Table of Contents
ToggleHello, guys lucifer here, and in this article, we will discuss the steps and ways to perform footprinting through search engines. Here we will collect publicly available information about our target for making future attacks and understanding target networks.fsdf
It is the first step in Ethical Hacking for understanding and gaining information about our target for future attacks.
We will learn how we can use different types of search engines to collect different types of data through them and use them to analyze and understand target networks and behavior.
Here we use search engines like Google (Dorks), YouTube Metadata (Reverse Image Search), FTP search Engines, and IoT Search Engines.
Let’s discuss the steps and processes of every method in different search engines.
Footprinting with Advance Google Hacking Techniques
Doing footprinting with Google’s advanced search tricks sometimes makes your search clear and specific to any topic or content you want to gather. These tricks limit the search result around to your query, it will not show unnecessary results for you.
Let’s take an example of the login page of any company. Here we need to fetch all the login pages related to that company domain.
so if you directly search for all login pages of xyz.com then it will show unnecessary pages too with all login pages. so here we need to limit our search results to only the things we need to fetch.
Let’s fetch the login pages of Microsoft.com
1. Go to Google and type your query “So all the login pages of microsoft.com”
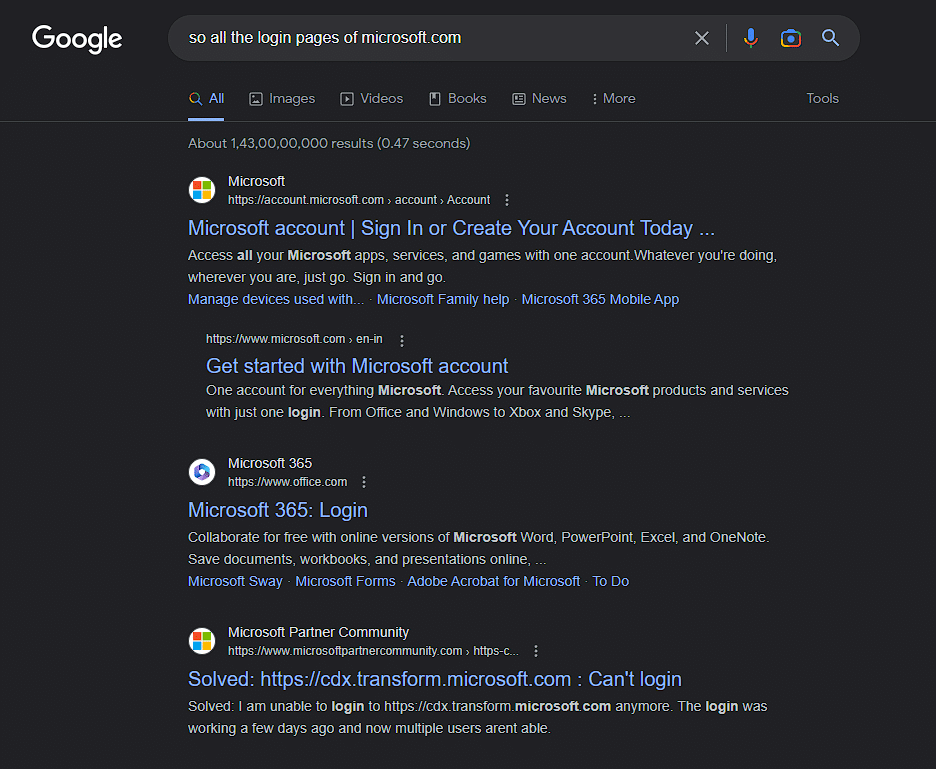
Here our results are not only specific to the login pages for the website Microsoft. so now we will use advanced search queries for getting exactly what we want.
for the login page, our query will be like “intitle:login site:microsoft.com” It sorts all the login pages related to Microsoft domain and shows the result of it
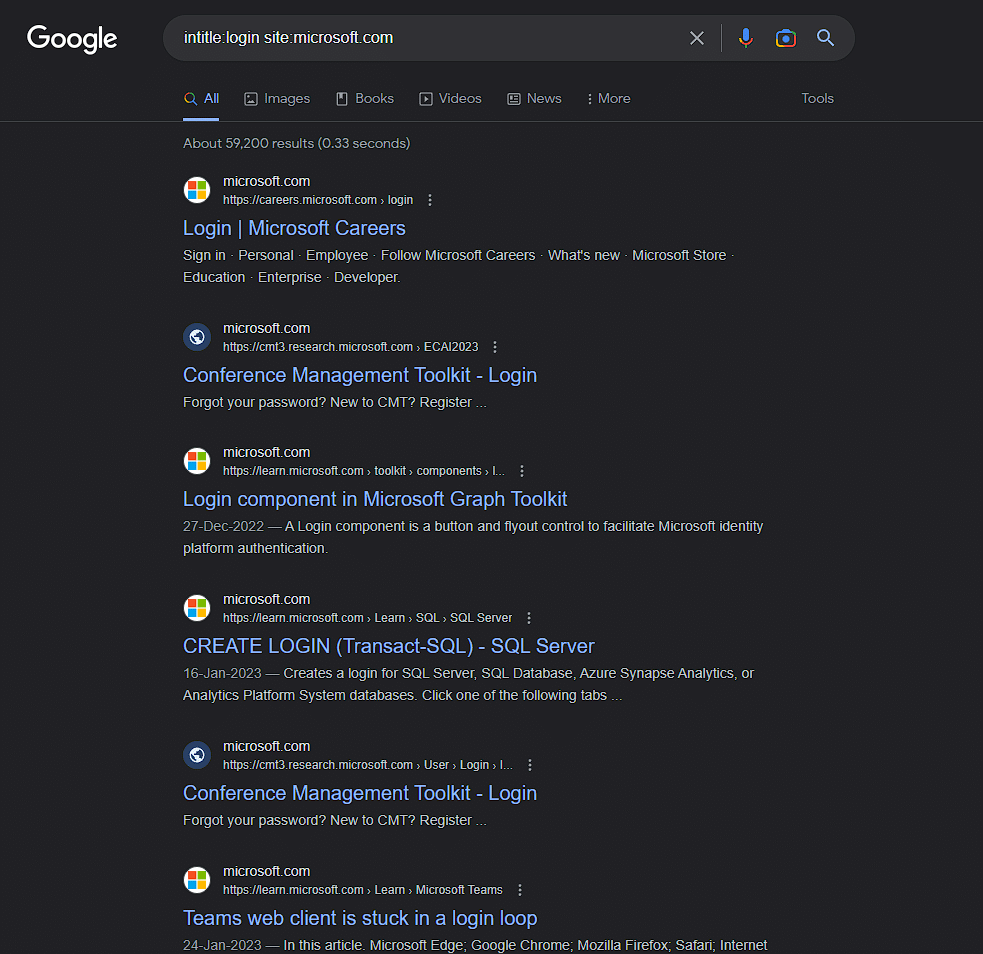
Now here our search results are only specific to login pages of microsoft.com
Let’s take another example for getting any PDF of a specific topic. Like PDF name is certified ethical hacker now our query will be like “intitle: certified ethical hacker filetype:pdf”
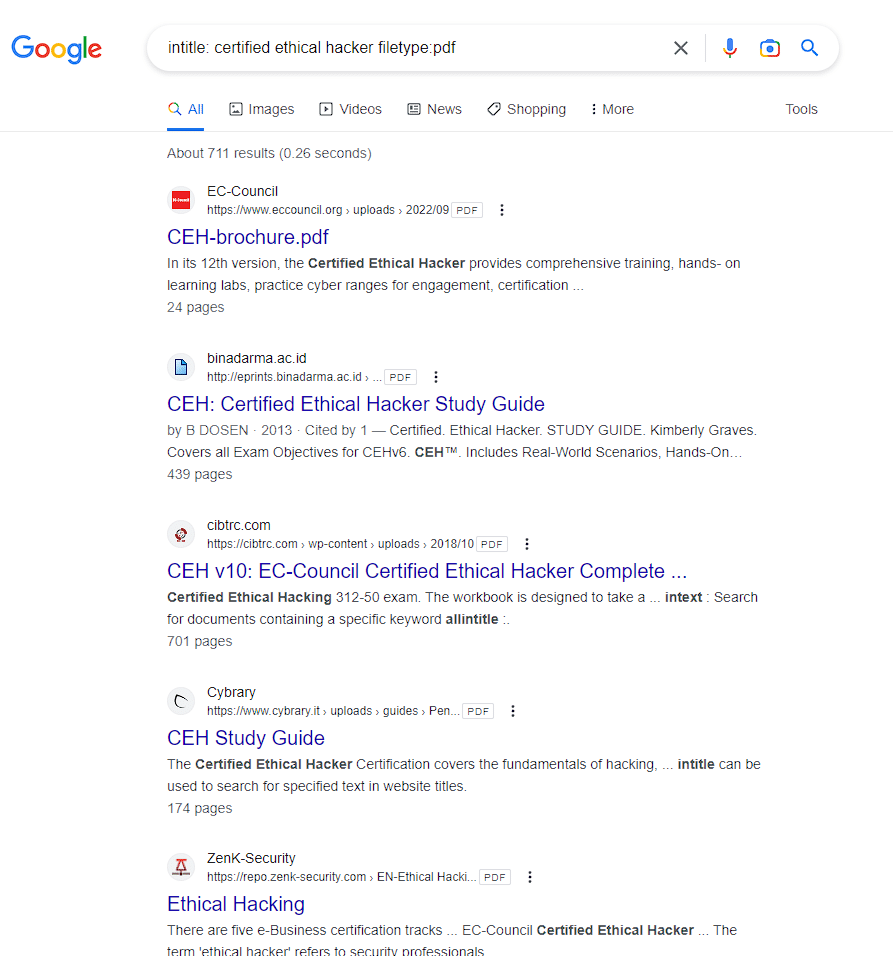
here all the results contain a file-type PDF related to the title certified ethical hacker. this is how we can use the Google Advanced search operator for any specific search terms that will limit the result and show only what we want.
It will save our time and work for getting information about any query we want.
Footprinting with video search engines
Video search engines are internet-based search engines that title the information about the video that you are looking for. They contain all the details about any videos that are uploaded to the internet.
Like video ID, content ID, publisher name, server details, publishing date, etc. information that is related to that video. These search engines crawl the metadata of the videos for getting their information.
These types of information can help you in understanding someone’s behavior and network system and what thinking they kept over the internet.
here we are going to perform an advanced video search and reverse image search by using the YouTube search engine and YouTube metadata tool kit.
Let’s target an organization named cipherssecurity and here we will use one video of it for getting as much information about the target.
1 first search cipherssecurity on YouTube and copy the link of “How RSA algorithm works with an example explained in simple terms” video as an example.
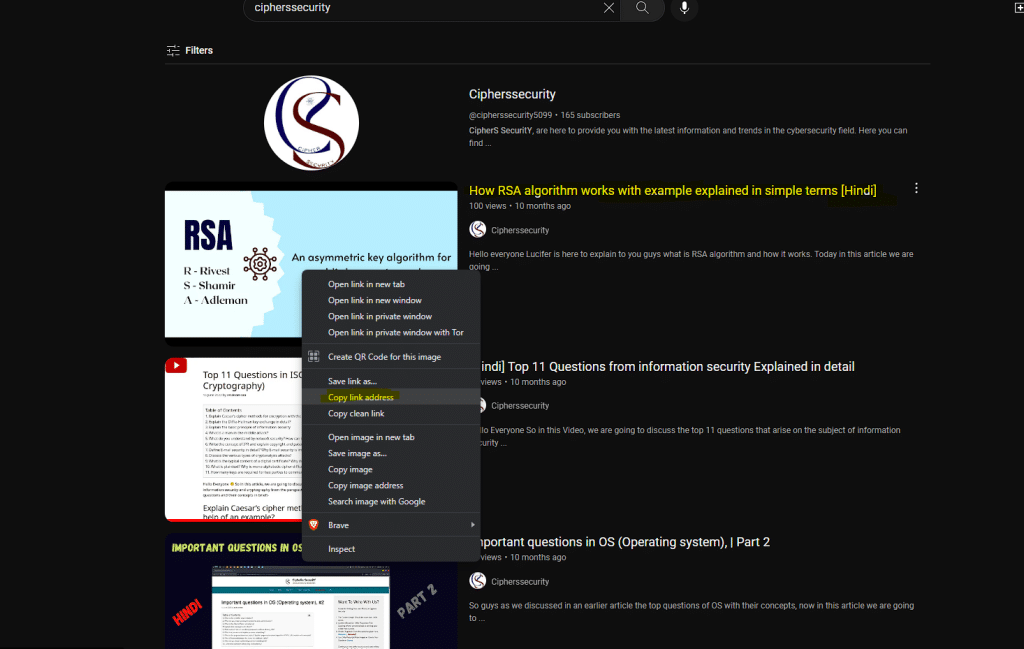
after copying the link now go to this website (YouTube Metadata search) and paste your link over here and click the submit button.
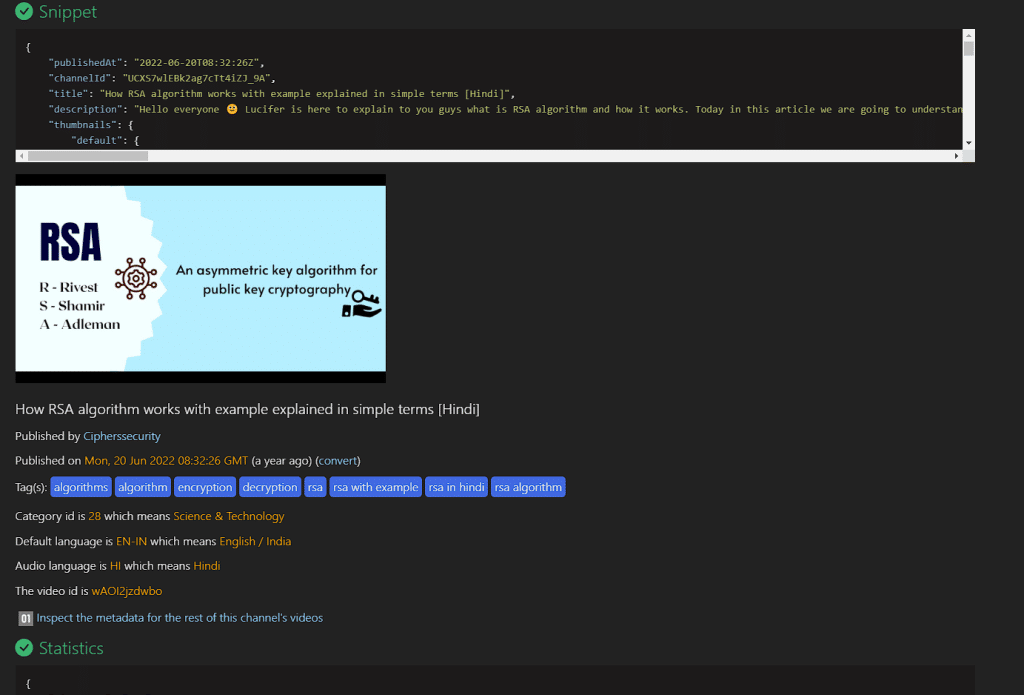
here you will get information about video details like published date and time, video ID, channel ID, title, publisher, etc. in the snippet section.
you can explore and observe more details like images and geolocation of the video and others in the metadata search engine.
you can do a reverse image search with a thumbnail image in the Thumbnails section
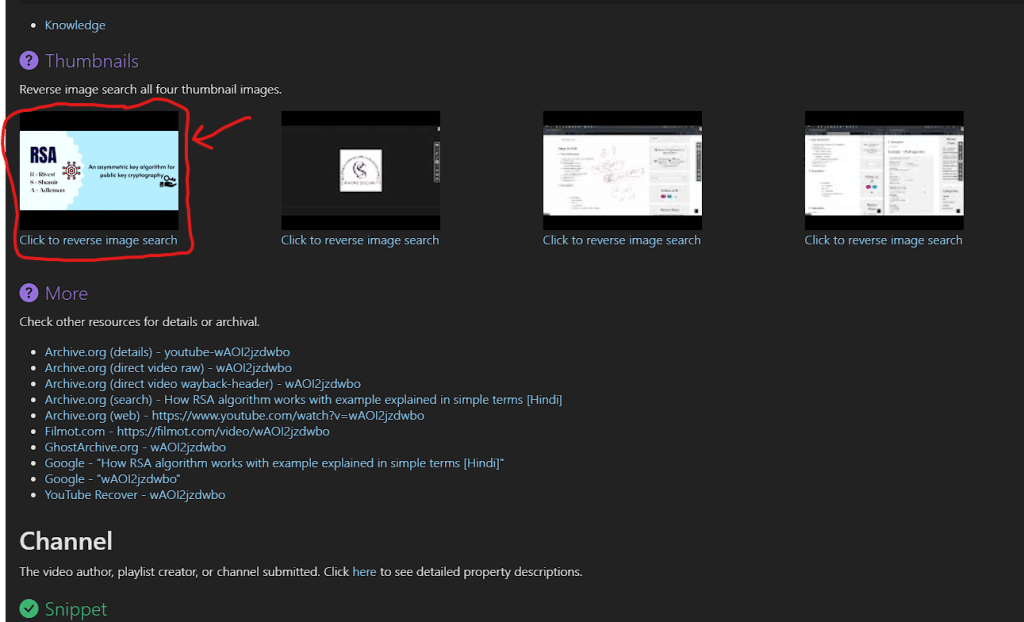
after clicking on the reverse image search link a new tab will appear and results for the same will show up.
List of Other Video Search Engines:-
List of reverse image search tools
Footprinting through FTP search engines
FTP File Transfer Protocol search engine is usually used for searching files that are kept over any FTP server. This search engine indexes the files of FTP servers, files may contain valuable information about the target organization.
Most companies like institutions, industries, and universities use FTP servers for keeping their large files and shared applications among their employees for better reachability.
Sometimes FTP search engines can deliver some critical information about our target from their FTP server’s files.
Information can contain valuable data like employees’ personal records, financial records, tax documents, business strategies, licensed software information, and other critical information about the target organization.
FTP search Engines:-
Let’s See an example of using the FreewareWeb FTP File search engine
First, go to the search engine website and then search for your target organization domain. As an example, I’m searching for Microsoft organization
Now this is the result i got after this we need to analyze what information is helpful for us and what are the garbage information in the search
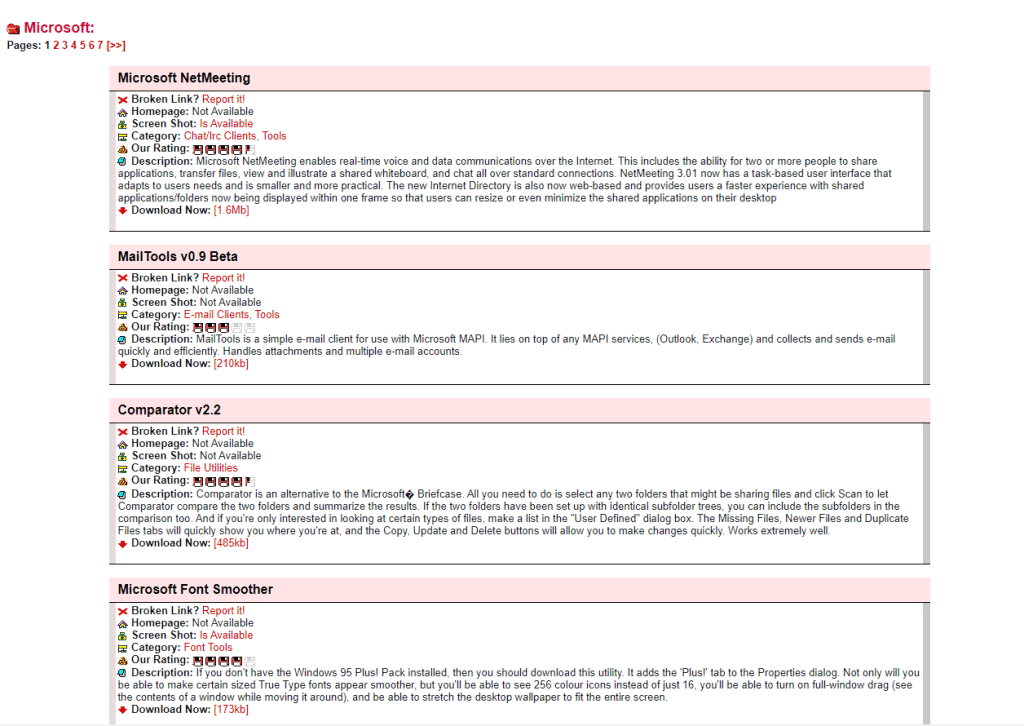
sometimes you will get many critical information and files that are not to be disclosed publicly.
Footprinting through IoT Search Engine
IoT Internet of Things search engines crawls the IoT devices that are publicly accessible over the internet. IoT search engines can crawl and provide much crucial information about IoT devices.
Crucial Information may contain control of SCADA (Supervisory Control and Data Acquisition) systems, Internet-connected household appliances, traffic control systems, industrial appliances, CCTV cameras, Automatic doors, automated devices, etc.
IoT search engines:-
Let’s try IoT search Engine Shodan with a target organization microsoft.com
First, open the Shodan search engine from the above link and then search for your target organization, and it will show much crucial information about your target.
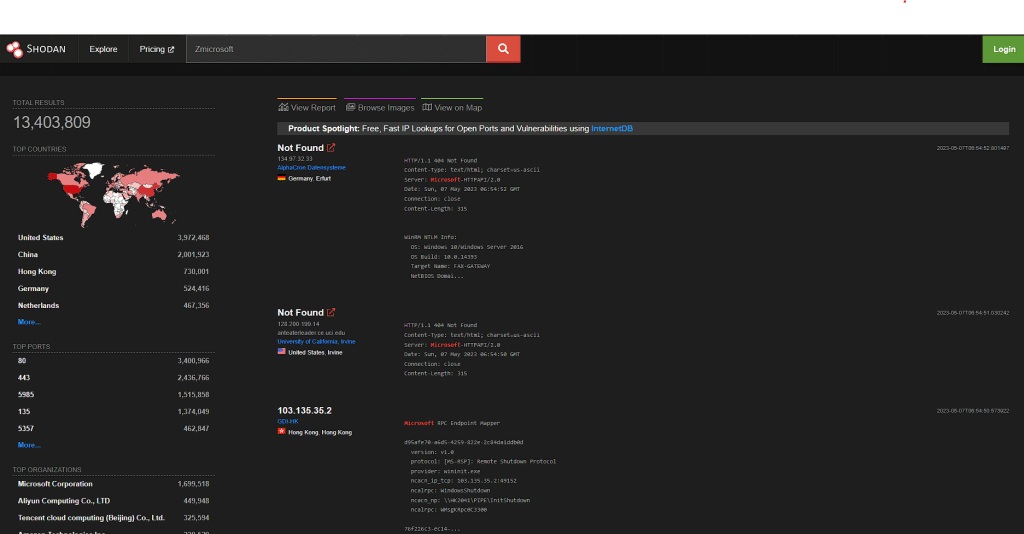
analyze the search result for any vulnerable IoT devices related to your target organization in various countries. This will help you to gather information about vulnerable IoT devices in your victim’s network.