization.
Tools and Web services we are going to use and discuss:-
- Netcraft:
- For getting information about target organization domains and subdomains
- PeekYou
- For getting personal information about target people of an organization or individual
- theHarvester
- This tool is useful for getting multiple information about the target, but we will see how to email address of the target
- Censys
- For getting information about the target network system like OS, IP, and Security Protocols.
- Deep and Dark web By Tor Browser
- For getting any critical information about the target organization that is not available on the surface web or not indexed one
Footprinting Through Netcraft
Netcraft is a web service tool that can provide us with information that includes domains and subdomains of any organization.
It is loaded with much information about your target that can be very useful for the footprinting and understanding of your target infrastructure.
For using the Netcraft web service tool you need to navigate to its website :Netcraft:
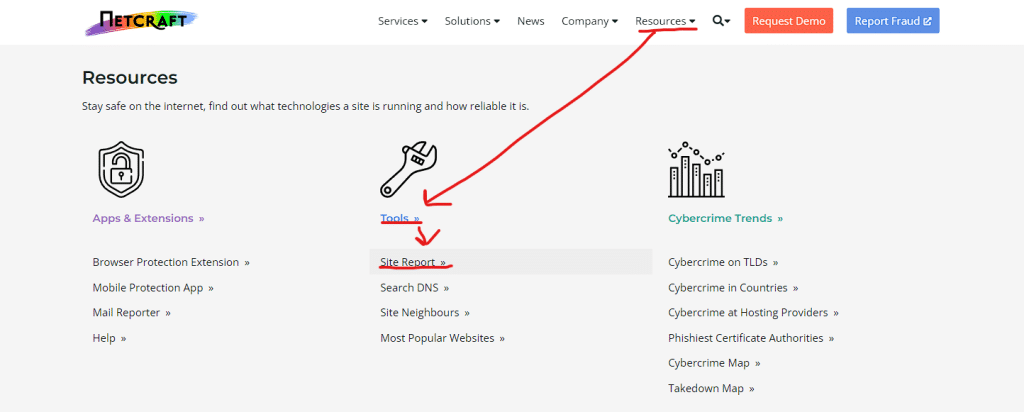
Then navigate to the Resources -> Tools -> Site Report [as shown in the image below]
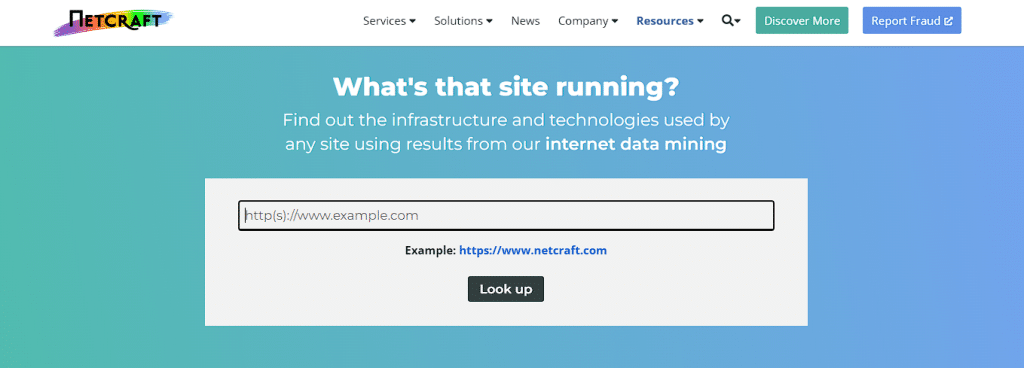
The Netcraft tools will have appeared as shown in the image below
Now you can give your target organization domain for getting information about it. I am using Microsoft.com as my target organization for example.
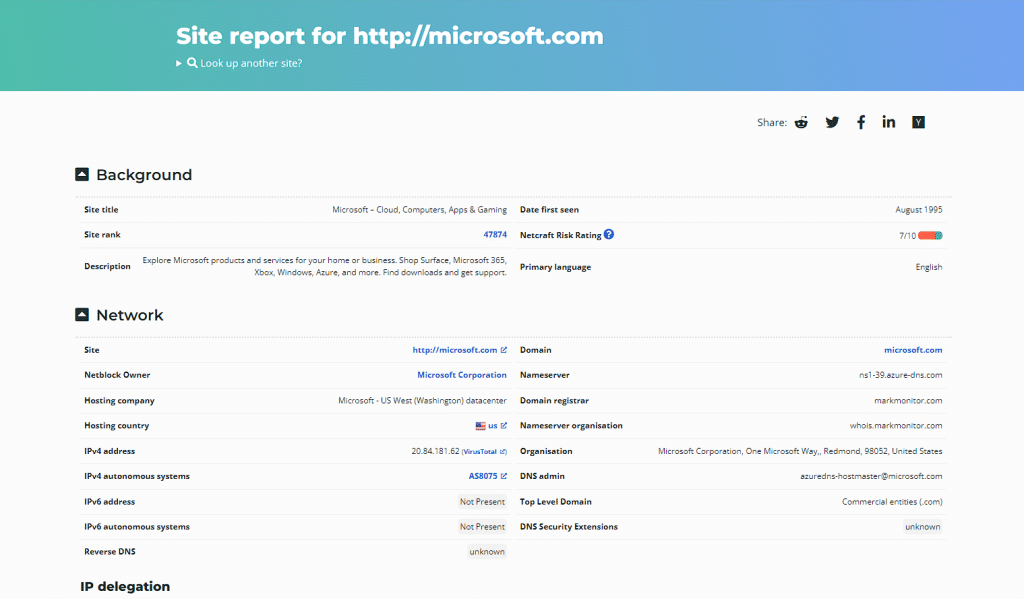
Now you will get all the possible information about your target organization’s network infrastructure that can be very useful for understanding target network security and vulnerabilities.
Footprinting through PeekYou
Peekyou is a web service tool that allows you to find people in any state by searching their names or social media usernames.
This can help you to gather information about your target organization’s employees, admins, or the owner itself.
This web service can include information like names, contact details, address detail, date of birth, photographs, videos, family and friend details, professional details, social networking profiles, property information, and optional background on criminal checks.
You can navigate to the Peekyou website from this link [PeekYou]
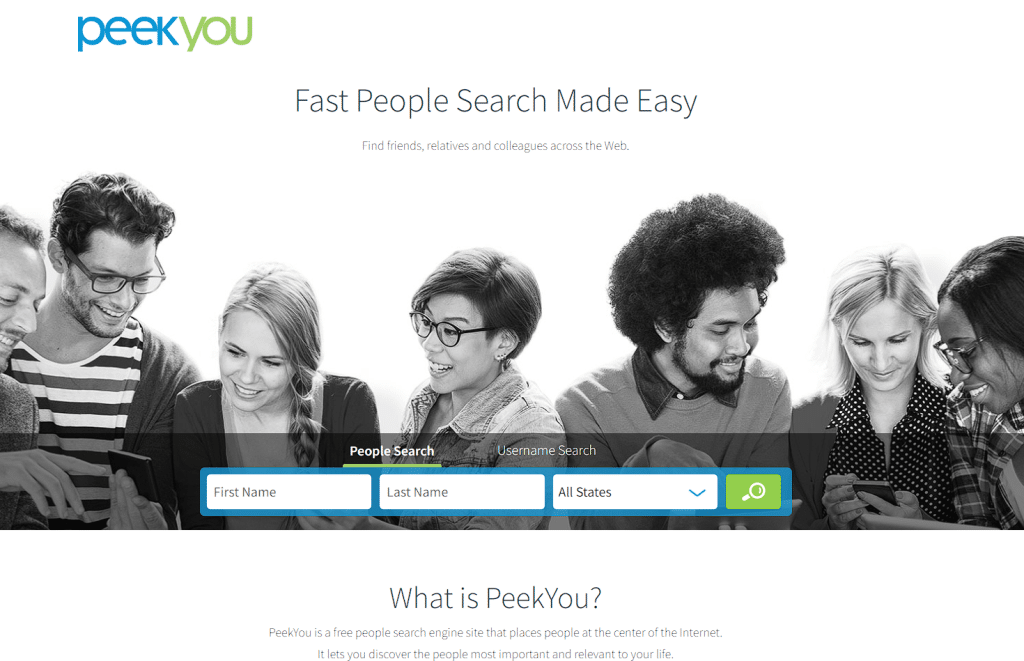
the website looks like the above image. now you need to enter the first and last name of your target person and then search for them.
I am choosing Mark Zuckerberg as my target person only for the explanation.
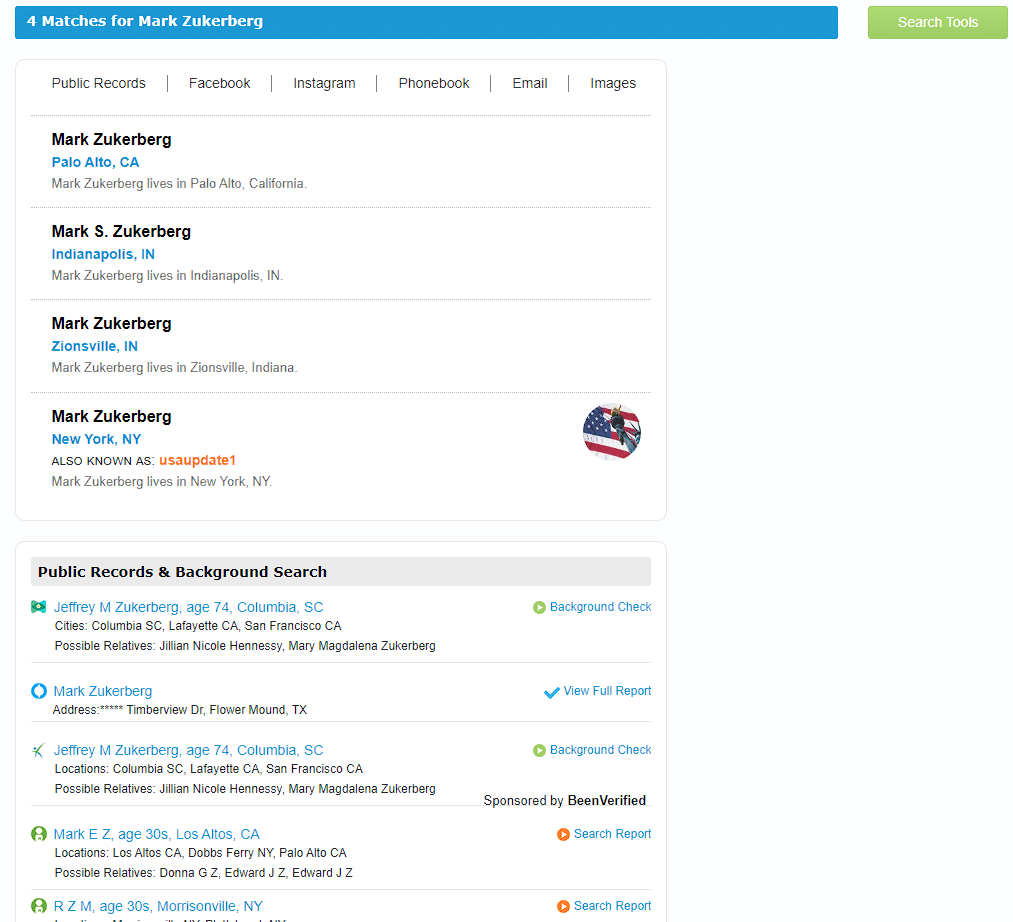
here you’ll see all the personal and professional details about the target person. This information is helpful in understanding our target person’s personal life and professional life which leads to a successful social engineering attack.
Footprinting through theHarvester
theHarvester is the OSINT tool for the footprinting stage to help determine a domain’s external threat landscape. It will help to get information like names, emails, IPs, domains, subdomains, and URLs by using multiple public resources.
We will use a harvester tool for gathering email information about our target organization. Because emails are like the personal identification of any employee or organization.
So, gathering email information of critical personnel is one of the key tasks of the footprinting stage.
You can check our article on theHarvester tool for installation and use information
Check for theHarvester tool in your terminal by the command: theHarvester
now for gathering email information about your target organization. you need this command type theHarvester -d amazon.com -l 100 -b duckduckgo and press enter
Note: here -d specifies the domain or company name to search, -l specifies the number of results to be retrieved, and -b specifies the data source.
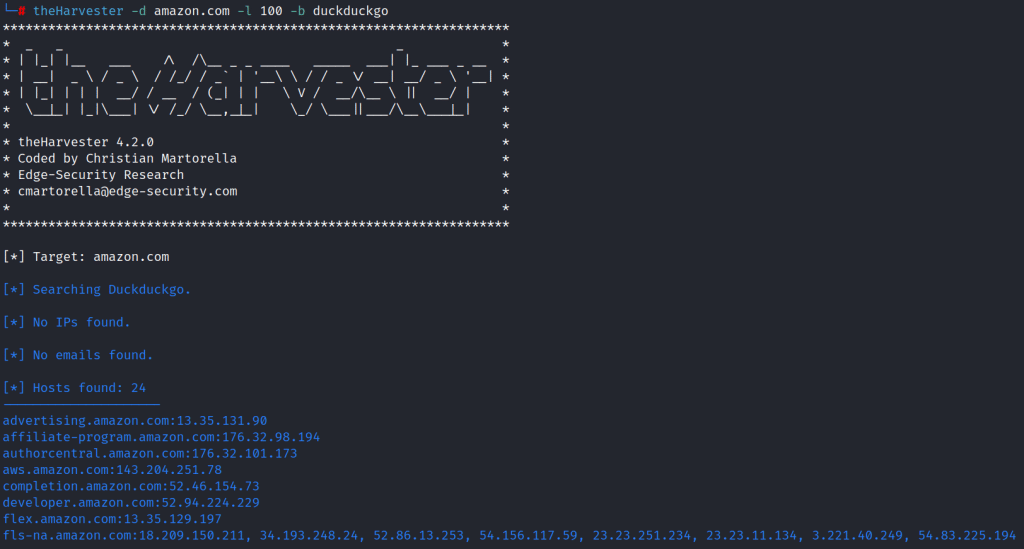
here I choose amazon.com as my target and I got these emails information from the tool. This will help me in finding a person’s personal detail and a way to successful social engineering attacks.
Footprinting with Censys web service
Censys is a web service tool that is used for getting crucial information about the target operating system, and it will help you with much other information gathering.
Censys can gather information that includes the operating systems, IP address, city, country, latitude/longitude, and hostname of the target organization.
Here I am choosing microsoft.com as my target and I will try to gather information about their operating system and location city.
You can navigate to the Censys search engine from here.
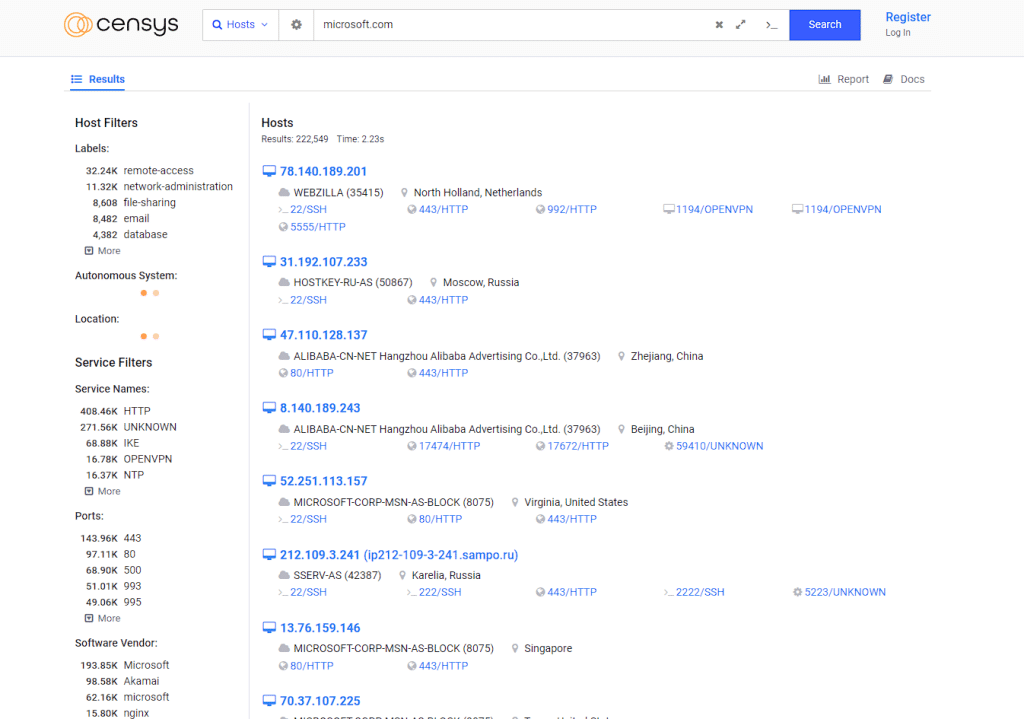
The above image shows the information I got from censys tool that includes IP addresses, Protocol, location, and OS details.