Table of Contents
ToggleHey everyone, today in this article we are going to discuss what is the diamond model of intrusion analysis what are the real-life scenarios where this will use
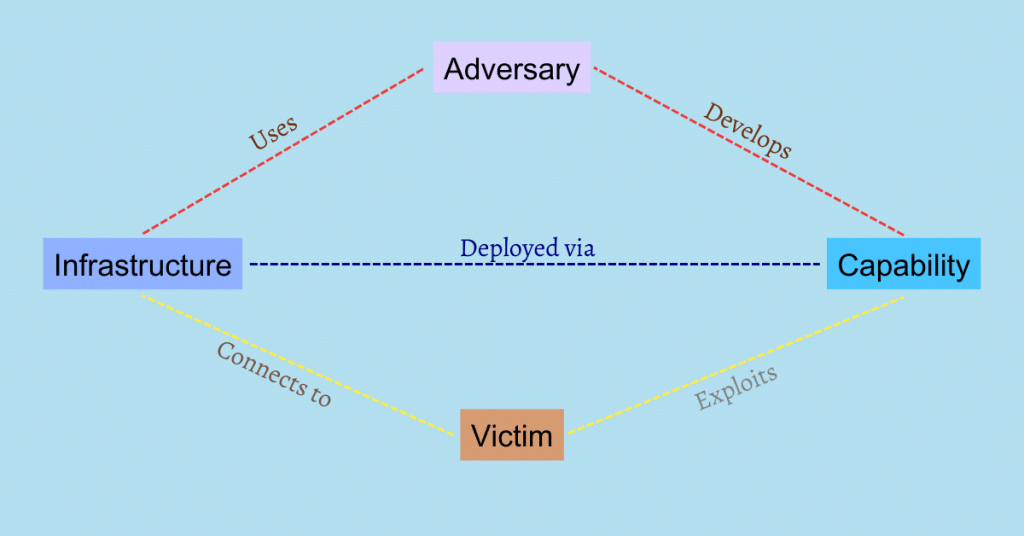
Show basically a diamond model of intrusion analysis is a cyber security framework developed by an expert analyst For better responding to a cyber threat.
This model consists of 4 key components in it or notes that are interconnected in a diamond-shaped model:-
- Adversary/attacker
- Infrastructure
- Victim
- Capability
Diamond Model of Intrusion Analysis
So the diamond model is a cyber security framework developed by an expert analyst for introducing state-of-the-art technology for intrusion analysis.
This model gives a framework and set of procedures for recognizing clusters of event data correlated on any organization’s systems.
It determines the vital atomic element that occurs in any intrusion activity and is referred to as the diamond event
Here the analyst can identify the events and connect them as activity threads for obtaining information regarding how and what transpired during an attack. the analyst can also easily identify whether any data are required by examining the missing feature.
it also offers a method or route map for analyzing incidents related to any malicious activity and predicting the possibility of an attack.
With this model, an analyst can develop more advanced and efficient mitigation approaches and analytic efficiency can be increased. this will result in cost savings for the defender and rising costs for the attacker.
This model is named a diamond model because when all the features are arranged according to the relationship between them, it forms a diamond-shaped structure. Although it appears to be a simple approach, it is rather complex and requires high expertise and skills to traceroute the flow of attack.
Essential Features of Diamond Model
There are 4 main essential features of diamond events in the diamond model of intrusion analysis:-
- Adversary/attacker
- Victim
- Capability
- Infrastructure
Let’s discuss these features in brief:
Adversary/attacker
This is the first node in the diamond model that represents the attacker or adversary, this will also include information about their capabilities motivations, and goals.
The attacker takes advantage of the capabilities against the victim to perform a malicious activity for financial benefit or to damage the reputation of the victims. An adversary can be individuals such as companies insiders or a competitor organization.
An attacker can use many techniques to gain information such as email addresses or network assets and attempt to attack any application used in smartphones to gain sensitive information.
Victim
The victim refers to the target that has been exploited or the network environment where the attack is going to be performed.
The Attacker exploits the vulnerabilities or security loopholes in the victim’s infrastructure by using their resources.
The victim can be any person, organization, institution, or even network information such as IP addresses, domain names, email addresses, and sensitive personal information of an individual.
Capability
This is the third node in the diamond model that represents the strategy used by the attacker including the tools, tactics, and techniques they used to carry out the attack.
Also, capabilities refer to all strategies, methods, and procedures associated with an attack.
It can also be a malware or tool used by an adversary against the target. Capability includes simple and complex attack techniques such as brute-forcing and ransomware attacks.
Infrastructure
The infrastructure is the 4th node in the diamond model that represents the infrastructure used by the attacker to perform the attack which includes the tools tactics and techniques they used to carry out the attack.
Here the infrastructure refers to the hardware or software used in the network by the target that has a connection with the attacker.
it refers to what the attacker has used to reach the victim’s network or system for performing the attacks.
For example:- Consider an organization having an email server in which all the data regarding employees’ email IDs and other personal details are stored.
The attacker can use the server as infrastructure to perform any type of attack by targeting a single employee which can be also said as social engineering attack.
Exploiting infrastructure leads to data leakage and data exfiltration.
Additional Event Meta-features
In the Diamond Model, an event contains some basic meta-features that provide additional information such as the time and source of the event.
These meta-features help in linking related events, making it easier and faster for analysts to trace an attack.
The following below are the features that help in connecting related events:-
- Timestamp
- Phase
- Result
- Direction
- Methodology
- Resources
Timestamp
This feature can reveal the time and date of an event. It is important as it can indicate the beginning and end of the event. It also helps in analyzing and determining the periodicity of the event.
Phase
The phase helps in determining the progress of an attack or any malicious activity. The different phases of an attack include the phases used in the cyber kill chain framework: reconnaissance, weaponization, delivery, exploitation, etc.
Results
The result is the outcome of any event. For example, the result of an attack can be a success, failure, or unknown. It can also be segregated using security fundamentals such as confidentiality(C) compromised, integrity(I) compromised, and availability(A) compromised. CIA Compromised.
Direction
This feature refers to the direction of the attack. For instance, the direction can indicate how the adversary was routed to the victim. This feature can be immensely helpful when describing network-based and host-based events. The possible values for this feature include victim to infrastructure, an adversary to infrastructure, infrastructure to infrastructure, and bidirectional.
Methodology
The methodology refers to any technique that is used by the adversary to perform an attack. This feature allows the analyst to define the overall class of action performed. Some attack techniques are spear-phishing emails, distributed denial-of-service (DDoS) attacks, content delivery attacks, and drive-by-compromise.
Resource
Resource feature entails the use of external resources like tools or technology used to perform the attack. It includes hardware, software, access, knowledge, data, etc.
Extended Diamond Model
The extended diamond model comes with some extra features that include socio-political meta-features to determine the relationship between the attacker and victim as well as technology meta-features for infrastructure and capabilities.
Socio-political meta-feature
These features can be useful for describing the relationship between the attacker and the victim. It can also help in determining the goal or motivation of the attacker: some common motivation includes financial benefit, corporate espionage, and hacktivism.
Technology Meta-features
These feature useful when describing the relationship between the infrastructure and capability. This meta-feature describes how technology can enable both infrastructure and capability for communication and operation. It can also be used to analyze the technology used in an organization to identify any malicious activity.