Hello everyone Lucifer 😉 with a very interesting topic which is the working of the DES algorithm. In this article, we will see how DES works and what are steps in the DES algorithm.
The Data Encryption Standard (DES) is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST) in 1975 as Federal Information Processing Standards (FIPS) 46 in the Federal Register and standardized in January 1977.
The proposed DES was first published on 17 March 1975 in the Federal Register, and it was approved in 1976 as a Federal Standard.
In DES for encryption, we give input of 64-bit plaintext and create a 64-bit ciphertext. For Decryption, it takes 64-bit ciphertext and creates a 64-bit block of plaintext. The same 56-bit secret key will be used for both encryption and decryption.
Steps in how the DES algorithm works
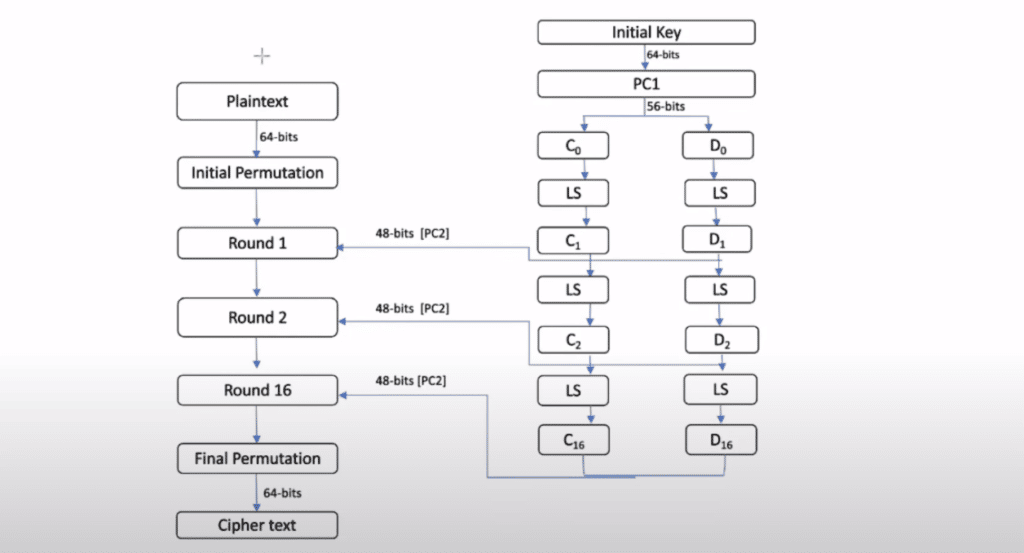
- We give 64-bit plaintext
- 64-bit plaintext goes to Initial Permutation (IP)
- In Initial Permutation there are rearranging of bits and gives an output of 64 bits of text.
- Now, the output of IP goes to Round 1 and there is a total of 16 Rounds.
- In Round 1 there are two things going, first 64-bit Initial Permutation and 48-bit Initial key.
- Then the output of round 1 goes to round 2, then the second round output goes to the third, and so on to round 16.
- Now, the output of round 16 goes to the Final Permutation
- Final permutation- Inverse of initial permutation
- The output of the final permutation gives our 64-bits ciphertext
Logic Behind Initial Key
- We take 64 bits of key, which is known as the Initial key.
- Now, 64 bits’ initial key goes to PC1, which converts into 56 bits.
- In PC1 there are only 56 bits of key but where 8 bits are gone, the 8 bits are eliminated or discarded.
- Now 56-bit PC1 is divided into two parts C0 and D0 which have 28-bits each respectively.
- Now, C0 and D0 go to LS (left shift) for shifting bits.
- Bits shift works on the principle of even or odd rounds if rounds are 1, 2, 9, 16, then it shifts 1 bit if rounds are 3, 4, 5, 6, 7, 8, 10, 11, 12, 13, 14, 15, then it shifts 2 bits.
- After the left shift (LS), shifted bits go to C1 and D1
- Then C₁ and D₁ go to PC2.
- But C₁ and D₁ is having 56-bits, and we want only 48-bits, so we wisely choose only 48-bits from 56-bits and leave the rest of them
- then 48-bits PC2 goes to round 1.
The whole shifting and the key process will be repeated till round 16. Every time the Input changes to like C₂—C3—- —C16 and D2—-D3— —D16
A detailed structure of Encryption Rounds
The 64-bit IP was further divided into two parts, Left (L) And Right (R) in which both are 32 bits each.
- 32-bit right plaintext goes to expansion permutation for converting 32-bits to 48-bits.
- Now, 48 bits of expansion permutation and 48 bits of initial key get together for XOR Operation.
- Now, the output from the 48-bit XOR operation will be going to the s-box (substitution) and give an output of
32-bits by eliminating 16-bits.
• S-Box, we make a total of 8 s-box, all having 6-bit input and giving 4-bit output. So total output is
8×4=32-bits - Output from S-Box 32-bits goes to permutation and then carried out to the next one.
- Now, 32 bits from permutation and 32 bits from left plaintext get together for XOR operation.
- Then we got the right plaintext and left plaintext, but the left plaintext is carried from the right plaintext of 32-bits
from the upper side.
Advantages and disadvantages of DES
Advantages:
- Fast and efficient
- Relatively simple to implement
- It is well-studied and widely analyzed
Disadvantages:
- The short key length makes it vulnerable to brute-force attacks
- Vulnerable to certain types of cryptanalytic attacks
- No longer considered secure for most applications
Breaking of DES
| Step | Description |
| 1 | A brute force attack is used to try all possible combinations of keys to decrypt the encrypted message. |
| 2 | Each key is used to encrypt a known plaintext message and the resulting ciphertext is compared to the original ciphertext. |
| 3 | If the resulting ciphertext matches the original ciphertext, the key used is the correct key and the message can be decrypted. |
| 4 | If all possible keys have been tried and no match is found, the DES algorithm has been successfully broken |
Uses of DES
- Encrypting sensitive data, such as financial or personal information.
- Securely transmitting data over the internet or other communication networks.
- Storing encrypted data in databases or other storage systems.
- Authenticating users or devices in a networked environment.
- Protecting against unauthorized access or tampering with data.
If you have any queries regarding the above content, or you want to update anything in the content, then contact us with your queries. You can directly post your question in the group.
Connect with us on these platforms