Introduction
LDAP, which stands for Lightweight Directory Access Protocol, is a widely used protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. LDAP enables organizations to manage users centrally, as well as groups and other directory information, often used for authentication and authorization purposes in web and internal applications.
Objectives
- Provide a thorough understanding of LDAP and its role in directory services.
- Explore the LDAP tree structure and its key components.
- Introduce LDAP Injection, its impact, and how it can be exploited.
- Equip participants with the knowledge and skills to identify and mitigate LDAP Injection vulnerabilities.
Pre-requisites
- A foundational understanding of how directory services work, particularly LDAP.
- Basic knowledge of web application security principles and common vulnerabilities.
- Familiarity with the structure and components of LDAP, such as Distinguished Names (DNs) and attributes.
- Experience with tools and techniques for security testing of web applications, such as OWASP ZAP or Burp Suite.
Task 2: Structure
In LDAP, directory entries are structured as objects, each adhering to a specific schema that defines the rules and attributes applicable to the object. This object-oriented approach ensures consistency and governs how objects like users or groups can be represented and manipulated within the directory.
Services that use LDAP:
- Microsoft Active Directory: A service for Windows domain networks, utilizing LDAP as part of its underlying protocol suite to manage domain resources.
- OpenLDAP: An open-source implementation of LDAP, widely used for managing user information and supporting authentication mechanisms across various platforms.
LDIF Format
LDAP entries can be represented using the LDAP Data Interchange Format (LDIF), a standard plain text data format for representing LDAP directory entries and update operations. LDIF imports and exports directory contents and describes directory modifications such as adding, modifying, or deleting entries.
Structure
An LDAP directory follows a hierarchical structure like a file system’s tree. This structure comprises various entries representing a unique item, such as a user, group, or resource.
At the top of the LDAP tree, we find the top-level domain (TLD), such as dc=ldap,dc=thm. Beneath the TLD, there may be subdomains or organizational units (OUs), such as ou=people or ou=groups, which further categorize the directory entries.
- Distinguished Names (DNs): Serve as unique identifiers for each entry in the directory, specifying the path from the top of the LDAP tree to the entry, for example,
cn=John Doe,ou=people,dc=example,dc=com. - Relative Distinguished Names (RDNs): Represent individual levels within the directory hierarchy, such as
cn=John Doe, wherecnstands for Common Name. - Attributes: Define the properties of directory entries, like
mail=john@example.comfor an email address.
Question: Read the task above.
Answer: No Answer Needed
Task 3: Search Queries
Example:
user@tryhackme$ ldapsearch -x -H ldap://10.201.97.40:389 -b "dc=ldap,dc=thm" "(ou=People)"
# extended LDIF
#
# LDAPv3
# base <dc=ldap,dc=thm> with scope subtree
# filter: (ou=People)
# requesting: ALL
#
# People, ldap.thm
dn: ou=People,dc=ldap,dc=thm
objectClass: organizationalUnit
objectClass: top
ou: People
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
┌──(luci㉿kali)-[~]
└─$ ldapsearch -x -H ldap://10.201.97.40:389 -b "dc=ldap,dc=thm" "(cn=Jo*)"
# extended LDIF
#
# LDAPv3
# base <dc=ldap,dc=thm> with scope subtree
# filter: (cn=Jo*)
# requesting: ALL
#
# john.doe, People, ldap.thm
dn: uid=john.doe,ou=People,dc=ldap,dc=thm
objectClass: inetOrgPerson
objectClass: top
cn: John Doe
sn: Doe
uid: john.doe
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1Question: Read the task above.
Answer: No Answer Needed
Task 4: Injection Fundamentals
Injection Fundamentals
LDAP Injection is a critical security vulnerability that occurs when user input is not properly sanitized before being incorporated into LDAP queries. This oversight allows attackers to manipulate these queries, leading to unauthorized access or manipulation of the LDAP directory data.
LDAP Injection exploits the way web applications construct LDAP queries. When user input is directly included in these queries without proper validation or encoding, attackers can inject malicious LDAP statements. This can result in unauthorized access to sensitive information, modification of directory data, or bypassing authentication mechanisms.
The process is analogous to SQL Injection, where malicious SQL statements are injected into queries to manipulate database operations. In LDAP Injection, the malicious code targets LDAP queries instead.
Common Attack Vectors
- Authentication Bypass: Modifying LDAP authentication queries to log in as another user without knowing their password.
- Unauthorized Data Access: Altering LDAP search queries to retrieve sensitive information not intended for the attacker’s access.
- Data Manipulation: Injecting queries that modify the LDAP directory, such as adding or modifying user attributes.
Injection Process
Making an LDAP Injection attack involves several key steps, from identifying the injection point to successfully exploiting the vulnerability.
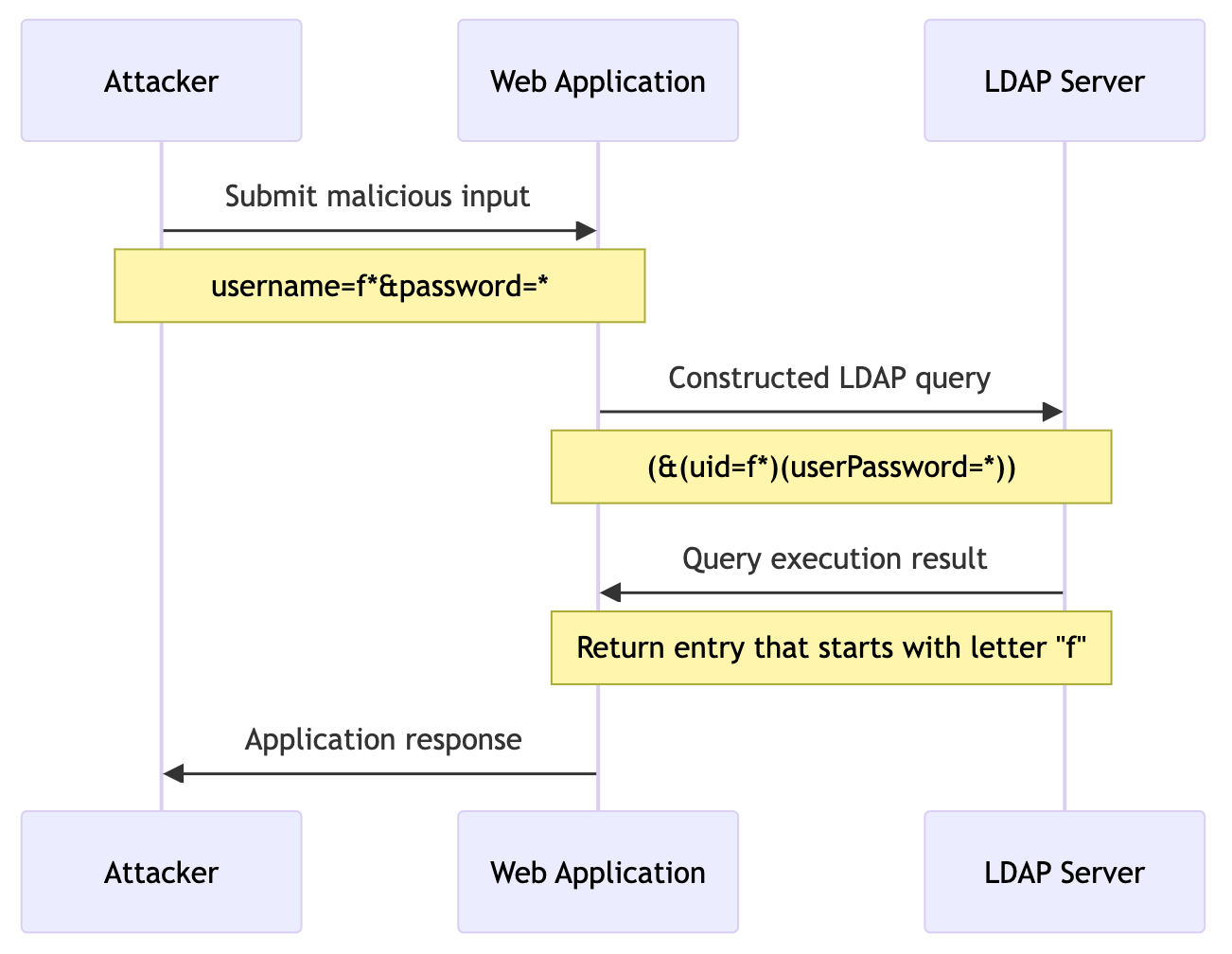
This diagram illustrates the interaction between the attacker, the web application, and the LDAP server during an LDAP Injection attack. The attacker submits malicious input to the web application login form, which constructs an LDAP query incorporating this input. The LDAP server then executes the altered query, leading to potential unauthorized access or information disclosure, depending on the nature of the injected payload.
Question: Read the task above.
Answer: No Answer Needed
Task 5: Exploiting LDAP
To demonstrate a simple LDAP Injection attack, go to http://10.201.97.40/normal.php. Based on the code above, the application constructs an LDAP query for authentication based on user input without proper sanitisation.
An attacker can exploit this by submitting a username and password with a character the application does not anticipate, such as an asterisk (*) for the uid and userPassword attribute value. This makes the condition always evaluates to true, effectively bypassing the password check:
Injected Username and Password:
username=*&password=*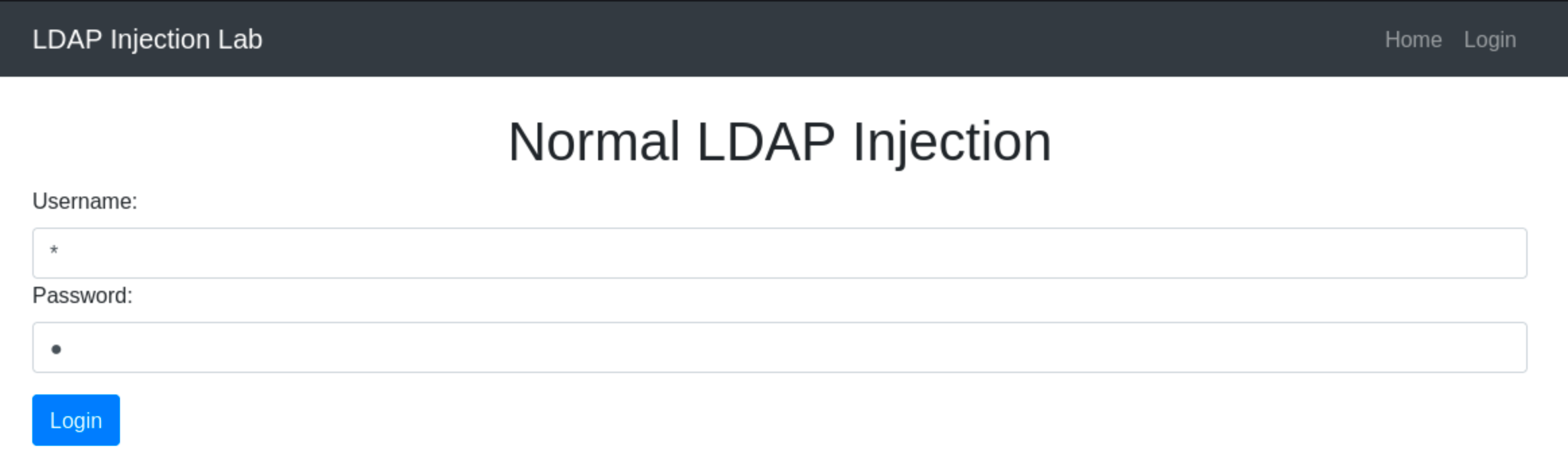
Resulting LDAP Query Component:
(&(uid=*)(userPassword=*))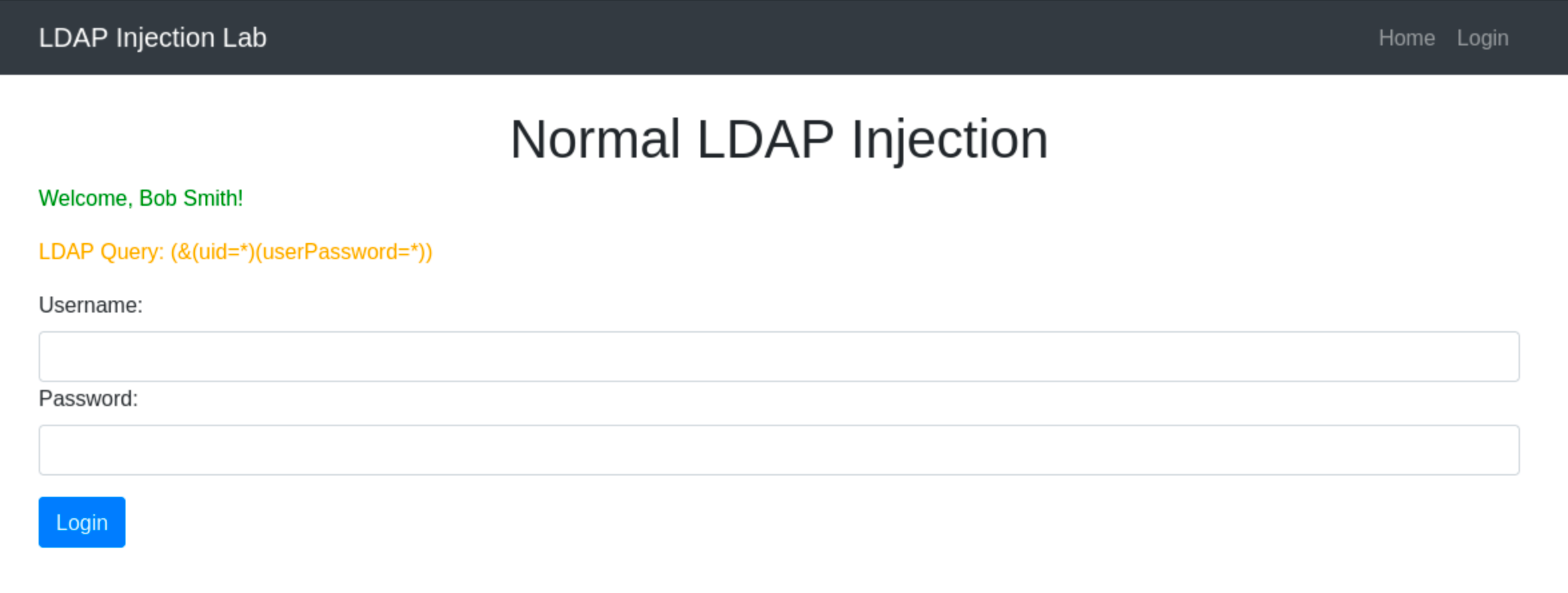
This injection always makes the LDAP query’s condition true. However, using just the * will always fetch the first result in the query. To target the data beginning in a specific character, an attacker can use a payload like f*, which searches for a uid that begins with the letter f.
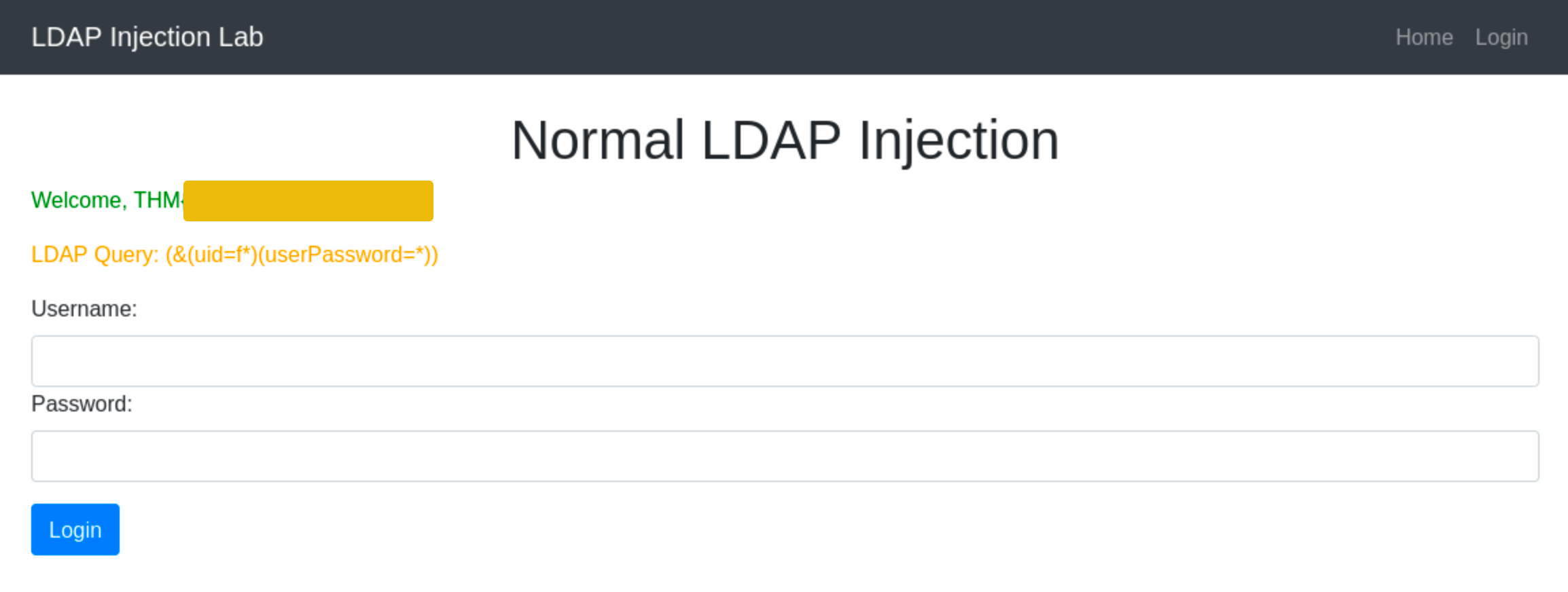
Question: What is the flag?
Query: username: f* and password: *
Answer: THM{!b451c_ld4p_inj3ct1ON!}!
Task 6: Blind LDAP Injection
Blind LDAP Injection
Blind LDAP Injection is a more subtle variant of LDAP Injection, where the attacker doesn’t receive direct output from the injected payload. Instead, they must infer information based on the application’s behaviour. This type of attack is more challenging but can still be used to extract sensitive information from an LDAP directory.
Blind LDAP Injection requires a different approach due to the lack of explicit query results. Attackers must rely on indirect signs, such as changes in application behaviour, error messages, or response timings, to deduce the structure of the LDAP query and the existence of vulnerabilities.
For example, below is the code snippet of http://10.201.97.40/blind.php that uses an LDAP query to check for the existence of a user but only returns a generic error message on failure. The application also checks if the submitted email is the same as the email in the database:
Question: Read the task above.
Answer: No Answer Needed
Task 7: Automating the Exploitation
Exploit Code
To automate the exfiltration of data in the previous task, you can use the Python script below:
Use the final payload to log in to http://10.201.97.40/login.php. Make sure to use * as the password; this will automatically evaluate the search query as true.
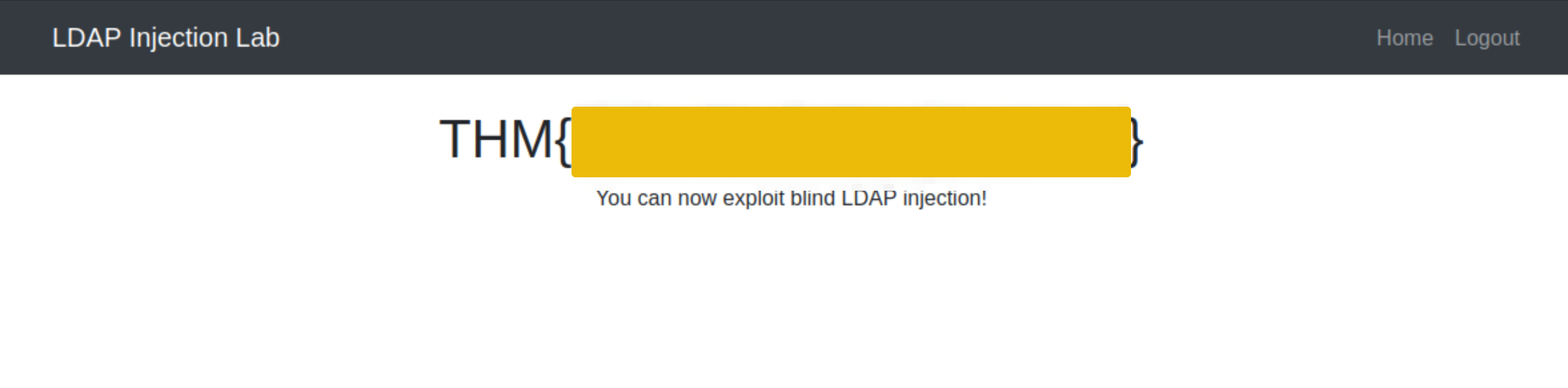
Question: What is the flag in the dashboard?
Run script and get the username and put password as *
Answer:THM{!!bl1nDLd4P1nj3ct10n!!}
Task 8: Conclusion
Conclusion
Congratulations on completing LDAP Injection! Here’s a recap of the key concepts we’ve covered:
- LDAP Fundamentals: We started by understanding LDAP’s role in directory services and learning about the structure of an LDAP tree, including DNs, RDNs, and attributes.
- LDAP Search Queries: You’ve learned how to construct basic LDAP search queries, understanding the importance of filters and their syntax.
- LDAP Injection Fundamentals: You’ve learned what LDAP Injection is, how it works, and common attack vectors, highlighting the risks associated with improperly sanitized input in LDAP queries.
- Exploiting LDAP Injection in Login Mechanisms: Techniques for bypassing authentication through LDAP Injection and practical exercises simulating vulnerable login systems were explored.
- Blind LDAP Injection Techniques: The challenges and methodologies for extracting information through Blind LDAP Injection, a subtler form of LDAP Injection, were discussed.
Additional Resources
To continue your journey in mastering LDAP and related security concepts, consider exploring the following resources:
- TryHackMe: Breaching AD: This room provides an in-depth look into Active Directory environments, offering practical experiences in exploiting common AD vulnerabilities and understanding the security mechanisms within AD.
Question: I can now exploit LDAP Injection vulnerabilities!
Answer: No Answer Needed
If there is any query please feel free to contact us: Contact
Thank you for reading this post, don't forget to subscribe!